.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Security teams today face a massive flood of digital noise. If you've ever worked in a Security Operations Center (SOC), you know the feeling of drowning in alerts. It's like trying to hear a whisper in a crowded stadium. This is exactly where the debate of SIEM vs SOAR begins.
SIEM (Security Information and Event Management) is a software solution that aggregates log data from across your network to provide real-time analysis and security alerts. SOAR (Security Orchestration, Automation, and Response) is a stack of compatible software programs that allow an organization to collect data about security threats and respond to low-level security events without human assistance.
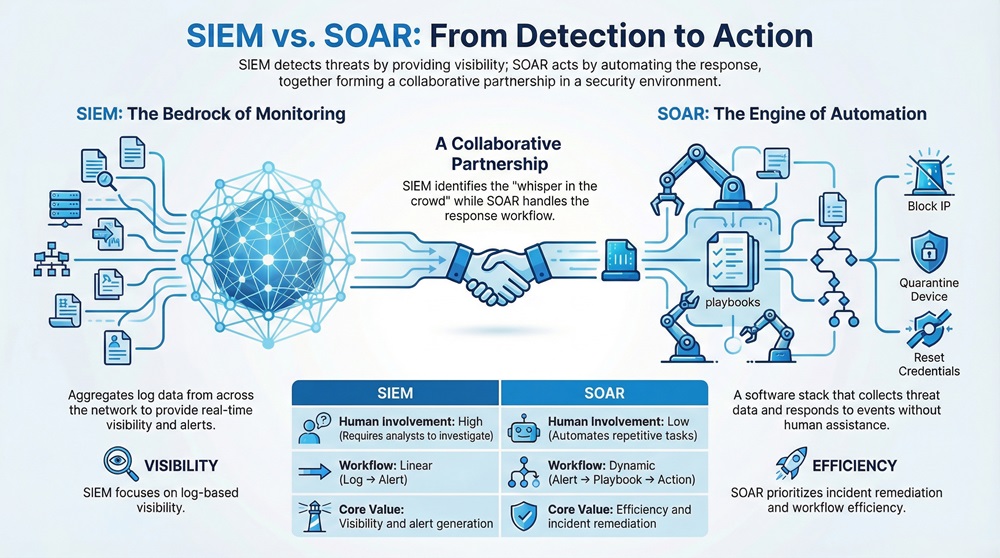
To be honest, many people think these two tools are rivals. In my experience, that’s a misconception. They aren't competing for the same job; they're more like a detective and a rapid-response team working the same case. But which one does your business actually need right now?
| Basis for Comparison | SIEM | SOAR |
|---|---|---|
| Primary Function | Data collection and log management | Threat response and workflow automation |
| Core Value | Visibility and alert generation | Efficiency and incident remediation |
| Input Source | Diverse logs (firewalls, servers, apps) | SIEM alerts and external threat intel |
| Human Involvement | High (requires analysts to investigate) | Low (automates repetitive tasks) |
| Data Handling | Ingests massive volumes of raw data | Focuses on actionable intelligence |
| Workflow | Linear (Log → Alert) | Dynamic (Alert → Playbook → Action) |
SIEM is the bedrock of modern security monitoring. It acts as a central repository for every digital footprint in your company. It gathers logs from your antivirus, your cloud servers, and even your employee logins.
SIEM technology supports threat detection, compliance, and security incident management. It looks for patterns. For instance, if someone tries to log in from New York and then two minutes later from Tokyo, the SIEM flags it.
The system works by using "correlation rules." You tell the system: "If X and Y happen together, tell me." It’s fantastic for compliance because it keeps a perfect record of everything. However, the downside is "alert fatigue." If your rules are too sensitive, your team gets thousands of notifications a day. How can a human possibly check them all?
Also Read: What is a Wide Area Network (WAN)? Architecture & Types Explained
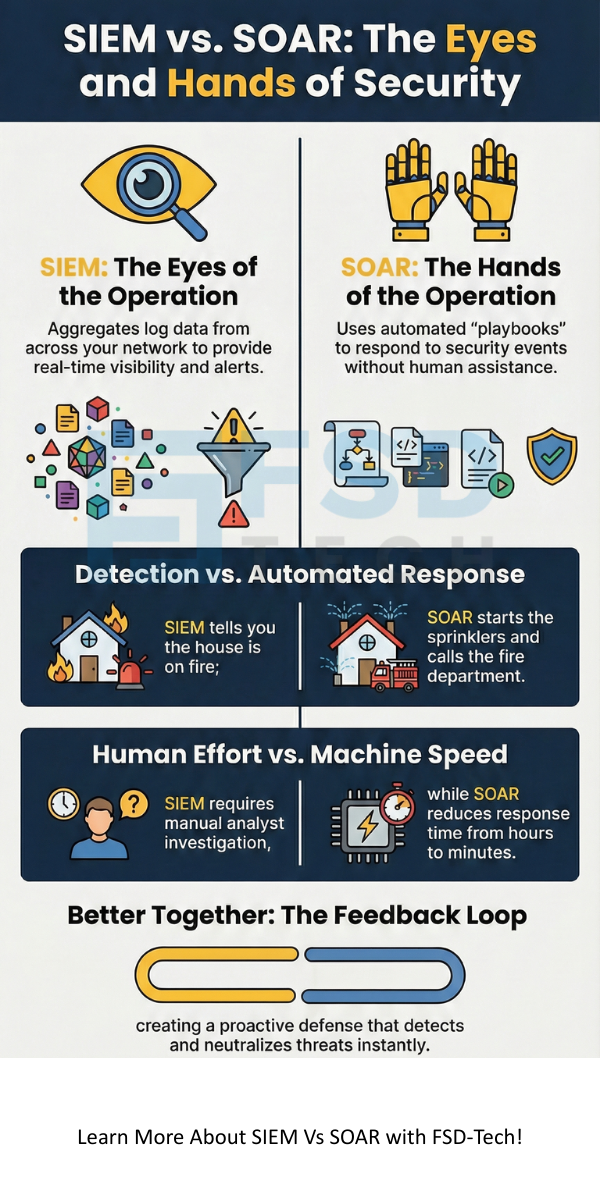
If SIEM is the eyes of your operation, SOAR is the hands. It takes the "What now?" out of the equation. SOAR platforms take the alerts generated by your SIEM (or other tools) and run them through a "playbook."
A playbook is essentially a digital "if-then" chart. For example, if an alert says a user's laptop has malware, the SOAR tool can automatically isolate that laptop from the network, scan the file, and email the IT manager—all in seconds.
The magic of SOAR lies in its ability to integrate with other tools. It uses APIs to "talk" to your firewall, your email server, and your endpoint protection. In my time consulting for mid-sized firms, I've seen SOAR reduce the time to contain a threat from hours down to literal minutes.
The points given below explains the difference between SIEM vs SOAR in detail:
Also Read: What is Bandwidth? | Types, Working, and Network Capacity Explained
One may wonder: "If SOAR is so smart, do I even need SIEM?" Here's the thing—SOAR needs a feed to work. Without a SIEM, your SOAR doesn't know what's happening across your entire infrastructure. It would be like having a world-class surgeon but no diagnostic equipment.
In a mature security setup, these two tools form a loop. The SIEM detects a suspicious login. It sends that alert to the SOAR. The SOAR checks the user’s location and realizes it’s a breach. It then tells the SIEM to look for other logs from that same IP address across the whole network.
The combination of these technologies allows for a "proactive" rather than "reactive" stance. Isn't it better to stop a hacker at the door rather than cleaning up after they've left?
Advantages of SIEM
Disadvantages of SIEM
Advantages of SOAR
Disadvantages of SOAR
At the end of the day, the SIEM vs SOAR debate comes down to your team's maturity. If you don't know what's happening on your network, get a SIEM. If you know exactly what's happening but you're too busy to fix it all, you need a SOAR.
In my experience, the most successful companies are the ones that stop looking for a "magic bullet" and start building a layered defense. Your security team deserves tools that make their lives easier, not harder. We are committed to helping you find that balance, ensuring your data stays safe while your team stays sane.
Not really. While some SOAR tools are adding log features, they aren't designed to hold the massive amounts of historical data that a SIEM manages. You’d be losing your "memory" if you switched entirely.
It varies. SIEM is usually priced by data volume (GB/day), while SOAR is often priced by the number of "actions" or "users." Generally, SOAR is seen as an investment to save money on hiring more analysts.
Yes, it can be. You need to have your security processes documented before you can automate them. If your current process is messy, automating it just makes the mess happen faster!

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts