.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

PCI compliance is something you've probably heard of if you've ever processed a credit card payment. But let’s be honest, for most business owners, it feels like a massive wall of technical jargon and red tape. Have you ever wondered why some companies seem to handle data breaches with grace while others face millions in fines? The secret usually lies in how they handle their PCI compliance standards.
Here is the thing: PCI compliance isn't just a "nice to have" badge for your website. It is a rigorous security standard designed to protect the very lifeblood of your business—your customers' payment data. To be honest, in my experience, many people wait until an audit or a breach to take this seriously. By then, it’s usually too late.
What exactly goes into staying compliant? Is it just about having a strong password, or is there more to the story? Let’s break down what PCI compliance actually means for you and your team.
| Basis for Comparison | Level 1 | Level 2 | Level 3 | Level 4 |
|---|---|---|---|---|
| Transaction Volume | Over 6 Million/Year | 1 to 6 Million/Year | 20,000 to 1 Million/Year | Less than 20,000/Year |
| Audit Requirement | Annual Report (ROC) | Annual SAQ | Annual SAQ | Annual SAQ |
| Internal Scan | Required Quarterly | Required Quarterly | Required Quarterly | Required Quarterly |
| External Scan | ASV Required | ASV Required | ASV Required | ASV Required |
| Attestation | AOC Required | AOC Required | AOC Required | AOC Required |
Definition: PCI compliance is a set of security standards formed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. It is governed by the Payment Card Industry Security Standards Council (PCI SSC), an independent body created by major card brands like Visa, Mastercard, and American Express.
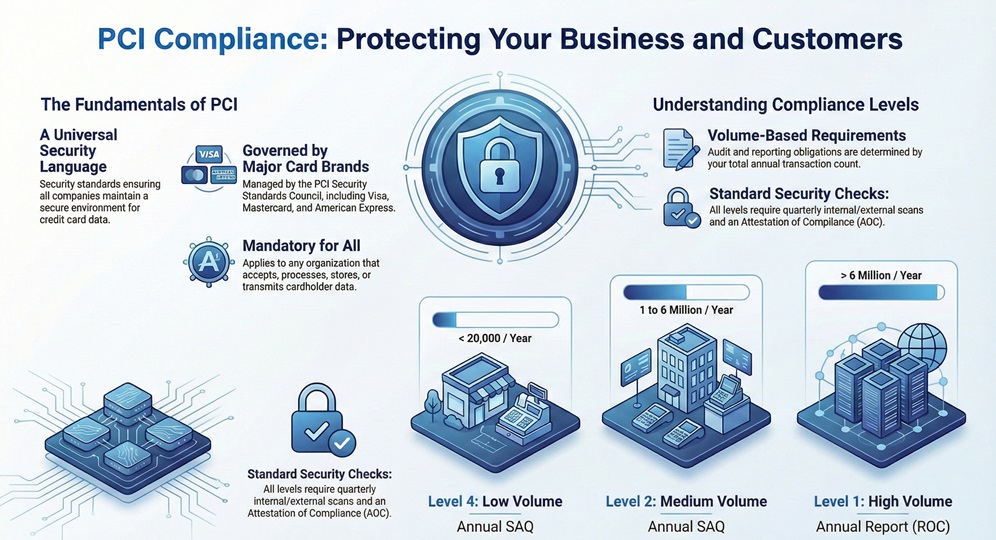
You can think of PCI compliance as a universal language for payment security. It ensures that whether a customer buys a coffee in London or a laptop in New York, their data is handled with the same level of care. PCI compliance applies to any organization, regardless of size or number of transactions, that touches cardholder data (CHD).
Now, you might ask, "Why should I care about PCI compliance if I'm a small business?" In my experience, the cost of non-compliance far outweighs the investment in security. When you maintain PCI compliance, you aren't just checking a box for the bank; you're building a wall around your reputation.
Data breaches are incredibly expensive. Between legal fees, forensic investigations, and the inevitable loss of customer trust, a single leak can end a business. PCI compliance provides a proven roadmap to prevent these disasters. Furthermore, card brands can levy heavy fines against banks that work with non-compliant merchants, and those costs are always passed down to you.
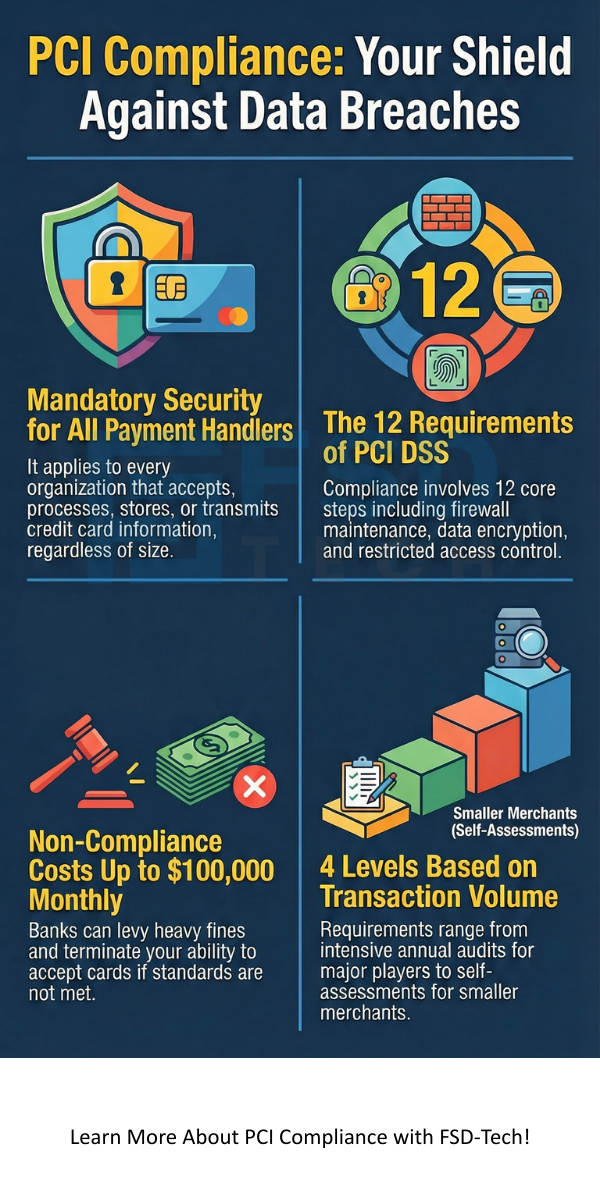
To achieve PCI compliance, you must adhere to the Payment Card Industry Data Security Standard (PCI DSS). These are broken down into six main goals and 12 specific requirements.
Build and Maintain a Secure Network
Protect Cardholder Data
Maintain a Vulnerability Management Program
Implement Strong Access Control Measures
Regularly Monitor and Test Networks
Maintain an Information Security Policy
Also Read: Authentication Authorization and Accounting (AAA)
PCI compliance isn't a one-size-fits-all approach. The "levels" are determined by your transaction volume over a 12-month period.
Level 1 is for the big players—merchants processing over 6 million transactions annually. These businesses must undergo an annual on-site assessment by a Qualified Security Assessor (QSA).
Levels 2, 3, and 4 generally involve smaller volumes. Instead of a full on-site audit, these merchants usually complete a Self-Assessment Questionnaire (SAQ). However, don't let the word "self-assessment" fool you. You are still legally obligated to be truthful and ensure your systems meet the PCI compliance requirements.
Let’s be honest: reaching PCI compliance is hard work. In my experience, the biggest hurdle is "scope creep." This happens when your cardholder data environment (CDE) expands because you’ve added new software or hardware without segmenting your network.
Another challenge is documentation. Many businesses do the work but fail to keep the records. If you can't prove you ran a scan six months ago, as far as an auditor is concerned, it never happened. Maintaining PCI compliance requires a disciplined approach to record-keeping.
Also Read: What is Cloud Access Security Broker (CASB)?
To keep your PCI compliance status healthy, you should move from "compliance as an event" to "compliance as a habit." Here are a few tips:
At the end of the day, PCI compliance is about one thing: integrity. It shows your customers that you value their privacy and their hard-earned money. Here at our firm, we believe that security should never be an afterthought.
We focus on helping clients navigate these complex waters with ease, ensuring that your data stays safe so you can focus on growing your business. Staying compliant is a journey, not a destination. Are you ready to take the next step in securing your future?
Secure your payments now. Speak with a specialist.
Yes. Even if you use a third-party processor like PayPal or Stripe, you are still responsible for ensuring that the way you integrate those services is secure. You still have a small amount of PCI compliance paperwork to handle (usually SAQ A).
If you are found non-compliant, you could face monthly fines ranging from $5,000 to $100,000. Additionally, your bank might terminate your ability to accept credit cards entirely.
You must validate your PCI compliance annually. However, certain requirements, like network scanning, must be performed every quarter.
Technically, it is not a federal law in the United States, but it is a contractual requirement by the card brands. However, some states (like Nevada and Washington) have incorporated PCI DSS into their state laws.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts