.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Breach and Attack Simulation is a smart way for companies to test their digital defenses by mimicking the moves of real hackers. Have you ever wondered if your expensive firewall actually works when a real threat hits? Many leaders feel safe because they bought the best tools, but they don't know if those tools are set up right. This is where BAS comes in. It acts like a persistent, friendly intruder that pokes at your doors and windows 24/7.
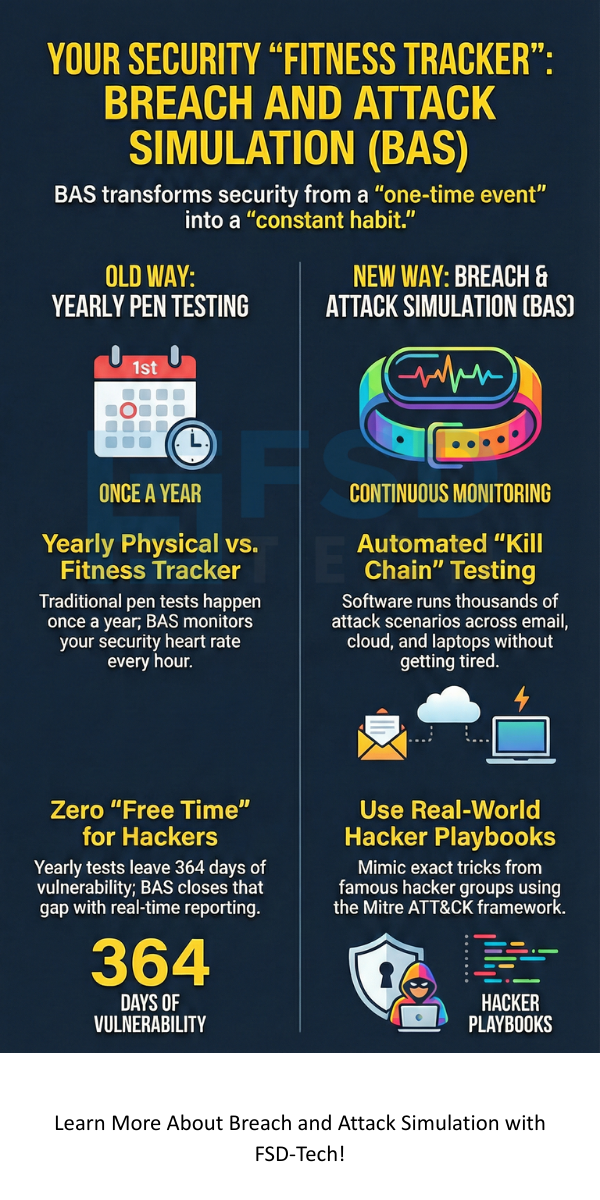
To be honest, the old way of checking security is failing. We used to rely on a "pen test" once a year. But a year is a lifetime in tech. If a hacker finds a new hole the day after your test, you’re in trouble. BAS changes the game by making testing constant. It helps you see your network through the eyes of an attacker without actually causing any damage.
Let's chat about why this matters. We’ve all been there—staring at a dashboard full of alerts, not knowing which one is a real fire. BAS helps clear that noise. In this guide, we'll look at how these tools work, the different styles of testing, and why your team might need to start using them today.
The term Breach and Attack Simulation, or BAS, refers to a software tool that automates the testing of your security posture. Think of it as a flight simulator for your IT team. Pilots use simulators to practice crashes without dying; IT teams use BAS to practice cyberattacks without losing data.
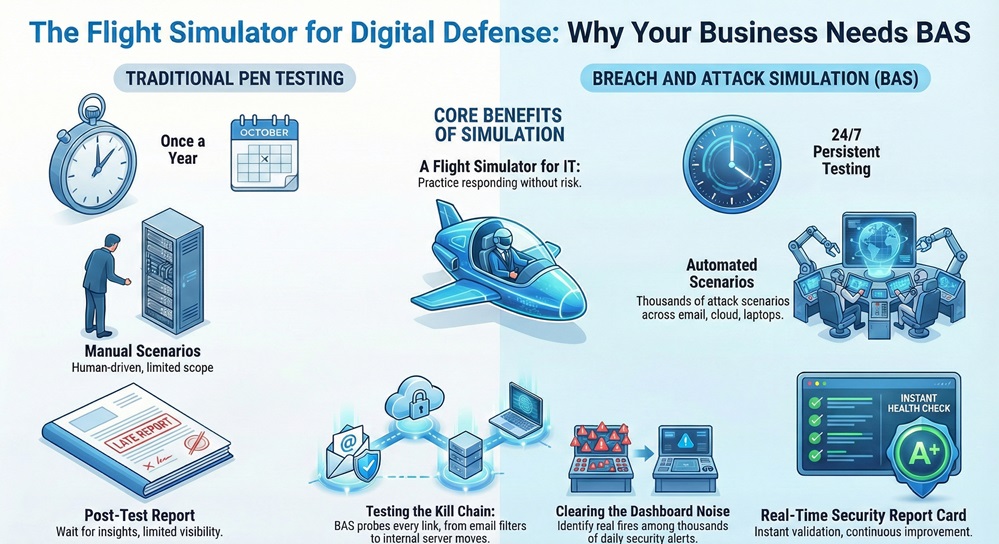
In my view, the biggest win here is automation. Humans are slow and they get tired. Software doesn't. A BAS platform can run thousands of attack scenarios across your emails, cloud, and laptops every single hour. It looks for "pathways" that a criminal might take to steal your "crown jewels"—your customer data or money.
You might ask, "Don't I already have an antivirus?" Yes, but attackers don't just walk through the front door anymore. They use complex steps called the "kill chain." BAS tests every link in that chain. It checks if your email filter catches a fake virus. It checks if your server blocks a fake "lateral move." It gives you a report card on your security health in real-time.
Not all simulation tools work the same way. According to industry experts, we can break them down into three main styles. Each has its own perks, and choosing the right one depends on what you want to protect.
1. The Endpoint Agent Method
In this style, we install small pieces of software (agents) on your computers. These agents talk to each other. They pretend to "infect" one machine and try to jump to another. Since they are controlled, they don't hurt your files. This is great for seeing if your internal office security is tight.
2. The Traffic-Based Approach
Here, the tool sends malicious-looking data packets across your network. It doesn't install anything. It just watches to see if your "guards" (like firewalls) stop the bad data. It’s like a car manufacturer crash-testing a vehicle to see if the airbags deploy.
3. The Playbook Method
This is my favorite because it’s so practical. The software uses a library of "plays" based on real-world groups like the Mitre ATT&CK framework. It tries the exact same tricks that famous hacker groups use. If a new ransomware comes out on Monday, a good BAS tool has a simulation for it by Tuesday.
One must note that BAS is not a replacement for human experts, but it is a massive upgrade in speed. Let's compare the two so you can see the difference.
Penetration Testing (The Old Way):
Breach and Attack Simulation (The New Way):
Here’s the thing: hackers don't wait for your scheduled test. They are always scanning. If you only test once a year, you are giving them 364 days of "free time" to find a way in. BAS closes that gap. It turns security from a "one-time event" into a "constant habit."
If you talk to any security analyst, they'll tell you they're overwhelmed. There are too many tools and too many alerts. How does Breach and Attack Simulation help them?
First, it validates their work. Imagine setting up a new security rule. How do you know it works? Usually, you just hope for the best. With BAS, you can hit a button and "attack" your new rule. If it catches the attack, you know you did a good job.
Second, it helps with "alert fatigue." We've all seen those screens flashing red. BAS helps you figure out which alerts matter. If the simulation shows that an attacker can't actually get to your data, that alert becomes a lower priority. It helps the team focus on the real holes.
Finally, it’s about the budget. When the boss asks, "Why are we spending $50k on this software?" you can show them a BAS report. It proves the software is actually stopping attacks. It turns "I think we're safe" into "I know we're safe."
Ready to try it? You don't have to turn everything on at once. We recommend a "crawl, walk, run" approach.
I want to be real with you—BAS isn't a magic wand. There are a few things to watch out for. Sometimes, simulations can trigger actual alarms in your office. Your IT team might get a "heart attack" thinking a real breach is happening!
This is why communication is key. Everyone needs to know when the "friendly" attacks are running. Also, BAS only tests what it knows. It can't predict a totally new, "never-seen-before" attack. You still need smart humans to think about the "what ifs."
You might think, "We're a small company, we don't need this." But hackers love small businesses because they often have weaker locks. If you have customer data or rely on your website to make money, you are a target.
In my view, Breach and Attack Simulation is becoming a "must-have" rather than a "nice-to-have." As the world gets more digital, the risk grows. Can you really afford to wait six months to find out your firewall has a hole in it?
At the end of the day, security is about peace of mind. You want to go home at night knowing your business is safe. Breach and Attack Simulation gives you that certainty. It takes the guesswork out of cyber defense. Instead of hoping your tools work, you get to see them in action every single day.
We believe that every company deserves a strong defense. Our team is dedicated to helping you find the right tools to stay one step ahead of the bad guys. Your security is our focus, and we're here to make sure your digital doors stay locked tight. Let's build a safer future together!
Ready to see your security gaps before hackers do? Contact our experts today for a free BAS strategy session and harden your defenses!
No. Think of your antivirus as the lock on the door. BAS is the guy who comes by to check if the lock is actually latched and if the door frame is solid. You need both.
Modern BAS tools are very "light." They are designed to run in the background without bothering your employees. You usually won't even know it's there.
Most "out of the box" BAS tools are fairly simple. You can usually get your first scan running in a few hours. However, getting the most out of it takes a bit of time to learn the reports.
The price varies based on the size of your company. While it's an extra cost, most firms find it saves money by preventing a massive data breach, which could cost millions.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts