.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Cloud Identity and Access Management is the most vital tool you have to protect your business data in the digital world. Imagine you run a large hotel. You wouldn't give every guest a master key that opens every room, right? You only give them a key to their own door. In the world of computers, Cloud Identity and Access Management (or Cloud IAM) does exactly that. It makes sure the right people can use the right resources for the right reasons.
To be honest, we’ve all felt that bit of worry when we hear about data breaches. You might wonder, "Is my company's data actually safe?" It's a fair question. As we move more of our work to the cloud, the old way of locking the front door isn't enough. There is no front door anymore! Your employees are working from home, coffee shops, and different countries. This is where Cloud IAM comes in to save the day. It acts as a digital security guard that follows your data wherever it goes.
But how does it actually work? And why does every tech expert keep talking about it? Let's break it down over this virtual coffee.
Before we get into the weeds, let’s define what we are talking about. At its heart, Cloud Identity and Access Management is a framework of policies and technologies. Its goal is to ensure that unauthorized users don't get into your systems. It handles two main jobs: identifying who you are and checking what you are allowed to do.
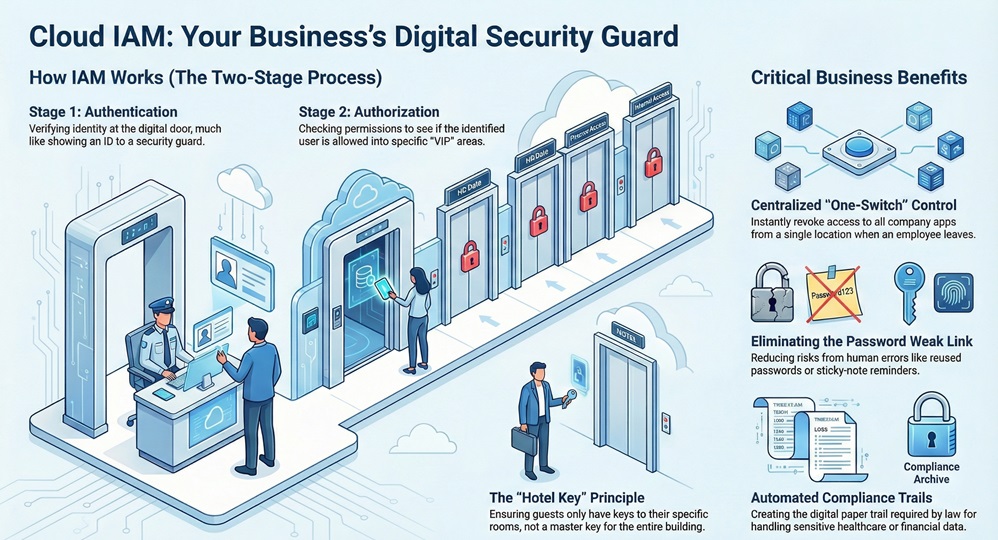
Think of it as two stages. First, you show your ID at the door (Authentication). Second, the guard checks the guest list to see if you’re allowed in the VIP lounge (Authorization). In the cloud, this happens in milliseconds. Without a solid Cloud IAM strategy, your data is basically sitting on a park bench.
Ready to build a Zero Trust foundation? Contact FSD Tech to design your custom IAM roadmap
You might ask, "Can't I just use strong passwords?" Well, in my experience, passwords are the weakest link. People reuse them, write them on sticky notes, or pick "Password123."
Cloud Identity and Access Management helps you move past these human errors. It provides a central place to manage everyone. When an employee leaves the company, you don't want to spend hours logging into fifty different apps to delete their accounts. With IAM, you flip one switch, and they are out. It’s about efficiency just as much as it is about security.
Furthermore, many industries have strict rules. If you handle healthcare or credit card data, the law says you must control who sees what. Cloud IAM provides the paper trail you need to prove you are following the rules.
When we talk about Cloud Identity and Access Management, we usually look at four main parts. These parts work together like the gears in a watch.
1. Identity Management
This is the "Who" part. It involves creating and managing digital identities for users, devices, and even software services. Yes, even your apps need identities! In Cloud IAM, we call these "entities."
2. Authentication (AuthN)
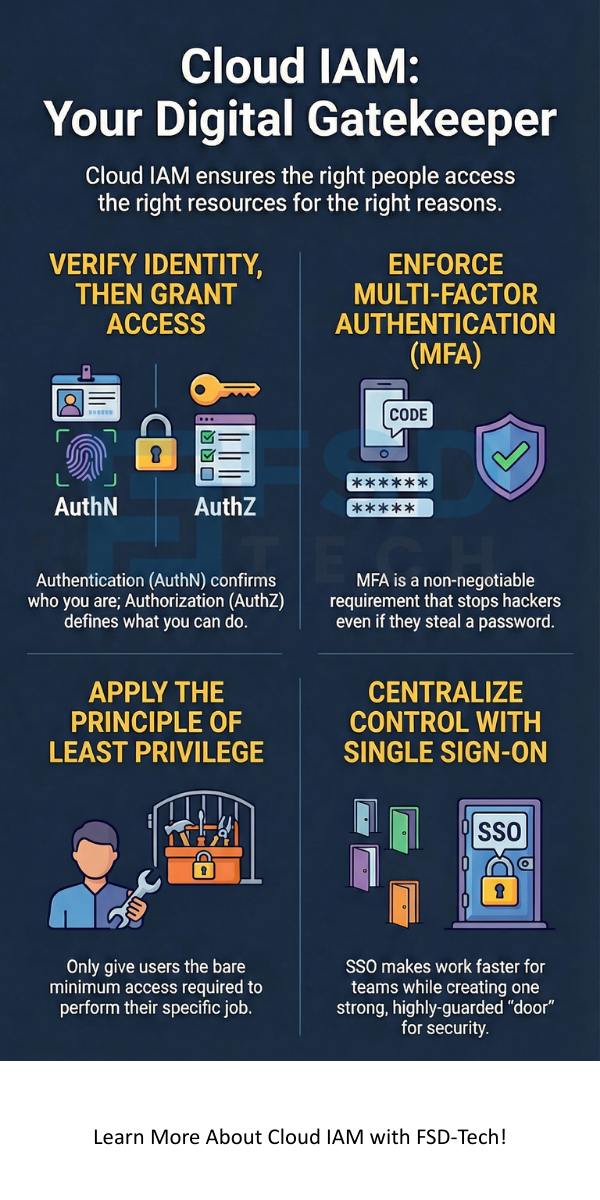
This is the process of verifying that you are who you say you are. We don’t just trust a username anymore. Most modern systems use Multi-Factor Authentication (MFA). This might be a code sent to your phone or a fingerprint scan. It adds that extra layer of "Are you really sure?"
3. Authorization (AuthZ)
Once we know it's you, what can you touch? Authorization uses sets of rules to grant permissions. You don't want the intern to have the power to delete the entire company database by mistake, right?
4. Auditing and Reporting
This is the "What happened?" part. Cloud Identity and Access Management keeps a log of every login and every file accessed. If something goes wrong, you can look back and see exactly who was involved. It's like having a security camera for your data.
Also Read: What is Cloud Access Security Broker (CASB)?
One of the coolest parts of Cloud IAM is something called Role-Based Access Control, or RBAC. Instead of giving permissions to every single person one by one, you create "Roles."
For example, you might have a "Marketing Role." Anyone in the marketing team gets that role. That role automatically gives them access to Facebook Ads and the email tool. If a new person joins the team, you just give them the role. It's much faster than checking boxes for every single app.
That said, you should always follow the "Principle of Least Privilege." This is a fancy way of saying: only give people the bare minimum they need to do their job. If they don't need to see the payroll, don't give them access!
Here is the thing: it can be as simple or as complex as you make it. Most big cloud providers like Google, Amazon, and Microsoft have built-in IAM tools. They want you to use them!
The challenge usually isn't the technology; it's the planning. You have to sit down and ask, "Who really needs access to this?" In my view, the best way to start is small. Lock down your most sensitive data first. Then, slowly bring the rest of your apps into the system.
Do you have a list of all your current users? That’s usually the best place to start. Most companies find "ghost accounts" — accounts for people who left years ago — as soon as they start this process. It’s a real eye-opener!
We've all been there—trying to remember fifteen different passwords for fifteen different work apps. It’s exhausting. Cloud Identity and Access Management solves this with Single Sign-On, or SSO.
With SSO, you log in once to a central portal. Then, you can access all your work apps without typing your password again. It makes life easier for your team. But more importantly, it makes things safer. Because there is only one "door" to guard, you can make that door very, very strong with MFA and high-level encryption.
Also Read: What is Role-Based Access Control (RBAC)?
Why go through all this trouble? Because the bad guys are getting smarter. Here are a few things Cloud Identity and Access Management helps stop:
If you want to do this right, follow these simple steps:
We are moving toward something called "Zero Trust." In a Zero Trust world, the system assumes everyone is a threat until proven otherwise. It doesn't matter if you are sitting in the office or at home; the system will check your identity every single time you try to access something. Cloud Identity and Access Management is the engine that makes Zero Trust possible.
At the end of the day, Cloud Identity and Access Management is about trust. It’s about making sure your team can work freely without putting the company at risk. We believe that security shouldn't be a hurdle; it should be a quiet partner that helps you grow with confidence. Our focus is always on your peace of mind. By putting people and their identities first, we help you build a digital environment that is both open for business and closed to threats. Let's make your cloud journey a safe one!
Ready to lock down your cloud environment? We’re here to help you build a security strategy that actually works for your team. Contact us today for a free security consultation and let's protect what matters most to you!
Traditional IAM was built for servers kept inside an office building. Cloud IAM is built for the internet. It handles users coming from anywhere and connects to services hosted by other companies.
Not at all! In fact, small businesses are often targets because they have weaker security. Even if you only have five employees, using a basic Cloud IAM setup is a smart move.
Actually, with features like SSO, it usually makes work faster. You spend less time resetting passwords and more time getting things done.
Most major cloud providers have very reliable systems with backups. It is much more likely that a user will forget their password than the entire IAM system failing.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts