
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

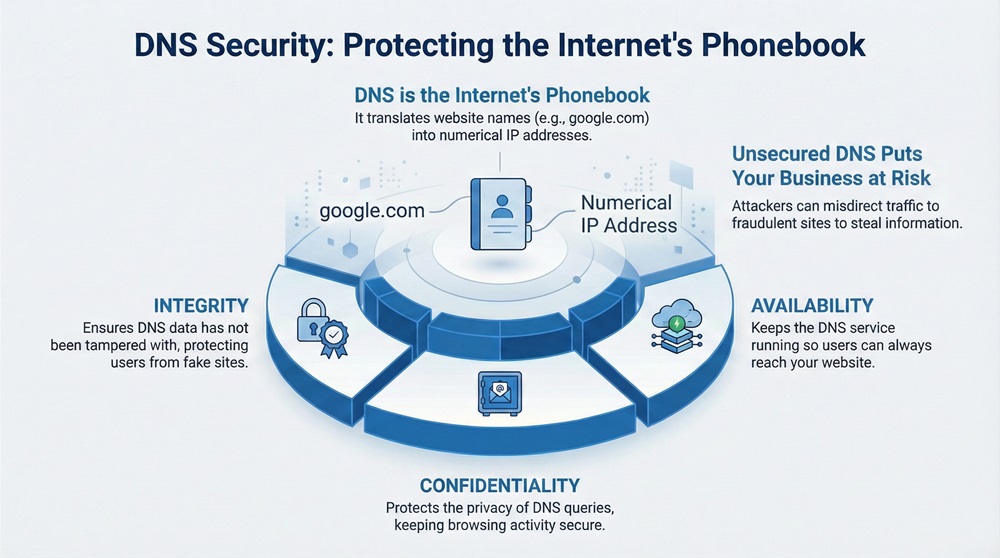
Have you ever typed a website name, like "https://www.google.com/search?q=google.com," and immediately landed on the correct page? The Domain Name System (DNS) makes this simple action happen every day. DNS acts as the internet's phonebook, translating easy-to-remember website names into complex numerical Internet Protocol (IP) addresses that computers use to talk to each other.
But what happens if a criminal messes with this phonebook? Your business, your data, and your customers all face a serious threat. DNS security is nothing but the set of practices, technologies, and protocols you use to keep this vital translation service safe from attack. We will now explore what DNS security is and why it plays a vital role in your overall cyber security strategy.
We will explain how to use the best DNS security tools and DNS security best practices to keep your network safe.
DNS cybersecurity refers to the measures and techniques you implement to protect the Domain Name System infrastructure from unauthorized access, malicious activities, and failures. This system is a critical component of the internet. Therefore, securing it is essential to ensure that users connect to the intended website and not a fraudulent one.
In simple words, DNS security prevents criminals from misdirecting your employees or customers. It also stops them from stealing information or disrupting your services.
To understand this better, it is important to note that DNS security meaning focuses on three core areas:
How does DNS security work to protect your network? It works by implementing layers of defense at different points where DNS requests are handled.
When a user requests a website, the DNS resolution process involves multiple steps. DNS security secures each of these steps:
This approach ensures that the system maintains the correct map between domain names and IP addresses, thereby preventing misdirection and network disruption.
Criminals often target the Domain Name System because of its fundamental role in internet communication. DNS security risks are numerous and evolve constantly.
Let us explore the main DNS security issues your business faces.
The following are the most significant threats that target the Domain Name System.
Now, the question arises: How do we protect against these varied and persistent attacks? The answer lies in robust DNS security best practices and technologies like DNS Security Extensions (DNSSEC).
Also Read: Domain Spoofing Explained: How It Works & How to Stop It
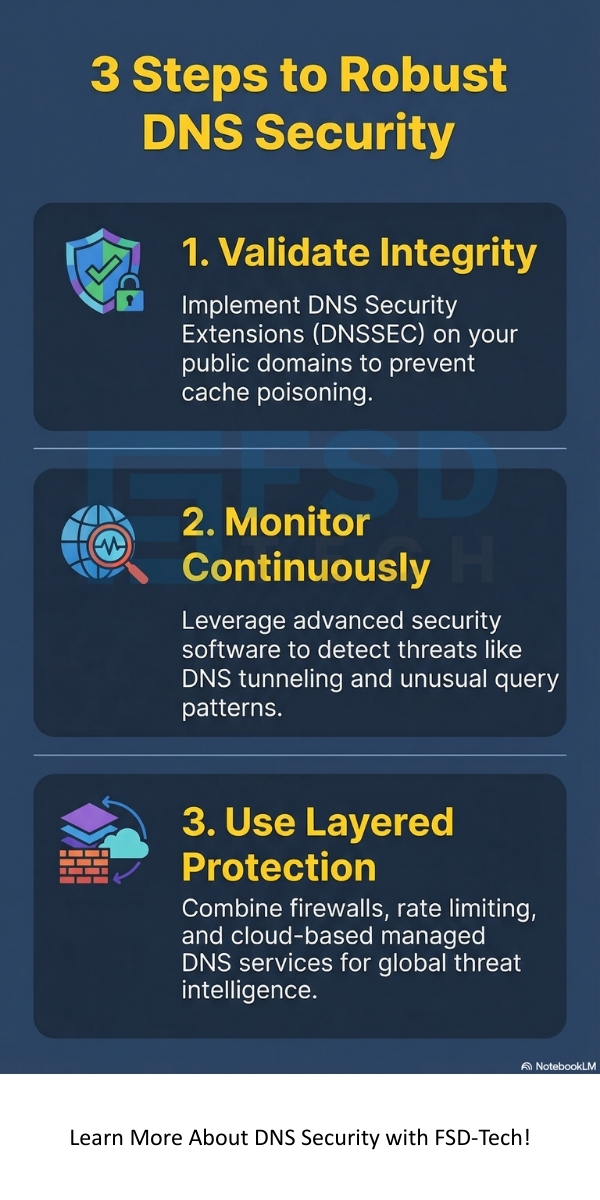
DNS Security Extensions (DNSSEC) is one of the most crucial technological advancements for strengthening the Domain Name System. DNS security extensions are nothing but a set of specifications that provides data origin authentication and data integrity protection for DNS.
DNS security extensions work on the principle of cryptography—using digital signatures. Simply put, DNSSEC adds a layer of trust to the standard DNS lookup process.
This mechanism ensures that the user connects to the correct website, giving an assurance of the data's integrity. DNSSEC implementation is vital for any modern organization.
When securing your network, you have multiple options, ranging from basic protection to advanced managed DNS security services. Let us compare two primary types of solutions: basic DNS security software and advanced DNS security services.
Comparison of DNS Security Approaches
| Basis for Comparison | Basic DNS Security Software (e.g., Local Firewall) | Advanced Managed DNS Security Service |
|---|---|---|
| Primary Goal | Preventing access to known bad domains (basic filtering). | Comprehensive protection against advanced threats (e.g., tunneling, DDoS). |
| Implementation | Installed and managed on-premise on local servers. | Cloud-based service; traffic is routed through the provider's global network. |
| Defense Scope | Limited to the local network where the software is running. | Extends protection to users regardless of their location (on-premise or remote). |
| Threat Intelligence | Relies on simple, often static, threat lists. | Uses real-time, global threat intelligence and behavioral analysis. |
| Key Feature | Basic domain filtering. | DNS Tunneling detection, DDoS mitigation, and detailed DNS security monitoring. |
| Deployment | Requires manual configuration and updates. | Easy, centralized deployment and automatic updates. |
Advanced DNS security services provide a more comprehensive and real-time defense against the most sophisticated DNS security threats.
Also Read: What is a Firewall as a Service (FWaaS)?
You must implement strong DNS security best practices to effectively protect your digital assets. Taking into account the wide range of threats, a multi-layered approach is the most effective.
Securing your authoritative or internal DNS server is crucial. The following steps comprise the most effective defense strategy:
Effective DNS security monitoring and the use of the right DNS security tools are essential for a proactive defense.
What is the best way to determine which DNS server is best for your organization? Considering your size and complexity, a managed DNS security service often provides the best DNS security because it includes global threat intelligence and DDoS mitigation.
DNS security is absolutely vital for safeguarding your modern business. You now understand that criminals actively target the internet's phonebook using sophisticated methods like DNS cache poisoning and DNS tunneling. Therefore, you must move beyond basic protection. Implement DNS Security Extensions (DNSSEC) to guarantee the integrity of your data.
Furthermore, leverage managed DNS security services and continuous DNS security monitoring. This comprehensive approach ensures the availability of your services and prevents data loss. We commit to empowering you with the strategies and best DNS security tools you require to maintain a reliable and secure presence in the digital world.
Worried About DNS Risks? Reach us for immediate help
So, with the above discussion, we can say that securing the Domain Name System is no longer an option—it is a fundamental requirement for modern businesses. The complexity and persistence of DNS security threats necessitate a proactive, layered defense.
The primary purpose of DNS security is to ensure the integrity and availability of the Domain Name System resolution process. This prevents criminals from redirecting users to fake websites or making legitimate services unavailable through attacks like DDoS or cache poisoning.
DNS security is vital for a business because a compromised DNS can lead to:
No, DNS Security Extensions is not the only solution. While DNSSEC ensures data integrity and prevents DNS cache poisoning, it does not protect against DDoS attacks or DNS tunneling. A comprehensive strategy requires a combination of DNSSEC, firewalls, rate limiting, and a DNS security service for threat intelligence.
A secure DNS (like one using DNSSEC) focuses on the integrity of the resolution—ensuring that the IP address is correct. On the other hand, a private DNS (like one using DNS over HTTPS, i.e., DoH) focuses on the confidentiality of the query—ensuring that no one can secretly see what websites you are visiting. Both are essential for a strong overall security posture.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts