.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Have you ever wondered if someone changed a sensitive file on your server without you knowing? It is a scary thought for any business owner or IT manager. Most people think a firewall is enough, but what happens when the threat is already inside? To be honest, most data breaches involve unauthorized changes that go unnoticed for months. In my experience, catching these small tweaks early is the difference between a minor fix and a total system collapse.
File integrity monitoring acts as your digital security camera. It watches your files 2026/7, 24 hours a day, and alerts you the moment something smells fishy. But how does it actually work? Why do compliance auditors obsess over it? Let us dive into the details of this essential security tool.
| Basis for Comparison | File Integrity Monitoring (FIM) | Standard System Logging |
|---|---|---|
| Primary Focus | Monitors specific file changes and content integrity. | Records general system events and user logins. |
| Detection Method | Uses cryptographic hashing to verify file state. | Records text-based metadata of activities. |
| Alerting | Provides real-time alerts for unauthorized modifications. | Usually requires manual review or SIEM analysis. |
| Data Depth | Shows exactly what changed inside the file. | Shows that a file was accessed, but rarely "what" changed. |
| Compliance | Mandatory for PCI DSS, HIPAA, and NERC CIP. | Generally helpful but often insufficient alone. |
File integrity monitoring, often called FIM, is an internal security process that validates the integrity of operating system and application software files through a verification method between the current state and a known good baseline. It monitors for changes in folders, files, and settings that could indicate a cyberattack or human error.
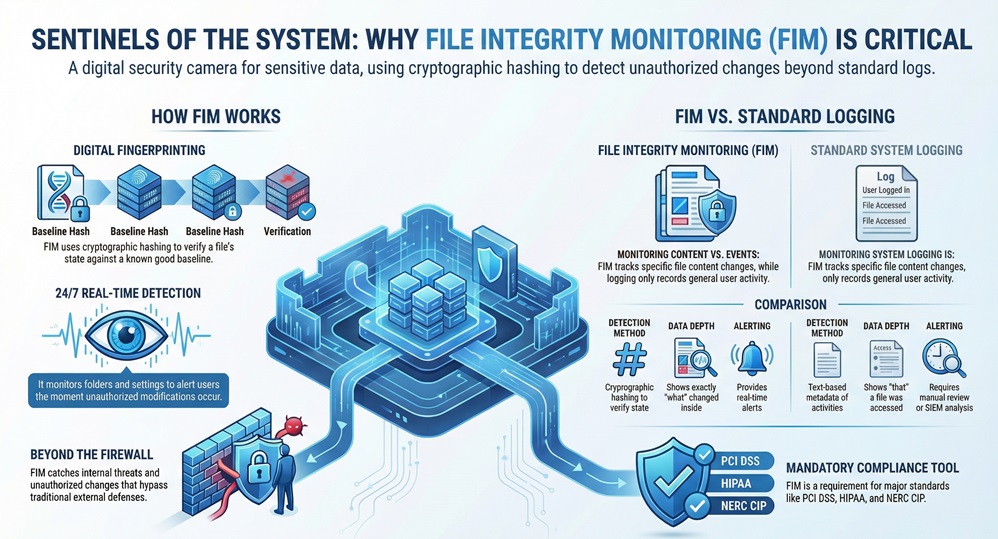
To understand this, we need to look at it as a "digital fingerprinting" system. Every file has a unique identity. When a hacker or a rogue employee modifies a configuration file, that identity changes. File integrity monitoring ensures that you are the first to know when that fingerprint no longer matches the original record.
Secure your data now with Cimtrak
The working of file integrity monitoring can be understood through a simple four-step cycle. It does not just "look" at files; it uses math to prove they are safe.
1. Establishing the Baseline
First, the file integrity monitoring software scans your system to find "known good" versions of your files. It creates a cryptographic hash (like SHA-256) for each one. This hash is a long string of characters that represents the file's exact contents. If even one pixel in an image or one character in a text file changes, the hash changes completely.
2. Constant Observation
Once the baseline exists, the file integrity monitoring tool starts its watch. It periodically or in real-time re-calculates the hashes of your protected files. It looks at:
3. Comparison and Detection
Now the question arises: what happens during a scan? The system compares the new hash to the baseline hash. If they are identical, everything is fine. However, if they differ, the file integrity monitoring system flags it as a change.
4. Alerting and Reporting
If the change is unauthorized, the system sends an alert to your security team. High-quality file integrity monitoring tools like Cimcor's CimTrak can even show you exactly who made the change and what the new code looks like compared to the old code.
Also Read: What is a Wireless LAN Controller? Configuration & Setup 101
File integrity monitoring is not just a "nice-to-have" feature. It is a fundamental layer of defense. Here is the thing: hackers love to hide in plain sight. They might change a system file to create a "backdoor" so they can return later. Without file integrity monitoring, you might never see that backdoor.
Meeting Strict Compliance Standards
If you handle credit card data, you must follow PCI DSS. Requirement 11.5 of PCI DSS specifically demands file integrity monitoring. The same goes for healthcare (HIPAA) and federal agencies (FISMA). These organizations know that logs can be faked, but hashes do not lie.
Detecting Zero-Day Attacks
Antivirus software looks for "known" viruses. But what if the virus is brand new? File integrity monitoring does not care what the virus looks like. It only cares that your system files changed. By focusing on the "state" of your files, file integrity monitoring catches threats that other tools miss.
Stopping Internal Human Error
Let us be honest; sometimes the "threat" is just a tired IT admin. A simple mistake in a configuration file can take down an entire network. File integrity monitoring helps you identify these accidental changes instantly, allowing you to roll back to a safe state before the customers even notice.
When you are looking for file integrity monitoring software, you shouldn't just pick the cheapest option. You need a tool that simplifies your life, not one that floods your inbox with useless alerts.
Also Read: What is VPN Gateway? 7 Key Ways It Secures Your Network
Implementing file integrity monitoring requires a bit of strategy. You can't monitor every single file on a hard drive; it would slow your computer to a crawl. Follow these steps for a smooth rollout:
File integrity monitoring is incredibly versatile. While we usually talk about it in terms of "hackers," it serves many purposes in a modern business.
Monitoring Cloud Environments
As companies move to the cloud, they lose some control over their hardware. File integrity monitoring gives that control back. It monitors your cloud instances to ensure the provider or an external attacker hasn't tweaked your virtual machines.
Protecting Point-of-Sale (POS) Systems
Retailers are huge targets. Hackers try to install "scrapers" on POS systems to steal credit card numbers. File integrity monitoring watches the POS software files. If a scraper tries to install itself, the file integrity monitoring system kills the process or alerts the manager immediately.
Enhancing DevOps Security
In a fast-paced coding environment, "configuration drift" is a nightmare. This happens when different servers slowly become different from each other due to manual tweaks. File integrity monitoring ensures every server in your cluster stays exactly the same as your master blueprint.
File integrity monitoring is the backbone of a proactive security strategy. It moves you away from "guessing" if you are safe and gives you mathematical proof that your systems remain untampered. At our company, we believe that security should be transparent and undeniable. We focus on giving you total visibility into your infrastructure because you can't protect what you can't see.
By prioritizing the integrity of your data, you aren't just checking a box for a compliance auditor—you are building a wall of trust around your business and your customers. To be honest, in a world where data is the most valuable currency, file integrity monitoring is the vault that keeps it safe.
Prevent data breaches today, Contact Our FIM Experts

No, they are different. Antivirus looks for malicious code (the "bad guys"). File integrity monitoring looks for changes to your files (the "crime scene"). You need both for a complete security stack.
If configured poorly, it can. However, modern file integrity monitoring tools are very lightweight. By focusing only on critical system files and using efficient hashing, the impact on your CPU is usually less than 1%.
Yes! Advanced file integrity monitoring solutions can monitor database schemas, stored procedures, and triggers. This is vital because many attacks target the data stored inside the database rather than the files on the disk.
Change noise refers to the hundreds of "normal" changes that happen on a computer every day (like log updates). A good file integrity monitoring tool filters these out so you only see the important, unauthorized changes.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts