
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Network security relies on a strong framework to manage user access and track activity. You need a way to verify who a person is and what they can do once they enter your system. This is where Authentication Authorization and Accounting (AAA) becomes essential. The AAA framework provides a modular way to handle these three distinct security functions.
How do you ensure that only the right people access your sensitive data? How do you keep a record of what happens on your network for billing or auditing? Authentication Authorization and Accounting (AAA) answers these questions by creating a structured environment for network security.
In this guide, you will learn how Authentication Authorization and Accounting (AAA) works. We will look at each component and see how they interact to protect your digital assets. Let us start by defining what this framework actually means for your business.
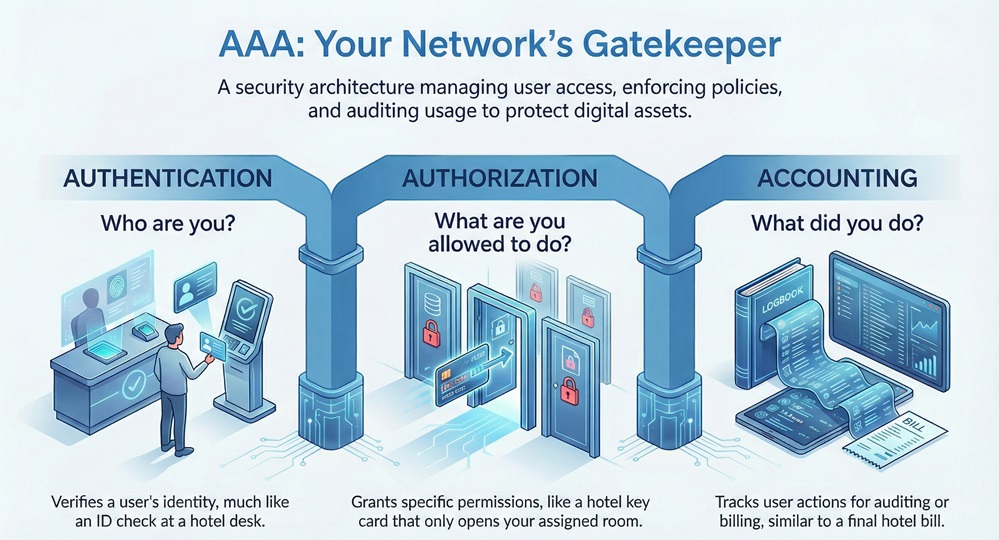
Authentication Authorization and Accounting (AAA) refers to a security architecture used to manage user access, enforce policies, and audit usage. It acts as the gatekeeper for your network. Authentication Authorization and Accounting (AAA) ensures that every user is identified, granted specific rights, and held accountable for their actions.
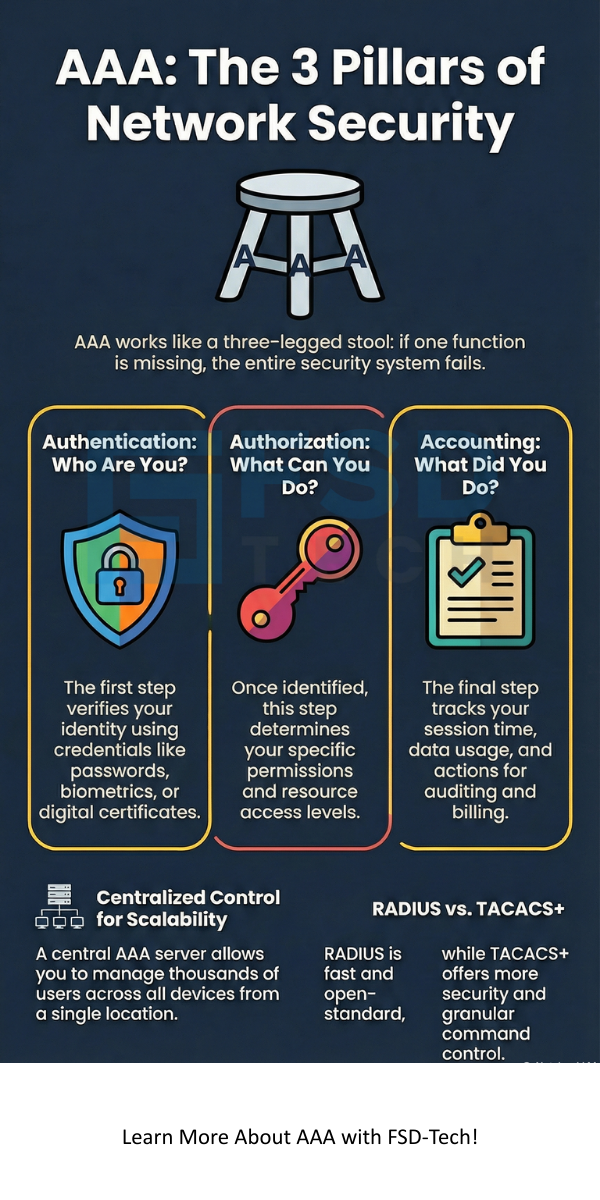
Authentication Authorization and Accounting (AAA) can be understood as a three-legged stool. If one leg is missing, the security of the entire system falls apart. Organizations use this framework to centralize administration. Instead of managing users on every single device, you use a central AAA server.
To understand this better, think about a hotel. Authentication is your ID check at the front desk. Authorization is the key card that only opens your room. Accounting is the final bill that lists all your charges.
Authentication Authorization and Accounting (AAA) splits security tasks into three logical steps. Each step plays a vital role in maintaining a secure network environment.
Authentication is the first step in the process. It is the method of verifying the identity of a user or device. When you log into a computer, you provide a username and password. The system checks these credentials against a database.
If the credentials match, the system identifies you as a valid user. Authentication Authorization and Accounting (AAA) supports various methods like digital certificates, biometrics, and one-time passwords.
Authorization happens after you successfully authenticate. It determines what resources you can access and what operations you can perform. Just because you are allowed into the building does not mean you can enter the server room.
Authentication Authorization and Accounting (AAA) uses policies to define your rights. These rights might include access to specific files, the ability to run certain commands, or time-of-day restrictions.
Accounting is the final piece of the puzzle. It involves collecting and reporting data about user activity. Authentication Authorization and Accounting (AAA) tracks when you log in, when you log out, and what data you transferred.
This data is crucial for billing, capacity planning, and security auditing. If a security breach occurs, accounting logs help you trace the steps of the intruder.
Also Read: What is the Principle of Least Privilege (PoLP)? Guide & Benefits
The following table provides a quick look at the differences between the three components.
| Basis for Comparison | Authentication | Authorization | Accounting |
|---|---|---|---|
| Main Goal | Verifying identity | Granting permissions | Tracking activity |
| Timing | Happens first | Happens after authentication | Happens during and after session |
| Information Used | Passwords, tokens, IDs | Roles, groups, policies | Timestamps, data usage, logs |
| Typical Question | Who are you? | What can you do? | What did you do? |
| Outcome | Access granted or denied | Level of access defined | Log entry created |
Authentication Authorization and Accounting (AAA) follows a specific sequence of events to protect a resource. Let us discuss the typical workflow when a user attempts to connect to a network.
Also Read: What is SD-WAN Architecture? Benefits and Working
To implement Authentication Authorization and Accounting (AAA), you need protocols that allow devices to talk to the server. The two most common protocols are RADIUS and TACACS+.
RADIUS (Remote Authentication Dial-In User Service)
RADIUS is an open-standard protocol. It is mainly used for network access. RADIUS combines authentication and authorization into a single exchange. It encrypts only the password during transmission. Because it uses UDP, it is generally faster but less reliable in complex environments.
TACACS+ (Terminal Access Controller Access-Control System Plus)
TACACS+ is a Cisco-proprietary protocol, though it is widely supported. It separates authentication, authorization, and accounting into distinct processes. TACACS+ encrypts the entire body of the packet. It uses TCP, which ensures reliable delivery of data. Many admins prefer TACACS+ for device administration because it allows for granular command authorization.
Authentication Authorization and Accounting (AAA) provides several benefits for modern businesses. As networks grow, manual management becomes impossible.
Centralized Management
Authentication Authorization and Accounting (AAA) allows you to manage all user accounts in one place. If an employee leaves the company, you disable their account on the AAA server. They immediately lose access to all network devices. Without this, you would have to log into every switch and router to delete their user profile.
Scalability
The framework scales easily. Whether you have ten users or ten thousand, the process remains the same. You can add more AAA servers to handle the load and provide redundancy.
Enhanced Security
By using Authentication Authorization and Accounting (AAA), you enforce a consistent security policy. You can require strong passwords or multi-factor authentication (MFA) across the board. The accounting logs provide a clear trail for compliance and forensics.
Accurate Auditing
Accounting helps you understand how your resources are used. You can see which users consume the most bandwidth or which devices are accessed most frequently. This data helps in making informed decisions about infrastructure upgrades.
Implementing AAA in Your Network
Setting up Authentication Authorization and Accounting (AAA) requires careful planning. You must decide which protocol fits your needs and which server software to use.
Choosing a Server
You can use dedicated software like Cisco Identity Services Engine (ISE) or FreeRADIUS. Some organizations use Active Directory (AD) as the backend database for their AAA server. This integration ensures that network access matches company-wide user credentials.
Defining Policies
Authentication Authorization and Accounting (AAA) is only as good as the policies you create. You should follow the principle of least privilege. This means giving users the minimum level of access they need to perform their jobs.
Monitoring and Logs
Simply collecting logs is not enough. You must regularly review your accounting data. Look for failed login attempts or unusual activity patterns. High numbers of failed authentications might indicate a brute-force attack.
Also Read: What is SQL Injection (SQLi) Attack? Examples & Prevention
Authentication Authorization and Accounting (AAA) is the foundation of a Zero Trust architecture. In a Zero Trust model, you never trust anyone by default. Every user must be verified and authorized for every session.
Authentication Authorization and Accounting (AAA) facilitates this by providing a continuous loop of identity verification and activity tracking. As cloud services and remote work become standard, the "perimeter" of the network disappears. Your security must follow the user, and that is exactly what this framework does.
Now, the question arises: should you use RADIUS or TACACS+? Let us explore the technical distinctions.
While Authentication Authorization and Accounting (AAA) is powerful, it is not without challenges.
Authentication Authorization and Accounting (AAA) is more than just a technical requirement. It is a strategic approach to identity management and data protection. By separating identity, permission, and tracking, you create a robust defense against unauthorized access.
Our team focuses on building secure foundations for every client. We believe that clarity in security leads to better business outcomes. When you know exactly who is on your network and what they are doing, you can operate with confidence. Authentication Authorization and Accounting (AAA) provides that peace of mind.
Protecting your network starts with knowing your users. Use Authentication Authorization and Accounting (AAA) to build a system that is both secure and easy to manage. If you value transparency and control, this framework is the right choice for your organization.
Book a Call with Our Network Experts
Authentication checks who you are. Authorization determines what you can do. You must be authenticated before the system can authorize your actions.
No. Even small businesses benefit from centralized access control. It reduces the risk of orphaned accounts and simplifies management.
Yes. WPA2-Enterprise and WPA3-Enterprise use RADIUS for Authentication Authorization and Accounting (AAA) to verify individual user credentials instead of a shared password.
Most network devices have a "fallback" configuration. You can set a local username and password that only works if the server is offline.
Yes. Many modern AAA servers can integrate with MFA providers to add an extra layer of security during the authentication phase.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts