
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

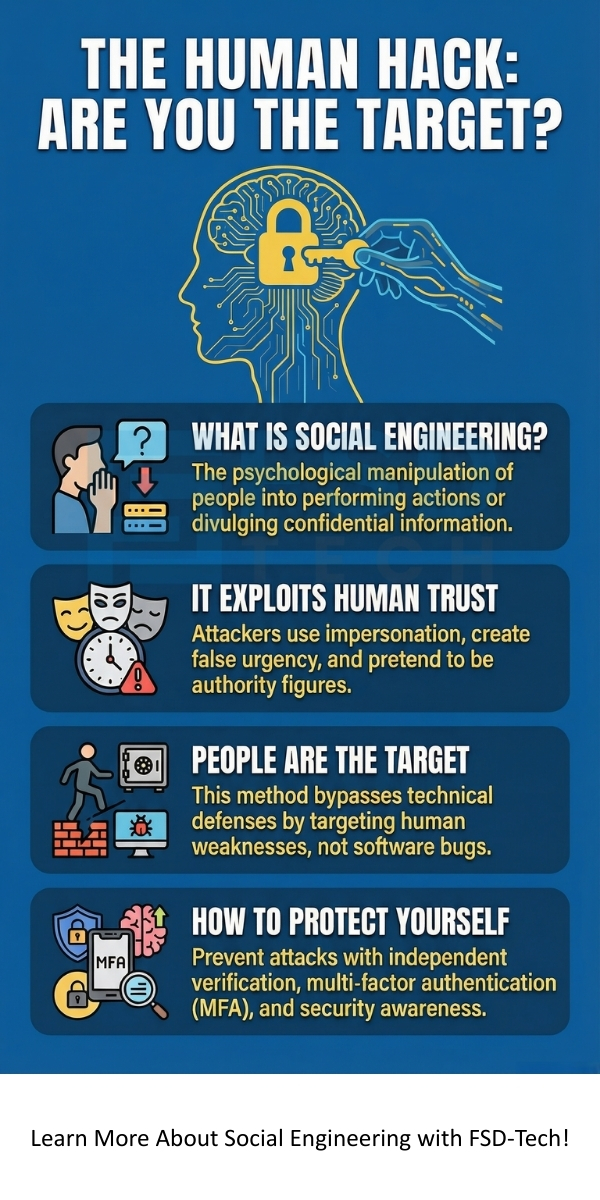
Social engineering refers to the use of psychological manipulation to trick individuals into divulging confidential information or performing actions that benefit an attacker. It is a non-technical method that hackers use to get what they want. This deceptive practice relies on exploiting the natural human tendency to trust others.
The primary function of social engineering is to bypass security safeguards by targeting the human element, which is often the weakest link in any security system.
The two essential components are the attacker (the person or group attempting the manipulation) and the target (the individual possessing the desired information or access). Social engineering attacks often start with seemingly harmless communication. It consists of various tactics, including impersonation and manipulation, which can easily trick unsuspecting victims.
A successful attack can lead to data breaches, financial loss, or unauthorized system access, making it a crucial real-world security concern.
In this section, we will discuss social engineering in detail along with its types and how you can protect yourself and your company. We will learn how these social engineering attacks work and the psychology behind them. To know more about social engineering, read below.
The term social engineering can be understood as the clever art of manipulating people to give up private information. This private information is often highly sensitive, like passwords or bank details. Social engineering is not about hacking software or breaking codes. Instead, it is about fooling people. People are tricked into trusting the attacker.
Social engineering attacks often start by building a relationship or trust with the target. Attackers may pretend to be a colleague, an IT support person, or even a manager. This is a form of impersonation. The attacker creates a false sense of urgency or need.
For instance, the attacker might claim there is a critical system error that only you can fix by giving them your password. The attacker exploits basic human emotions like curiosity, fear, or a desire to be helpful.
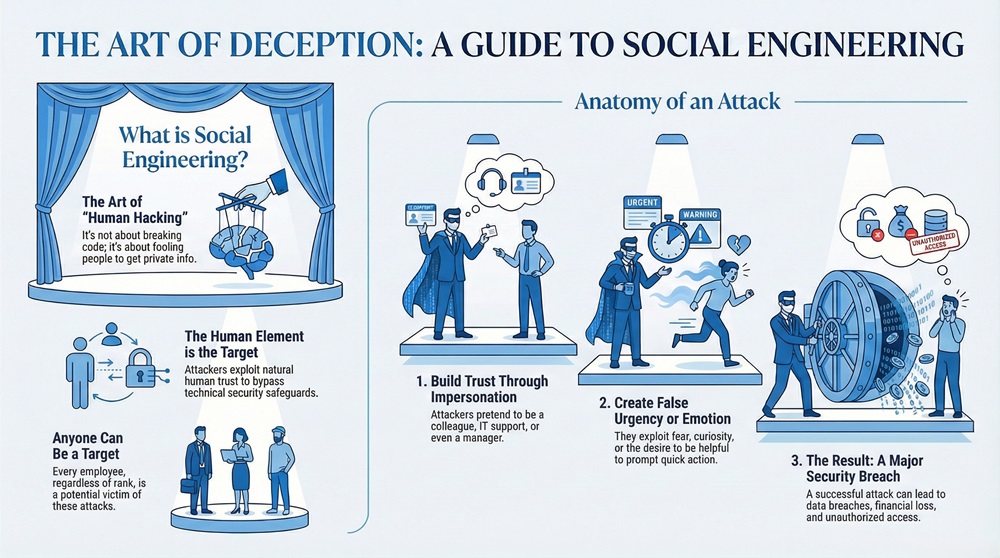
Let us now understand that every employee, no matter their rank, is a potential target of social engineering. It is a major threat to businesses and individuals alike. This is why awareness about these security threats is vital. If you do not know about the attack, how can you stop it?
Don’t be the next victim – talk to a Cato expert today!
Let us now discuss the psychological principles that these social engineering attacks utilize. Social engineering works because it exploits how the human mind makes decisions. These are subtle yet powerful techniques that make people drop their guard. This type of manipulation makes the victim feel less alert about the security risk.
The six essential principles of influence that these attackers commonly use are:
Also Read: What is a Virtual Private Network? How does VPN works?
Social engineering attacks are diverse and constantly changing. However, they rely on a few common methods. Each type has a specific way of tricking the victim. Understanding these methods is the first step toward better cyber security.
Following are the major types of social engineering attacks:
Phishing can be defined as an attempt to acquire sensitive information, like usernames, passwords, and credit card details, often for malicious reasons. Phishing attacks impersonate a trustworthy entity in an electronic communication. These communications are usually emails but can also be texts or instant messages.
Phishing is a huge problem because the attacks are simple to carry out and highly effective. In simple words, the goal of the phishing attack is to trick you into clicking a link or opening an attachment. The link will take you to a fake website that looks real. This fake website is designed to steal your login credentials. The attachment often contains malicious software (malware).
Let us now discuss the most common types of phishing:
The following list shows some signs of a phishing attack:
Also Read: IPSec Explained: Protocols, Modes, IKE & VPN Security
To understand social engineering, it is necessary to go through the steps an attacker takes. The attacker does not just send a random email. They follow a careful process to ensure success. Here, we will see how a typical social engineering scam works.
The following are the typical phases of a social engineering attack:
As shown in the diagram above, the attacker's success depends on how well they execute the pretexting and exploitation phase. Observe that thorough planning in the investigation phase is critical for the success of the attack.
Let us now understand that social engineering attacks share several common characteristics. These features make them a serious and continuous security problem. They are often what distinguishes them from purely technical hacks.
Following are the key characteristics of social engineering:
In finer terms, the core of social engineering is a psychological game played against the victim.
While a powerful tool for criminals, social engineering also has its limitations and risks. It is not always a guaranteed success for the attacker.
Following are the key disadvantages or risks:
Also Read: What is a Firewall as a Service (FWaaS)?
Social engineering is used in many real-world scenarios, and its applications are always malicious. For instance, these attacks are often used to gain initial access to a corporate network.
The major applications of social engineering are:
Example: Consider the following scenario. An attacker sends a target a text message (smishing) that says, "Your bank account has been locked. Click here to verify your details immediately." The link goes to a fake bank website. The victim, fearing their account is locked, enters their login and password. The attacker then steals the credentials. This is a common and highly effective application of social engineering.
Social engineering uses various ways to attack a target. Here is a chart that clearly shows the differences between the three main electronic attack vectors.
| Basis for Comparison | Phishing | Vishing | Smishing |
|---|---|---|---|
| Meaning | It refers to the attempt to steal information using email or malicious websites. | It refers to the use of voice communication over the telephone to trick victims. | It refers to the use of text messages (SMS) to deceive the target. |
| Nature | The attack is primarily text and link-based, often sent to a large number of people. | The attack relies on real-time conversation and voice manipulation. | The attack uses brief, urgent text messages and typically includes a malicious link. |
| Examples | A fake email from an IT department asking you to click a login link. | A call from someone claiming to be technical support asking to remote into your computer. | A text message about an urgent package delivery requiring you to click a tracking link. |
| Function/Purpose | Its main function is to steal login credentials and distribute malware. | Its main purpose is to build trust through conversation and create a false sense of urgency. | Its function is to exploit the immediate and casual nature of mobile messaging. |
| Determined by | The believability of the email's content and the look of the fake website. | The attacker's ability to sound professional, authoritative, or distressed. | The immediate, alarming message that bypasses email spam filters. |
| Method | It utilizes deceptive emails and fake website landing pages. | It uses Voice over IP (VoIP) and caller ID spoofing technology. | It leverages the mobile phone's notification system and inherent trust in text alerts. |
| When Used/Application | Used for mass data theft and credential harvesting. | Used for targeted, high-value attacks where conversation is needed. | Used for quick financial scams and immediate malware delivery. |
Protection against social engineering is mostly about awareness and caution. Since the attacker targets your behavior, you need to change how you react to suspicious requests. Let us now discuss some ways you can protect yourself from these security threats.
Following are the simple but effective steps to prevent social engineering:
It must be noted that you should be particularly suspicious of requests for passwords or money transfers. No legitimate company will ask for this type of information via an unexpected email or phone call.
Social engineering is the clever art of human manipulation used for malicious gain. It exploits basic human nature—like trust, fear, and a desire to be helpful—to bypass technical security systems. We have discussed how phishing, pretexting, and other tactics are used to steal vital information. The success of social engineering attacks relies on thorough reconnaissance and the exploitation of psychological principles like authority and urgency.
Therefore, the key to staying safe is vigilance and education. Understanding the signs of a social engineering attack and implementing security practices like Multi-Factor Authentication are essential defenses. Every individual must act as a human firewall.
Hence, we believe that a well-informed user is the best defense against this persistent and evolving threat. We are dedicated to providing you with the knowledge needed to protect your digital life and maintain strong cyber security.
One whaling email can cost millions. See how Cato SASE blocks executive impersonation in real time – schedule a live demo!
The main goal of a social engineering attack is to manipulate people into giving up sensitive information, such as passwords, banking details, or access to secure systems. The attacker wants to gain unauthorized access to data or funds by exploiting human nature rather than technical flaws.
Pretexting differs from phishing because it relies on creating a detailed, false scenario (the pretext) through conversation, often via phone or face-to-face. Phishing uses broad, non-specific electronic communication, like email, to trick many targets at once using a fake link or attachment. Pretexting is more targeted and involves more interaction.
Social engineering is considered a serious security threat because it bypasses all technical security layers like firewalls and encryption. It attacks the weakest point, the human user. A highly trained attacker using impersonation and urgency can be more effective than a complex technical hack.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts