.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Recovery Point Objective acts as the heartbeat of your company’s disaster recovery strategy. Imagine your office loses power or a hacker locks your files at 2:00 PM. If your last backup happened at 10:00 AM, you just lost four hours of hard work. Can your business survive that gap? That specific four-hour window is what we call your RPO.
To be honest, most people ignore this metric until something goes wrong. We’ve all been there, thinking our data is safe just because "we have a backup." But here is the thing: a backup is only as good as its timing. In my experience, companies that don't define a clear Recovery Point Objective often face devastating financial hits during a crisis.
Are you actually prepared for a data breach? Or are you just hoping for the best? Let’s break down how this technical term keeps your business running when things go south.
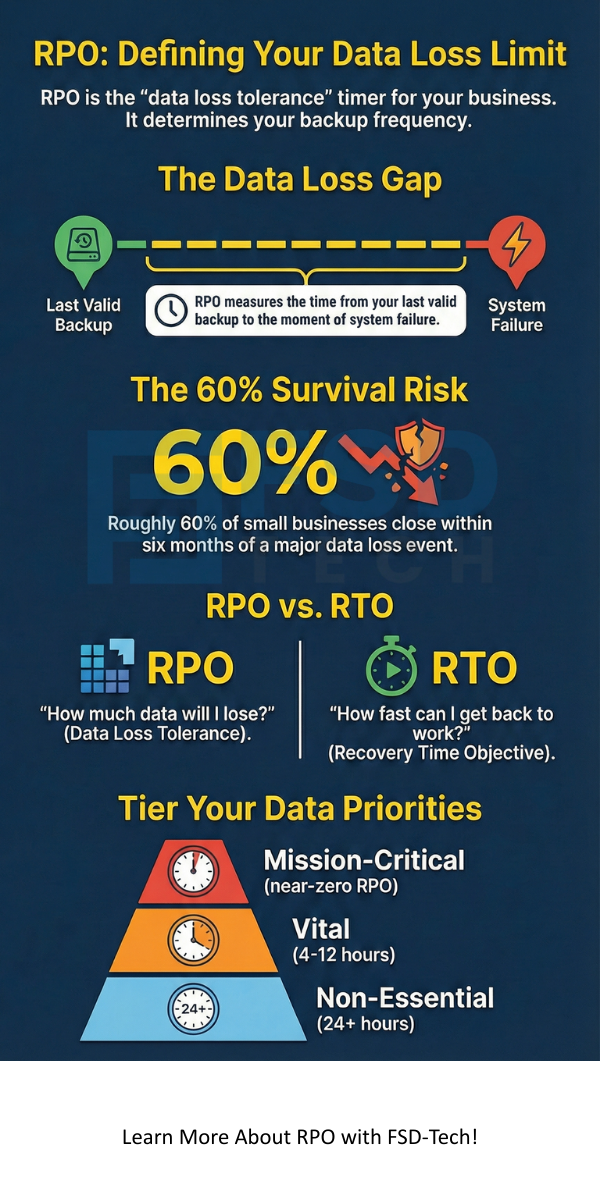
The Recovery Point Objective refers to the maximum amount of data your organization can afford to lose. It is essentially a measurement of time. You look back from the moment of a failure to the last valid backup. If you set an RPO of one hour, you must back up your data every hour.
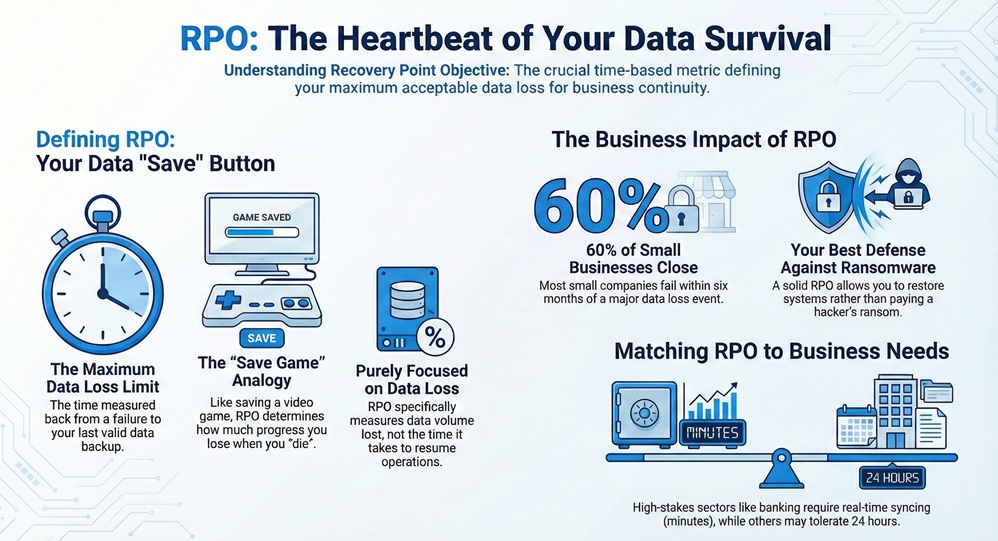
This metric tells your IT team how often they need to copy data. Think of it like a "save" button in a video game. If you only save once a day, and you "die" in the game at night, you lose the whole day's progress. In cybersecurity, we use this to ensure that we don't lose vital customer info or financial records.
Now, let’s discuss the technical side. According to industry whitepapers, RPO focuses purely on data loss. It does not look at how long it takes to get back to work. It only cares about the "point" in time you can return to. This is why it is a pillar of any modern Business Continuity Plan (BCP).
Get a Free Disaster Recovery Assessment
In a world full of ransomware, having a solid Recovery Point Objective is your best defense. When a virus encrypts your servers, you have two choices. You can pay the ransom, or you can wipe the system and restore from a backup. Your RPO determines how much work you have to redo once that restoration is finished.
Here, the Recovery Point Objective acts as a safety net. If you work in a bank, losing even one minute of data could mean losing thousands of transactions. Conversely, a small local plumbing shop might only need an RPO of 24 hours. Does your current backup schedule match the speed of your business?
Roughly 60% of small businesses close within six months of a major data loss event. That is a scary thought. By defining your RPO, you are essentially setting a "loss tolerance" level. It helps you decide which systems need expensive, real-time syncing and which ones can wait until the end of the day.
Calculating a Recovery Point Objective isn't just about picking a random number. You must look at how your data changes throughout the day. In my view, the best way to start is by categorizing your data into tiers. Not all files have the same value.
Tier 1: Mission-Critical Data
This includes your live databases, customer orders, and financial transactions. For these, you likely need an RPO of zero or near-zero. This means you use "high availability" tools that copy data the second it is created.
Tier 2: Vital Data
These are files you use daily but aren't "live" every second. Think of internal project trackers or HR records. An RPO of 4 to 12 hours might work here.
Tier 3: Non-Essential Data
This covers old archives or marketing assets that don't change much. A 24-hour or even weekly RPO is usually fine for this group.
Picture this: your main server crashes. If you have Tier 1 data with a 24-hour RPO, you are in big trouble. You'll spend weeks trying to figure out what customers bought in those 24 hours. That’s why we use these tiers to balance cost and safety.
Also Read: Is Your Business PCI Compliant? A 12-Step Roadmap
People often get RPO mixed up with RTO. While they sound similar, they solve different problems. As we have already discussed, RPO is about "How much data will I lose?" On the other hand, RTO (Recovery Time Objective) asks, "How fast can I get back to work?"
Let's consider an example. A server fails at noon.
You need both to have a full plan. High-end systems aim for "zero RPO" and "zero RTO," but that costs a lot of money. Most businesses find a middle ground that keeps them safe without breaking the bank.
Several things will dictate how you set your targets. First, look at your industry regulations. Some laws require certain types of businesses to keep data very current. If you fail to meet these, you could face huge fines.
Second, consider the cost of downtime. How much money do you lose every hour your team can't work? If that number is high, you need a very short RPO. This forces you to invest in better backup technology.
Finally, think about your storage capacity. If you want a 5-minute RPO, you will be saving a lot of data. Do you have the cloud space or physical hard drives to handle that? This is where many companies struggle. They want no data loss, but they don't want to pay for the storage required to keep those constant snapshots.
Also Read: What is VPN Gateway? 7 Key Ways It Secures Your Network
We live in a great time for tech. In the past, we used tapes that we moved to a vault once a week. Now, we have cloud-based tools that offer "Continuous Data Protection" (CDP).
CDP is the gold standard for Recovery Point Objective management. It captures every change to your data in real-time. This allows you to roll back to almost any second before a disaster hit. It is like a "Time Machine" for your whole company.
Other tools use "Snapshots." This takes a picture of your data at set intervals, like every 15 minutes. This is often more affordable than CDP but still provides a very tight RPO. Which one fits your budget?
It is easy to write a number on a piece of paper. It is harder to make it happen. One big challenge is "Data Gravity." As your company grows, you have more data to move. If your internet connection is slow, you might not be able to send backups to the cloud fast enough to meet a 15-minute RPO.
Another issue is system performance. Constant backups can slow down your computers. If your employees can't work because the backup software is hogging all the RAM, your "safety" is actually hurting your productivity.
Thus, we can say that RPO is a balancing act. You want it to be as short as possible, but it must be realistic for your hardware and your staff.
To get a better handle on your situation, try asking these questions during your next meeting:
These questions move the conversation from "Are we backed up?" to "How resilient are we really?"
Setting a clear Recovery Point Objective is the difference between a minor hiccup and a business-ending disaster. It gives your team a target and your business a shield. By understanding your data tiers and investing in the right frequency of backups, you ensure that a "bad day" doesn't become the "last day" for your company.
In our view, protecting your data is about more than just technology; it is about respecting the hard work you and your clients put in every day. We believe in building systems that aren't just "robust," but truly resilient. Our team focuses on your specific needs to ensure your data is always right where you left it.
Contact Us to Secure Your Future
There is no single "good" number. A bank might need 0 seconds, while a personal blog might be fine with 24 hours. It depends on your "data loss tolerance."
A shorter RPO usually costs more. It requires more frequent backups, more storage space, and faster network speeds to move that data.
Yes, this is called "Synchronous Replication." Data is written to two places at the exact same time. It is expensive but prevents all data loss.
Absolutely. Even if your data is in the cloud, you should know how often the provider backs it up. You might need a third-party tool to reach your desired RPO.
The business owners or stakeholders should decide based on risk. The IT team then implements the technology to meet that goal.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts