.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

In 2025, domain spoofing remains a significant threat with over 90% of the world's top email domains vulnerable to spoofing, enabling cybercriminals to launch sophisticated phishing attacks. Only about 7.7% of the top 1.8 million email domains have implemented strict DMARC policies to effectively block spoofing attempts.
Most domains either have weak or no DMARC policies, resulting in easy email spoofing opportunities for attackers. Around 62% of phishing attacks in 2025 used domain spoofing or lookalike URLs as a tactic to deceive recipients.
Domain spoofing and lookalike URLs are key parts of modern phishing. Around 62% of all phishing attacks in 2025 used these methods to trick people.
Further, the sheer number of attacks is alarming:
Domain spoofing attacks are becoming harder to stop. Attackers are abusing legitimate cloud hosting services. They host their phishing sites there. This practice helps them bypass common network defenses.
Now, we also see AI-powered phishing making things worse. It is designed to create highly convincing fake emails and spoofed websites. This clearly contributes to a rise in identity-based phishing incidents.
Despite efforts to encourage DMARC adoption, progress is slow. Over 50% of domains still lack basic email authentication records. Also, enforcement visibility remains low.
This widespread vulnerability fuels continuous phishing campaigns. These campaigns lead to credential theft, financial fraud, and business email compromise attacks that are costing billions worldwide.
In this blog, we are going to understand what exactly is domain spoofing and how you can prevent it.
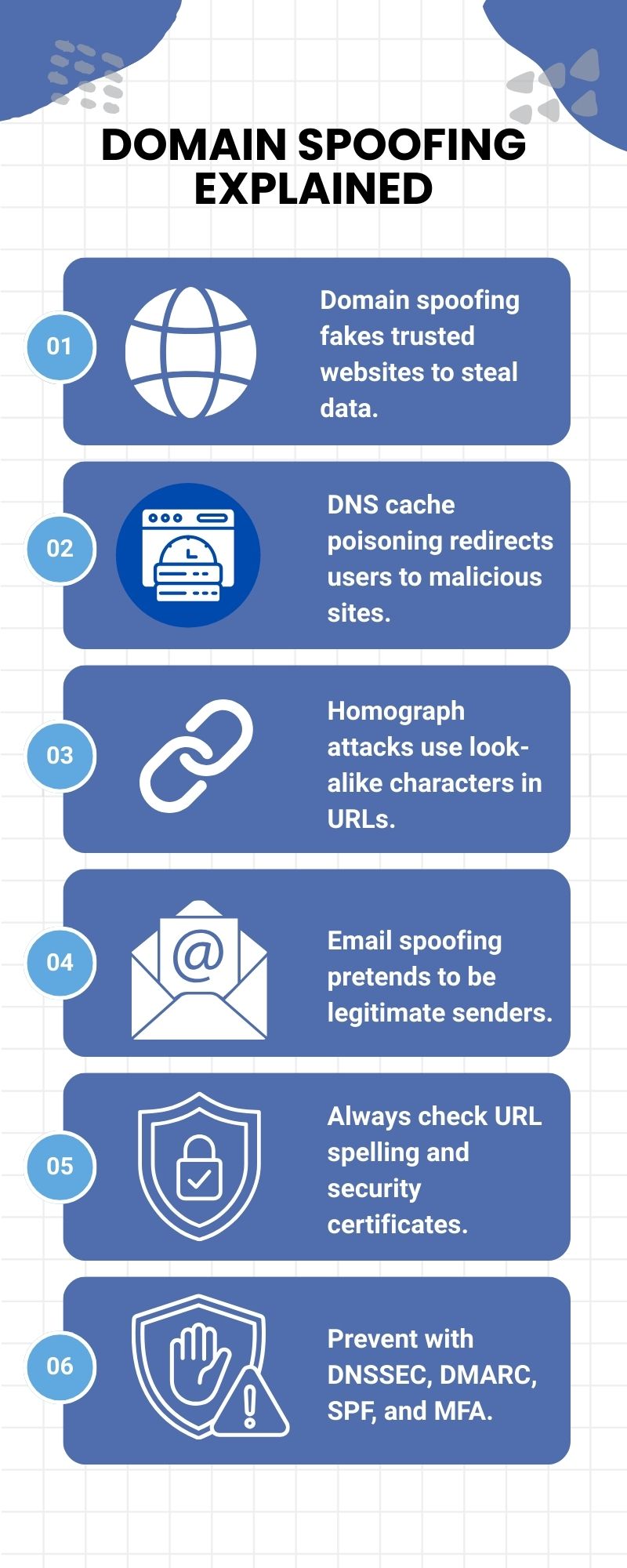
Domain Spoofing refers to the act of faking a website’s identity. It makes the malicious site look like a legitimate, well-known one. The threat actor spoofs the website's address. They want you to believe you are visiting the real bank or email provider. You should note here that this is a type of deception.
Domain spoofing often creates a digital illusion. This illusion steals your attention and your private information. The functional purpose of domain spoofing is almost always financial gain. It is also used for planting malware on your computer.
As the name suggests, Domain Spoofing uses a fake domain name. This fake domain name looks very much like the real domain. Consequently, you enter your login details on the malicious website. Always remember that this is how threat actors gain access to your accounts.
Get Prevention from Domain Spoofing
The core of Domain Spoofing lies in exploiting trust and technical vulnerabilities. To understand domain spoofing in better terms, we must look at how websites connect. When you type a website name, your computer asks for the site's address. This address is a numerical one, like 192.168.1.1. The Domain Name System (DNS) is what translates the name to the number.
Domain spoofing threat actors interfere with this translation process. They want your computer to receive the wrong address. They send you to their fake server instead of the real one. Further, they make the fake site look exactly like the real one.
Now, we will look at how a common type of domain spoofing attack, known as DNS Cache Poisoning, happens.
Here, the threat actor corrupts the local storage of your DNS resolver. This resolver stores past address lookups to speed things up. So, when you look up "www.realbank.com," the poisoned cache gives you the fake IP address. The fake IP address belongs to the attacker's server.
Domain Spoofing is highly effective because you see the correct name in your browser. You trust the name, so you trust the page. The threat actor builds curiosity by making you think the solution is simple. However, the solutions are multi-layered, and we will cover them soon.
There are various types of Domain Spoofing worth understanding:
This is the most technical form of domain spoofing. It targets the DNS server itself. It is a critical attack that manipulates the DNS records.
Consequently, the user is redirected to a malicious IP address without their knowledge. This method is dangerous because it affects many users at once. It is not easily fixed on the user’s side.
This type of domain spoofing targets the user directly. The threat actor uses domain names that look very similar to the real one.
For instance, they might swap a lowercase "L" for the number "1." Or they might use characters from a different alphabet that look identical. Always remember to look closely at the web address. It is to be noted that this form of domain spoofing is used often in phishing emails.
This is when the sender's email address is faked. The email appears to come from a trusted company or person. The actual website link in the email leads to a malicious page.
Resultantly, you click the link and land on a domain spoofing site. This site then tries to steal your information. Email domain spoofing relies on social engineering to work.
In this, the threat actor sits between your computer and the legitimate server. They intercept your traffic. They can then send you to a fake login page. This form of domain spoofing is harder to detect without specific tools.
Domain Spoofing comes in many forms. But they all share the same goal: deception.
Also Read: What Is Antimalware? Your Guide to Threat Defense
Domain Spoofing causes major damage to both individuals and large organizations.
When you fall for domain spoofing, the consequences are severe. Always remember that your information becomes valuable to the threat actor.
The impact is huge for the companies whose domains are being spoofed.
Keep this in mind that the long-term damage from loss of trust is hard to measure. Consequently, companies must actively educate their clients.
How can you protect yourself from falling victim to Domain Spoofing? Take a read of these essential steps. You must remember that being vigilant is your best defense.
The main defense against Domain Spoofing is careful observation. You must learn to check small details.
Also Read: Why Cybersecurity Is a Business Growth Strategy – Not Just a Cost
To understand prevention in clearer terms, we can look at technical tools. These tools offer better protection.
Often, people confuse Domain Spoofing with phishing. While they work together, they are not the same thing. To understand the difference between Domain Spoofing and Phishing in clearer terms, consider the following key points:
| Point of Comparison | Domain Spoofing | Phishing |
|---|---|---|
| Primary Goal | To deceive the user about the origin of the message or website (identity theft). | To trick the user into giving up sensitive information (data theft). |
| Nature of Attack | A technical manipulation of data, like DNS records or URL appearance. | A social engineering attack focused on human psychology and manipulation. |
| Method Focus | Technical trickery involving URLs, DNS records, or sender addresses. | Emotional exploitation through emails, texts, or phone calls (Vishing/Smishing). |
| Relationship | Domain Spoofing is often a tool used to make a phishing attack look more believable. | Phishing is the end goal or the overall attack that may utilize spoofing. |
| Direct Action Needed? | Can occur in the background (e.g., DNS cache poisoning) without the victim clicking anything. | Requires the victim to take an action, such as clicking a link or downloading a file. |
| Appearance | The website URL looks legitimate, or the DNS record is faked to match a real one. | The email/message often creates a sense of urgency, fear, or overwhelming reward. |
| Scope of Deception | Specific to forging an identity or address (email, IP, domain, caller ID). | Broader—it is the entire fraudulent communication process (the "bait"). |
| Technical Requirement | May require exploiting network protocols or DNS vulnerabilities. | Primarily requires strong social tactics and minimal technical skills to set up. |
| Legal Status | Considered a method of impersonation or identity fraud. | Considered a direct act of fraud or attempt to commit fraud. |
| Target | Often targets the computer or network to bypass security mechanisms (like DNS servers). | Specifically targets the human user to exploit their trust and emotion. |
Also Read: Cyber Insurance & Cybersecurity – Why SMBs Need Both to Survive in GCC & Africa
Email domain spoofing is a huge risk for businesses. It damages their brand name. We and you must work to prevent this.
There are three key protocols to combat email domain spoofing:
Always remember that setting up these protocols is complex but necessary. It stops criminals from sending emails that look like they come from your company. This prevents them from using your domain for domain spoofing.
So, we have now covered the complete picture of Domain Spoofing. We understand how this digital deceit works. We know it ranges from complex DNS spoofing to simple URL tricks.
Therefore, when you are asked for login details, take a moment to pause. It preys on rushing. Your attention is the best firewall you have. Always check the URL, the lock icon, and the overall quality of the site.
In summary, protecting your data is a shared task. We aim to provide you with the best knowledge to stay safe. When faced with any doubt, choose caution. This is why we focus on transparency and education. We believe that an informed client is a secure client.
We know you have many questions about this serious threat. Here are answers to some common points:
Domain spoofing is definitely illegal. It is a form of cybercrime and fraud. Threat actors who engage in domain spoofing are often prosecuted for their actions. It is an act of deception used for malicious purposes.
If you click the link, you are on the malicious site. Immediately, do not type in any information. Close the browser window right away. Run a virus or malware scan on your device. Change your passwords right away on a trusted device.
A VPN adds a layer of privacy. However, it cannot stop a DNS spoofing attack directly. This is because DNS spoofing often tricks your DNS resolver before the VPN is fully engaged. But a strong, reputable VPN can sometimes use its own secure DNS servers. This makes you much safer.
Domain spoofing is the act of redirecting you to a fake site. The fake site itself is the website clone. The spoofing makes the cloning successful. They are two parts of the same attack plan.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts