.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Have you ever wondered what hackers see when they look at your business? To be honest, most of us only think about what’s inside our office walls. We buy firewalls and use passwords. But what about the secrets being traded on the dark web? Digital risk monitoring is the shield you didn’t know you needed for everything outside your network.
Imagine someone creates a fake version of your website to steal customer credit cards. Or picture a disgruntled employee posting private company files on a public forum. These aren't just IT headaches; they’re threats to your reputation and your wallet. In my experience, most companies don’t realize they’re exposed until the damage is already done.
So, how do you stay ahead of these invisible "bad actors"? It starts by looking at the world through their eyes. Let’s talk about how digital risk monitoring keeps your brand from becoming a target.
Digital risk monitoring is the process of scanning the open, deep, and dark web for threats against your company. It acts like a digital private investigator that never sleeps. While your internal security focuses on your "house," this tool watches the street and the neighborhood for signs of trouble.
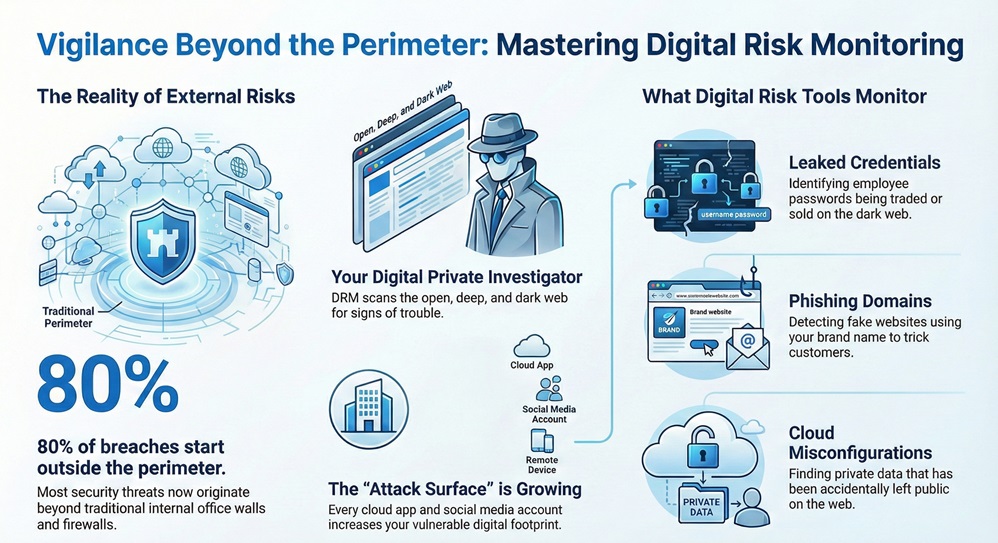
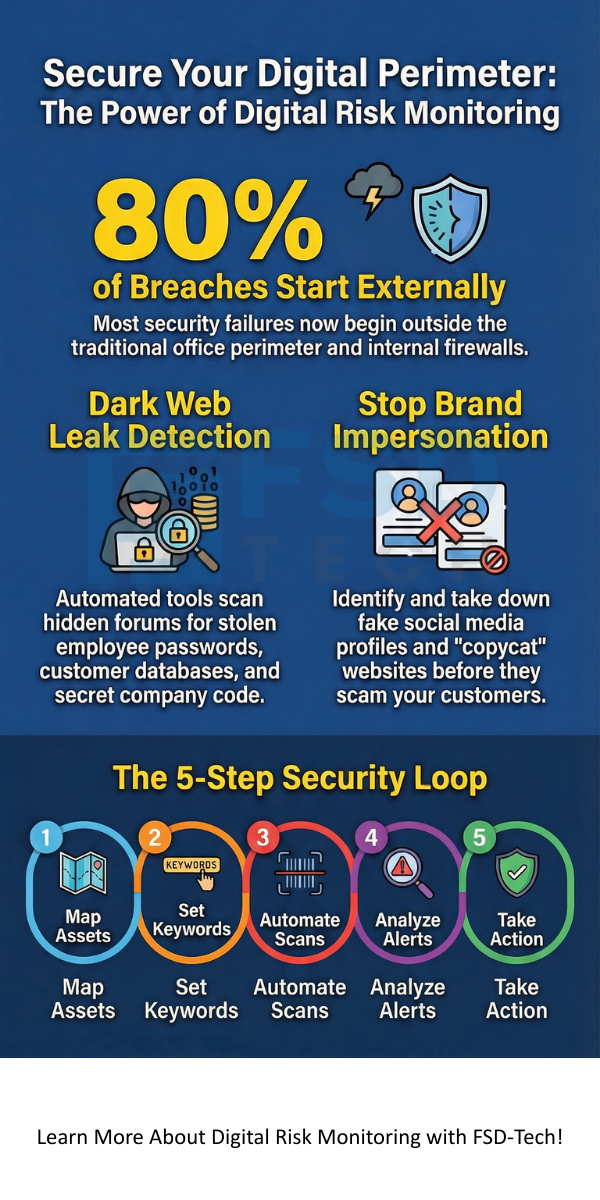
Why does this matter so much now? Well, we’ve all been there—juggling cloud apps, social media, and remote workers. Every new tool you use creates a "digital footprint." The bigger your footprint, the more places there are for a hacker to trip you up. Roughly 80% of security breaches now start outside the traditional office perimeter.
This is why we need to shift our focus. You can't just build higher walls; you have to see who is trying to climb them.
Stop reacting to breaches. Start preventing them. Book your Digital Risk Strategy Session now.
Digital risk monitoring focuses heavily on the "External Attack Surface." Think of this as every digital door and window your company has open to the world. Sometimes, you don’t even know these windows exist. Maybe a marketing team launched a site three years ago and forgot about it. Now, it’s unpatched and sitting there like a "welcome" mat for bugs.
Here is what these tools typically look for:
To be honest, it's a lot to track manually. That's why smart businesses use automated tools to do the heavy lifting. They scan millions of data points every second to find that one needle in the haystack.
Digital risk monitoring isn't just for techies; it’s for your brand’s reputation. We've seen cases where scammers create fake social media profiles using a CEO’s face. They then message employees asking for urgent wire transfers. This is called "Executive Impersonation," and it works surprisingly well.
By watching social media and mobile app stores, you can catch these fakes before they scam your customers. If you find a fake app using your logo, you can take it down fast. This keeps your customers' trust high and your legal team's blood pressure low.
Have you checked if there’s a "copycat" version of your brand out there lately? It happens more often than you’d think.
Also Read: What is Macro Virus? Types, Symptoms & Removal
Digital risk monitoring often involves diving into the parts of the internet that Google can’t see. The dark web is where hackers hang out to trade stolen data like digital trading cards.
In my view, this is the most critical part of the process. If your company’s data shows up here, the clock starts ticking. You might find:
Finding this info early gives you a "head start." You can force password resets or patch a hole before the hacker actually uses it. It’s the difference between a small fix and a national news headline.
Digital risk monitoring works best when it combines fast software with smart people. While AI is great at finding data, it sometimes gets confused. It might flag a legitimate mention of your brand as a threat. That’s called a "false positive."
This is where human intelligence comes in. Experts can look at a threat and say, "Is this a real danger or just noise?" We call this "Cyber Threat Intelligence." It helps you focus on what really matters instead of chasing ghosts. It's like having a filter for your security alerts so you only deal with the big stuff.
Also Read: What is Single Sign-On (SSO)? All You Need to Know
Digital risk monitoring might sound complex, but you can start small. You don't need a massive team to begin protecting your assets.
Fast-forward to six months from now—wouldn't you feel better knowing you have an early warning system? It’s about being proactive rather than reactive.
At the end of the day, your business lives online. Whether it’s your website, your social media, or your email, your digital presence is how the world sees you. We've seen how a single data leak can change everything in an instant. But it doesn't have to be that way.
By using digital risk monitoring, you’re choosing to stay in control. You’re telling your customers that their safety is your priority. Our team believes that every company deserves to operate without the fear of hidden threats. We're here to help you shine a light on the dark corners of the web so you can focus on growing your business.
Protect your reputation and your revenue. Contact our GCC threat hunters to secure your brand today.
No, not at all. An antivirus protects your computer from files you download. Monitoring looks at the entire internet to see if someone is talking about attacking you or selling your data.
Yes! Scammers often target small businesses because they think their security is weak. Many tools are now affordable for smaller teams.
It should be "always-on." Hackers don't work 9-to-5, so your monitoring shouldn't either. Real-time alerts are the gold standard.
Absolutely. Most laws require you to protect customer data. If you find a leak and fix it fast, you show the government you are taking security seriously.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts