
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Data leakage refers to the unauthorized flow of information from within an organization to an external destination or recipient.
Basically, data leakage is nothing but the accidental exposure of sensitive data. This can be anything from internal emails and financial records to customer data and intellectual property. Data leakage is a serious problem. It means that sensitive information is going outside your control.
Data leakage is a major concern for every modern business. Why? Because it can cause huge financial losses. It can also cause legal trouble and damage a company's reputation. Protecting your data is essential in today's digital world.
Let us now understand this concept of data leakage in more detail.
Data leakage is defined as the situation where sensitive data is exposed to unauthorized users. This exposure can happen physically or electronically. The key point here is that the data leaves the secured perimeter of the organization.
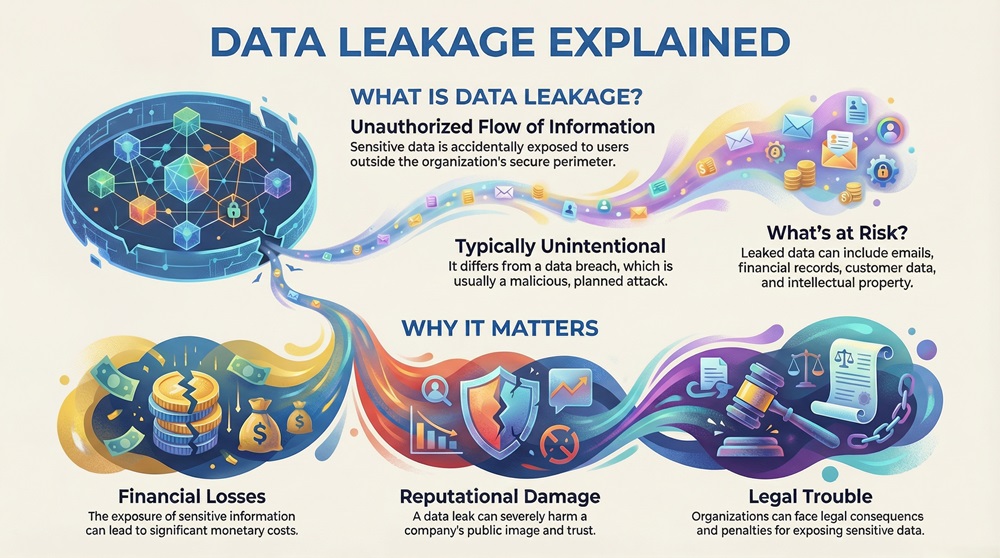
In simple words, data leakage implies that your secret or important information has fallen into the wrong hands. It is important to note that data leakage is usually an unintentional event. This is different from a data breach, which is often a malicious attack.
Secure Sensitive Data with Cato
Many people get confused between a data leakage and a data breach. Let us now understand the basic difference.
| Feature | Data Leakage | Data Breach |
|---|---|---|
| Definition | The unauthorized flow of sensitive data from inside an organization to an external destination, usually due to error or poor controls. | An intentional security violation where an unauthorized party gains access to or steals sensitive data from an organization's systems. |
| Primary Cause | Internal, unintentional actions or system flaws. The major driver is human error or misconfiguration. | External, malicious actions (e.g., hacking, malware) or deliberate internal theft (malicious insider). |
| Intent | Non-malicious or accidental. The person or system exposing the data did not intend to harm the organization. | Malicious or Hostile. The goal is typically to exploit, steal, or disrupt the business. |
| Typical Mechanism | Misdirected email; lost USB drive or laptop; data left in an unsecured cloud bucket; misplaced physical documents; unencrypted network traffic. | Phishing/spear-phishing attacks; brute-force attacks; exploiting zero-day vulnerabilities; injecting malware (ransomware/spyware); compromised user credentials. |
| Data Status | Data is usually exposed and transmitted to an unintended, but often benign, recipient or location (e.g., an employee's personal email). | Data is accessed and exfiltrated (stolen) by a hostile, typically criminal, third party. |
| Detection | Can be detected by Data Loss Prevention (DLP) systems that monitor data in transit, or by auditing cloud permissions and file logs. | Often detected after the fact by credit monitoring agencies, customer complaints, or specialized Security Information and Event Management (SIEM) tools. |
| Remediation Focus | Preventive measures like tightening DLP policies, improving access control, enforcing encryption, and extensive employee training. | Reactive measures like system patch management, incident response, forensic investigation, and notifying affected parties. |
| Example | An employee posts a client spreadsheet to a public, unprotected file-sharing service by mistake. | A hacker exploits a vulnerability in the company's server software and steals all customer credit card numbers. |
Data leakage is mainly due to carelessness or system flaws. On the other hand, a data breach primarily involves a criminal or hostile act. Both, however, lead to the same result: your sensitive data is lost.
Also Read: What is Credential Stuffing? Detection and Prevention
The main reason behind data leakage is often human error. However, a lack of proper systems and controls also plays a major role. We can divide the causes of data leakage into two primary categories: Internal Factors and External Factors.
1. Internal Factors Leading to Data Leakage
Data leakage primarily involves actions taken by people who already have access to the information. These are known as insider threats.
2. External Factors Affecting Data Leakage
While less common than internal factors, external factors also contribute to data leakage.
We can categorize data leakage based on how the information is being transmitted or exposed. Understanding these types helps in finding the right security solutions.
1. Network-Based Data Leakage
This type of data leakage happens when sensitive data travels outside the company network.
2. Storage-Based Data Leakage
This involves the physical or electronic storage of data leaving the secure environment.
3. Endpoint-Based Data Leakage
This is about the loss of data directly from endpoints, such as desktop computers, laptops, and mobile phones.
Also Read: What is an Intrusion Prevention System (IPS)?
Data leakage is not just an IT security issue. It is also a critical problem in the world of machine learning. Data leakage in ML means that information from the training data (the data used to build the model) is included in a way that artificially improves the model's performance.
This is a subtle, but highly important form of data leakage.
The goal of a machine learning model is to predict new, unseen data accurately. When data leakage happens, the model essentially cheats. It performs very well on the test data (the data used to check the model) because it has seen the answers indirectly.
Data leakage in ML can lead to a model that looks excellent during testing but fails completely when deployed in the real world. This is a big problem for businesses relying on accurate predictions.
1. Target Leakage
Target leakage occurs when the training data includes information that is not available in a real-world setting at the time you want to make a prediction. However, this information is strongly related to the target variable (what you want to predict).
Example: Suppose you build a model to predict if a customer will default on a loan. If your training data includes a column called "post-default collection fees," this is a clear case of data leakage. Why? Because, in the real world, you only know the collection fees after the default has happened. Including this data in training makes the model too good because it already has a signal of the outcome.
2. Train-Test Contamination
Train-test contamination is another form of data leakage. This happens when data from the test set (the data the model has not seen) accidentally influences the training process.
To avoid data leakage in ML, you must treat your test set as completely separate. You should only apply transformations that were learned only from the training data.
Also Read: What is Web Application Firewall? | WAF Explained
Since data leakage poses a severe risk, organizations must take proactive steps. Preventing data leakage requires a combination of strong technology, clear policies, and regular employee training.
1. Implement Data Loss Prevention (DLP)
A DLP system is a set of tools and processes designed to prevent data leakage. DLP systems work by:
Data Loss Prevention is primarily a technological solution to data leakage.
2. Strengthen Access Controls
Controlling access minimizes the risk of data leakage. Organizations must strictly follow the Principle of Least Privilege (PoLP).
3. Educate Employees on Data Leakage Risks
Since human error is a major cause, training employees is essential for preventing data leakage.
4. Use Encryption
Encryption makes data unusable even if it falls into the wrong hands.
5. Prevent Data Leakage in Machine Learning
Preventing data leakage in ML requires a careful approach to data handling.
Data leakage is a constant threat in the interconnected digital world. It is clear that every organization must take a serious stance on this issue. Understanding what data leakage is and what causes it is the first step toward building a strong defense.
Data leakage is mainly due to human mistakes or system vulnerabilities. We can reduce these risks by implementing strong measures like DLP systems and effective employee training. By adopting a security-first mindset, you protect your organization's most valuable assets. You maintain customer trust. You also ensure your business stays compliant with data protection laws.
We are committed to helping you understand and implement these robust security strategies.
Contact us today to learn more about our data protection services and how we can help you prevent data leakage within your organization. We focus on providing solutions that secure your data and build a safer digital future for your business.

Data leakage involves the unauthorized exposure or transmission of sensitive data outside a secure perimeter. This often means the data exists in two places: inside and outside. Data loss, on the other hand, means the data is destroyed or permanently inaccessible. While both are security incidents, data leakage is about exposure, and data loss is about destruction.
No. Data leakage can happen in many ways. While email is a very common method, it also occurs through web uploads, lost or stolen USB drives, physical printouts, instant messaging, and even misconfigured cloud storage services. Data leakage occurs anytime sensitive data leaves the authorized environment.
An insider threat is a security risk that comes from within the organization. This includes current or former employees, contractors, or business associates. An insider might cause data leakage accidentally through a mistake or intentionally to cause harm or steal information.
The most important step is a combination of DLP implementation and employee education. Technology, like DLP, can block accidental transmissions. However, since human error causes most data leakage, training employees to recognize risks and follow security protocols is absolutely crucial.
Data leakage in machine learning leads to overly optimistic model performance during testing. The model appears highly accurate but will fail in the real world. This happens because the model unknowingly uses information that would not be available at the time of real prediction. Data leakage in ML creates a misleadingly good model.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts