
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered why your office internet feels slow even with high speed fiber? You might have the best hardware, yet your cloud apps still lag during big meetings. This happens because old networks cannot handle how we work today. Most businesses now use the cloud for everything. But, is your network built for the cloud or for the past?
SD WAN architecture changes how your data moves from point A to point B. It is not just a simple upgrade. It is a new way to think about connectivity. Before we show you exactly how it saves time and money, let us look at what it really is.
SD WAN architecture refers to a software-defined approach to managing a wide area network. In simple words, it separates the network hardware from the software that controls it. This allows you to manage your entire network from one central place.
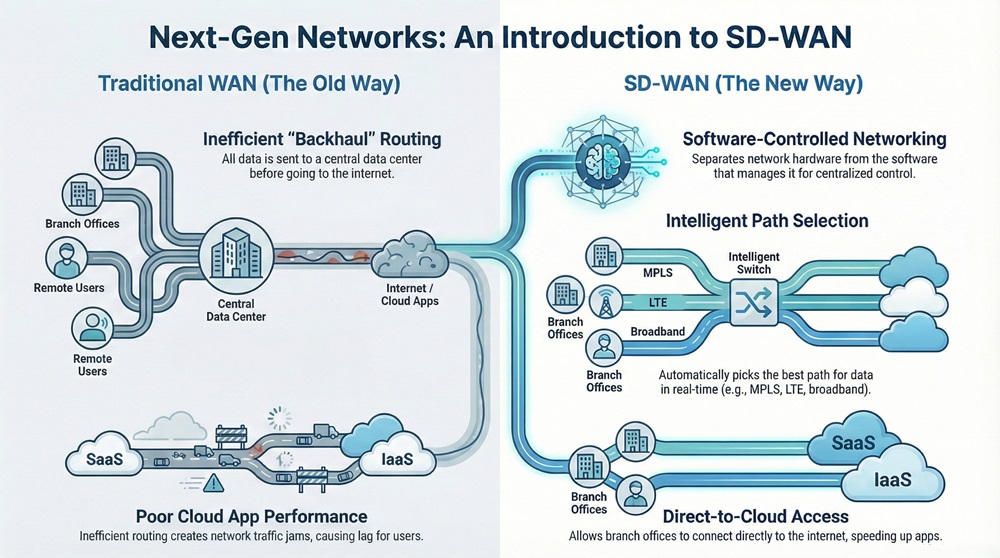
SD WAN architecture uses a centralized control function to direct traffic securely across the WAN. It does not matter if you use MPLS, LTE, or basic broadband. The system picks the best path for your data in real time.
Stop overpaying for MPLS. Get a Custom SD-WAN Cost Savings Estimate
SD WAN architecture solves the problem of traffic jams in your network. Traditional networks send all data to a central data center first. This is like driving twenty miles out of your way just to get onto the highway. It allows your branch offices to connect directly to the internet. This makes your cloud apps run much faster.
To understand SD WAN architecture, you must see how it differs from what you use now.
| Feature | Traditional WAN | SD WAN Architecture |
|---|---|---|
| Control | Decoupled on each router | Centralized software control |
| Transport | Mostly MPLS | Agnostic (MPLS, LTE, Fiber) |
| Traffic Path | Backhauled to data center | Direct internet access |
| Configuration | Manual (CLI) | Automated (Zero Touch) |
| Security | Perimeter-based | Integrated and end-to-end |
| Cost | High (due to MPLS) | Lower (uses public internet) |
How SD WAN works depends on its ability to see every path available. Imagine you have three roads to get to work. One is a private toll road, one is a highway, and one is a local street.
SD WAN can be explained by a smart GPS. The GPS looks at traffic on all three roads. It sends your most important meeting (voice calls) over the private toll road. It sends your emails over the local street. If the highway clears up, it moves your video stream there instantly.
How SD WAN works involves three main layers:
Also Read: What is Cloud Access Security Broker (CASB)?
SD WAN architecture usually focuses on these three layers working together. You no longer have to program every single router in every branch. Instead, you tell the central software what you want.
SD WAN architecture also involves "overlays." The software creates a secure tunnel over your existing internet lines. This tunnel keeps your data safe while it travels across the public web.
SD WAN architecture creates a virtual layer that sits on top of your physical wires. This means you can add a new office to your network in minutes. You do not have to wait weeks for a provider to install a special line. You just plug in a local internet cable and the software does the rest.
SD WAN implementation usually starts with a pilot program. You do not have to switch everything at once. Most companies start by adding an SD WAN appliance to one branch office.
It involves these four steps:
Is SD WAN worth it if you are a small company? The answer depends on your cloud usage. If you use Zoom, Office 365, or Salesforce, you will see a big jump in speed.
Is SD WAN worth it for larger firms? Definitely. It reduces the need for expensive MPLS lines. Many companies save up to 40% on their monthly network bills. You also get better security and less downtime. If one internet provider fails, the system switches to another in less than a second.
Also Read: What is Container Security? Best Practices, Tools, and Risks
The architecture relies on a few moving parts to stay efficient.
SD WAN architecture puts a smart device at the edge of your network. This device checks the quality of your internet every millisecond. It measures "jitter" and "latency." If a connection gets "jittery," the device moves your voice call to a better line before you even notice a glitch.
The architecture includes built-in security. Old networks needed a separate firewall at every location. Now, the security travels with the data.
SD WAN architecture uses encryption to lock your data inside the tunnels. Most systems also include "Stateful Firewalls" and "URL Filtering." This means your employees stay safe from malicious websites even when they are not in the main office.
SD WAN architecture helps your budget in two ways. First, it lets you use cheaper internet connections. You can replace a $500 MPLS line with two $80 broadband lines. You get more speed for less money.
It also saves time for your IT team. They no longer have to travel to branch offices to fix network issues. They can fix everything from their desk at home. This reduces "truck rolls" and keeps your experts focused on big projects.
Can I keep my old routers?
In many cases, yes. You can place an SD WAN device behind your current router. However, most people find it easier to replace old routers with new SD WAN edge devices.
Does SD WAN replace the internet?
No. SD WAN makes your internet connections work better together. It manages the "service" you buy from providers like AT&T or Comcast.
Is it hard to manage?
Actually, it is easier. You use a single dashboard to see your entire network. If a branch in another city goes offline, you will see a red light on your screen immediately.
SD WAN architecture comes in three main flavors:
Also Read: What is Network Sniffing? Attack and Prevention
SD WAN architecture should fit your team's skills. If you have a large IT team, you might want to manage it yourself. If you are a small shop, a managed service is usually better.
How is SD WAN implemented when you have a complex setup? You use a "hybrid" approach. You keep your MPLS for very sensitive data. You move everything else to the SD WAN. Over time, as your MPLS contracts end, you can move fully to the software-defined model.
How is SD WAN implemented without breaking the bank? Start with your most remote site. These sites usually have the worst internet. Improving the connection there will show you the value of the tech quickly.
SD WAN architecture is the future of business networking. It gives you the flexibility of the cloud with the security of a private line. You get better performance, lower costs, and happier employees.
Is SD WAN worth it for your specific needs? If you want a network that grows as fast as your business, the answer is yes. It takes the guesswork out of connectivity and lets you focus on your work.
Our team at FSD-Tech believes in making technology work for people. We focus on clear solutions that help your business stay connected without the headache of old systems. We value transparency and your success above all else. Book a Free Network Audit
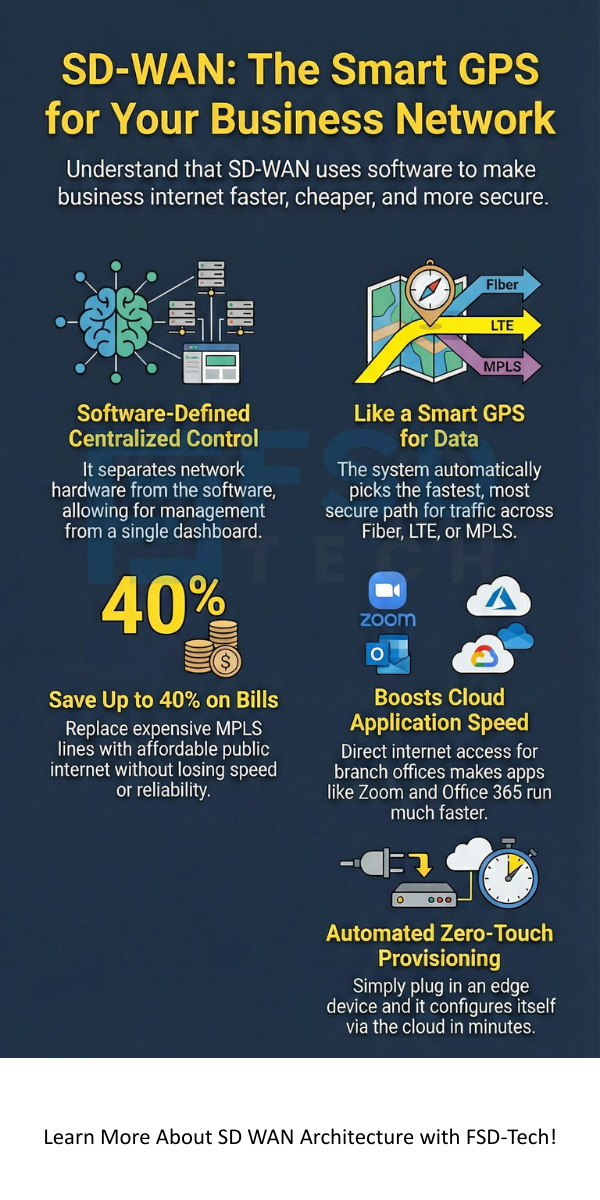
The main goal is to provide a high-quality user experience for cloud applications while reducing network costs and complexity.
It uses end-to-end encryption and integrated firewalls to protect data as it moves across public and private internet lines.
Yes. SD WAN can use 5G as a primary or backup connection, making it great for mobile offices or retail kiosks.
No. It is "provider agnostic," meaning it can mix and match connections from any company.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts