
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

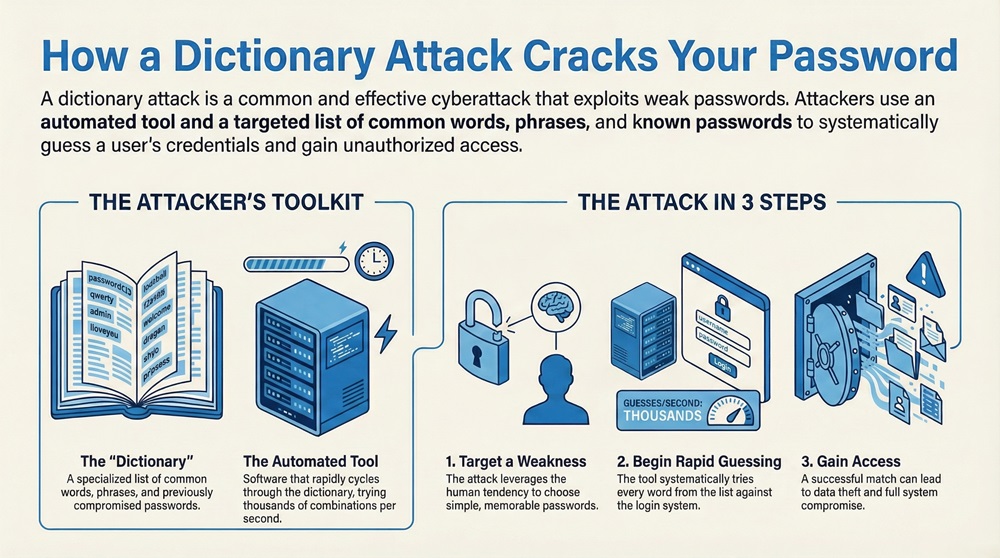
A dictionary attack is a type of cyberattack that involves an attacker trying to crack a password or passphrase by inputting words from a list. This list is essentially a "dictionary" of common words, phrases, and previously compromised passwords. The attacker uses an automated tool to quickly cycle through these words until a match is found. This is a very common method used in password cracking.
The two essential components of a successful dictionary attack are the password list and the automated tool. The password list contains all the possible words and phrases that the attacker will try. The automated tool handles the speed and volume of attempts, trying thousands of combinations per second against a target's login portal or hashed password file. This whole process leverages human tendencies to choose simple, memorable passwords.
To know more about this specific form of brute-force attack, read below. This content explains what a dictionary attack is, how it works, its different forms, and how you can defend your systems against this cybersecurity threat.
A dictionary attack can be defined as an attempt to breach a secure system by repeatedly trying potential passwords from a specific, targeted list. This attack exploits weak passwords that are simple words found in a dictionary, which is why it has this name. It is a straightforward yet highly effective hacking technique against users who choose common words for their login credentials.
In simple words, the dictionary attack is a systematic way to guess passwords. It relies on the simple fact that many people use passwords that are easy to remember. These easy-to-remember passwords often include words like "password," "welcome," or names, which are all included in the attacker's specialized wordlist. Therefore, the goal of the dictionary attack is to find a match in this list before the system locks the account.
It must be noted that these attacks are a major cyber threat to organizations and individual users alike. Successful attempts can lead to unauthorized access, data theft, or system compromise. Is your password strong enough to withstand a dictionary attack? We will look at how to secure your accounts later.
The figure below shows the basic concept of a dictionary attack.
As you can see in the figure, the attack relies on a predefined list of words instead of trying every single possible combination of characters. This makes it much faster than a pure brute-force attack.
Let us now understand the mechanism behind a dictionary attack. The way the dictionary attack works is a simple three-step process. First, the attacker needs a target and a special wordlist. Second, they use a tool to automate the process. Third, the tool submits the words as passwords until it finds the correct one.
The process of a dictionary attack involves:
Here, it must be understood that even small variations, such as adding numbers or symbols to common words (e.g., "P@ssword1"), are often included in a modern, sophisticated dictionary attack list. These modifications are called hybrid attacks, and they greatly increase the attack's effectiveness.
Let us now discuss the speed advantage of this password attack. Since the attacker is not trying random strings, the number of guesses is dramatically reduced. For example, trying every possible eight-character password can take years. However, a dictionary attack with a list of one million common words takes only a few minutes to complete the checking process.
Also Read: What is a Next Generation Firewall (NGFW)? Why UAE/GCC businesses need it?
To understand the full scope of dictionary attack security concerns, it is necessary to go through its various types. This form of password attack can be classified based on the wordlist and the target. The main types include the basic dictionary attack, the hybrid attack, and the specific dictionary attack.
Basic Dictionary Attack
This is the simplest form of the dictionary attack. It involves using a straightforward list of common words, names, and phrases, which are the same as found in any standard dictionary.
Hybrid Dictionary Attack
A hybrid attack is a more effective method that combines the wordlist with a small brute-force attack component. This is one of the most common forms of password cracking.
Specific Dictionary Attack
This type of dictionary attack uses a wordlist built specifically for a target or organization. This technique is sometimes called a focused attack.
It is to be noted that all these types of dictionary attacks show why relying on common terms, even with slight modifications, makes your authentication credentials vulnerable.
Following are the key characteristics that define a dictionary attack and make it a persistent cybersecurity threat. These features explain its nature as an efficient password guessing method.
One must note here that the continuous growth of huge wordlists, sometimes containing billions of entries from past data breaches, has made the dictionary attack more powerful than ever before.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
| Basis for Comparison | Dictionary Attack | Brute-Force Attack |
|---|---|---|
| Meaning | Tries to guess passwords from a pre-compiled list of words. | Tries every possible character combination to guess the password. |
| Nature | Highly targeted and efficient guess work. | Exhaustive and untargeted attempt. |
| Examples | Trying "secret123," "password," "admin." | Trying "aaaaa," then "aaaab," then "aaaac," and so on. |
| Function/Purpose | To crack weak passwords quickly. | To crack any password, given enough time and power. |
| Based on | Human tendency to choose common, memorable passwords. | Mathematical possibility of character combinations. |
| Method | Uses a specialized wordlist. | Uses an algorithmic character generator. |
| When Used/Application | Used when speed is critical and passwords are expected to be weak. | Used when the password length is known or when a dictionary attack fails. |
| Limitations | Fails against long, random passwords. | Requires enormous computational power and time. |
While the dictionary attack is efficient against weak passwords, it also has certain limitations that the attacker must face. These disadvantages make the attack less effective against systems with strong security measures.
Therefore, strong password policies and multi-factor authentication are critical in neutralizing the threat of a dictionary attack.
The dictionary attack has several applications, most of which are malicious. However, it is also used in a positive way for security testing. The main use cases center around gaining unauthorized access.
For instance, consider a company, Alpha Corp, that uses simple passwords. An ethical hacker might run a dictionary attack during a security audit. If the attack successfully compromises 50 employee accounts, it proves that Alpha Corp needs to enforce a stronger password policy.
Also read: What is an Intrusion Detection System (IDS)? Components and Types
Defending against a dictionary attack involves a mix of user education and technical safeguards. You need to focus on making the password difficult to guess and making the attack detectable. Following are the most significant measures to protect against this cyber threat.
Strong Password Policy
The first and most vital defense is to enforce a strong password policy. If passwords are not words found in a dictionary, the attack is defeated immediately.
Account Lockout Policies
This is a technical safeguard that stops the automated nature of the dictionary attack.
Multi-Factor Authentication (MFA)
This security layer makes a huge difference. Even if the attacker manages to find your password using a dictionary attack, they still cannot access your account.
Salting and Hashing Passwords
For systems that store passwords, never store them in plain text. Always use strong, modern hashing algorithms combined with salting.
Please refer to the example below.
Example: If your password is "flower," a salt is added to it, such as "flower" + "xY7z." This new, combined string is then hashed. Every user has a different salt, making it so that the attacker must perform a separate, time-consuming dictionary attack for every single password hash they steal, rather than comparing them all to a single, pre-calculated list.
A dictionary attack is a powerful and efficient password attack that targets the weak link in almost all security systems: human beings. It leverages the tendency of users to choose common, easily remembered words for their authentication credentials. This type of cyber threat is a specialized version of a brute-force attack, but it achieves high success by focusing on a probable list of words rather than random characters.
Therefore, the key to successful defense lies in adopting a mindset of zero tolerance for simple passwords. Enforcing long, complex, and random passwords, coupled with technical safeguards like multi-factor authentication and strict account lockout policies, is essential.
Our core value at FSD-tech is to empower you with the knowledge to stay secure in a complex digital world. We provide solutions and insights to ensure that your digital assets are not just protected, but fortified against evolving cybersecurity challenges.

A brute-force attack tries every possible combination of characters until it finds the password. A dictionary attack, conversely, only tries words and variations from a predetermined list of common passwords. The dictionary attack is much faster but less comprehensive than a full brute-force attack.
No, conducting a dictionary attack against an account you do not own or are not authorized to test is illegal hacking and a serious cybercrime. However, security professionals use it legally for penetration testing to find system weaknesses with explicit permission.
Hackers use dictionary attacks because they are very efficient and have a high chance of success against accounts with poor password hygiene. The tools are easy to use, and the method requires less computing power compared to other types of password cracking.
Yes, multi-factor authentication (MFA) is one of the most effective defenses. Even if a dictionary attack successfully guesses the password, the attacker cannot complete the login process without the second factor (like a code from your phone), which they do not have.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts