
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how big apps run smoothly without crashing? They often use small, portable units called containers. These units hold everything an app needs to work. But what happens if someone tries to break into those units? You might feel safe using them, but containers have their own set of risks. Are you protecting your digital assets correctly?
Container security involves much more than just locking a digital door. It is a full process of protecting the entire life cycle of a container. This starts from the moment you build it until it stops running. It covers the tools, the rules, and the steps you take to keep your data safe from hackers.
Let us look at why this matters for your business. When you use containers, you share the same host system. If one container is weak, the whole system could be at risk. Would you like to know how to stop that from happening?
Container security refers to the practice of protecting containerized applications and the infrastructure they run on. It is a continuous process that integrates into every stage of development. Because containers are meant to be fast and temporary, traditional security often fails to keep up.
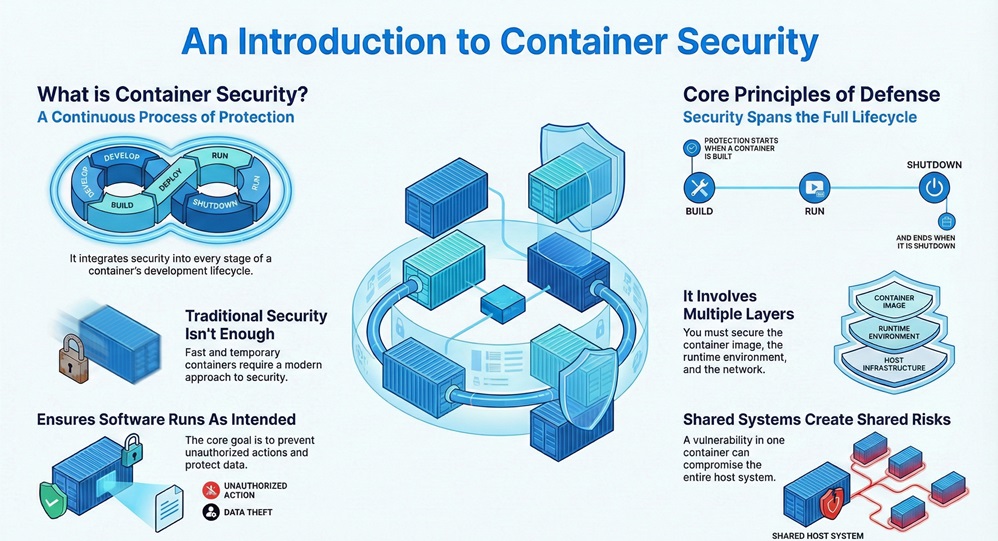
It requires you to look at multiple layers. These layers include the container image, the runtime environment, and the network. You must ensure that each part is hard to break. In simple words, it is about making sure your software runs only as intended and nothing else.
It is important to note that container security is not a one-time setup. It is a habit you must build into your daily workflow. Do you have a plan to monitor your containers after they go live?
To understand what is container security, we should compare it to something familiar like Virtual Machines (VMs). While both help run apps, they handle safety differently.
Basis for Comparison Table
| Basis for Comparison | Virtual Machines (VMs) | Container Security |
|---|---|---|
| Isolation Level | High (uses a full Guest OS) | Medium (shares the host OS kernel) |
| Attack Surface | Larger due to full OS | Smaller but more concentrated |
| Speed | Slow to boot and scan | Very fast to start and monitor |
| Resource Usage | High (heavy on RAM/CPU) | Low (efficient and lightweight) |
| Persistence | Long-lived | Often temporary and "ephemeral" |
Container security helps you prevent data leaks and service downtime. As more companies move to the cloud, the "Container Security Initiative" (CSI) concept often comes up. Originally, this term related to shipping trade, but in IT, it focuses on the global standard for keeping containerized data safe.
It is vital because containers are often "transparent" to traditional firewalls. Hackers can use a single flaw in an image to move through your entire network. This is why you need specific tools to watch what happens inside the container.
Also Read: What is Network Sniffing? Attack and Prevention
Container security tools are specialized software designed to find and fix holes in your system. You cannot rely on standard antivirus for this task. These tools look for "vulnerabilities" or weak spots in the code before you even launch the app.
Container security tools like Qualys, Tenable, or Trend Micro provide deep visibility. They can see inside the "layers" of a container. Have you checked if your current tools can scan for hidden malware in your registry?
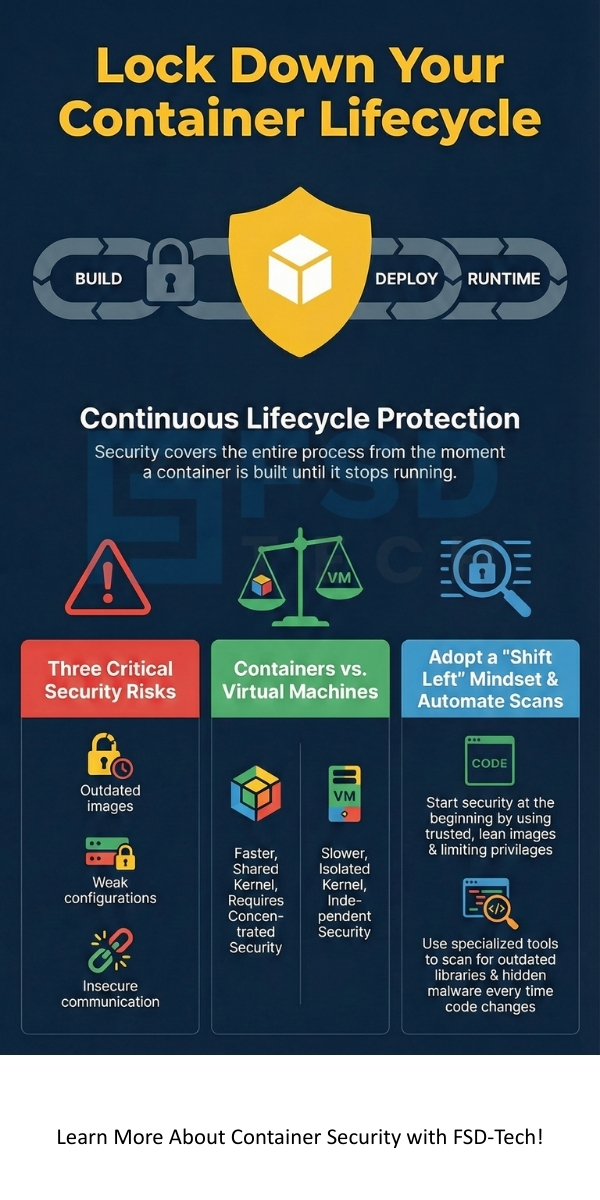
Container security best practices are the rules you should follow to stay safe. If you follow these, you lower your chances of a successful attack. It starts with a "Shift Left" mindset. This means you think about safety at the very start of your project.
It include using "lean" images. This means you only include the files the app needs to run. The fewer files you have, the fewer places a hacker can hide. Let us look at some specific steps you can take.
Also Read: What is Kerberoasting Attack? Detection & Prevention
A container security scan is a detailed check of your container image. It looks for known bugs or "CVEs" (Common Vulnerabilities and Exposures). Think of it like a health checkup for your software.
It should happen every time you change your code. Automated scanners can stop a "bad" image from ever reaching your customers. This saves you time and keeps your reputation clean.
A container security solution is a complete package that handles everything for you. Instead of buying five different tools, a single platform manages your risks. This is often the best choice for growing companies.
It provides a "single pane of glass." This means you can see the safety status of all your apps in one dashboard. It simplifies your work and helps your team respond faster to threats.
Also Read: What is Cloud Access Security Broker (CASB)?
When opening and closing a security container, you must follow strict protocols. While this phrase sometimes refers to physical safes, in the IT world, it means managing the "lifecycle" of your digital container.
When opening and closing a security container in a cloud environment, you must manage access keys carefully. You should ensure that when a container "closes" (terminates), all temporary data is wiped clean. This prevents "data remnants" that hackers could find later.
What is container security without host security? The host is the physical or virtual server that holds your containers. If the host is weak, the containers are not safe. You must harden the host OS by removing unnecessary services.
Container security logic says you should use a "Container-Optimized OS." These are stripped-down versions of Linux built specifically to run containers. They have a very small attack surface, which makes them much harder to hack.
Container security is a vital part of modern software growth. It involves using the right container security tools and following container security best practices. By integrating a container security scan into your daily routine, you protect your company from hidden dangers.
It is not just a technical task; it is a promise to your users. It shows you care about their data and the stability of your services. When you choose a strong container security solution, you are investing in the future of your business.
We believe that every company deserves a safe digital environment. Our team focuses on providing clear, actionable advice to help you stay ahead of threats. We put our clients first by staying updated on the latest security trends. Are you ready to make your containers unshakeable? Reach us now
The main goal is to protect the application and its data from threats. It ensures that the container environment remains stable and private throughout its life.
Yes, they are different but related. Docker security focuses on the individual container and its image. Kubernetes security focuses on how those containers talk to each other and how they are managed at scale.
It is not recommended. Traditional antivirus often lacks the visibility to see into container layers or handle the fast-paced nature of container starts and stops.
You should scan every time a developer "commits" new code. Continuous scanning is the only way to stay ahead of new threats that emerge daily.
A distroless image contains only your application and its dependencies. It does not contain a shell, package manager, or any other tools a hacker might use once they get inside.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts