
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025
%20in%20Cato-01.jpg&w=3840&q=75)
Managing who can access what—and with how much privilege—is a cornerstone of secure operations in any IT environment. With Cato Networks, Role-Based Access Control (RBAC) allows IT teams to enforce least-privilege access across administrators, service providers, and auditors, ensuring operational security and compliance.
This guide walks through the RBAC implementation steps in the updated Cato Management Application (CMA), outlines real-world use cases, and offers tips for structuring access based on team roles.
In the latest version of Cato’s Management Application:
Here, you’ll see a dropdown for selecting predefined roles or customizing access.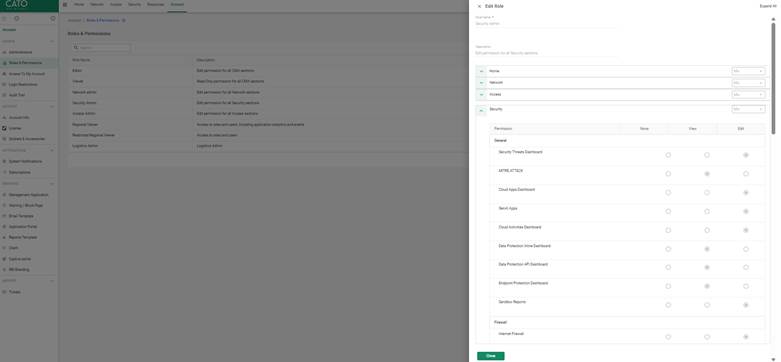
As of the latest release, Cato supports the following built-in roles:
Each role determines what tabs, data, and actions are visible and executable.
Use the following table to align user roles with IT roles:
| Team Member | Suggested Role | Justification |
| CISO / Compliance | Viewer | Needs audit access, not modification rights |
| Network Engineer | Network Admin | Full access to topology, rules, routing |
| Security Analyst | Security Admin | Manage threat dashboard, FWaaS, policies |
| MSP Technician | Custom Role | Limit to specific clients or regions |
| Tier 1 Support | Viewer or Custom | Access to logs, alerts—but no policy changes |
Let’s say you manage an internal IT team for a regional office. You want your Tier 2 engineer to troubleshoot firewall rules but not modify WAN configurations.
Steps:
This setup allows engineers to remain effective without overexposing critical infrastructure settings.
RBAC ensures only the right people have access to the right controls—no more, no less. Start structuring access today in your Cato CMA.
Yes, you can toggle individual permissions for a Custom Role during user creation.
Yes. You can edit user roles anytime via the User Management tab.
Yes, all user actions are logged in the Audit Trail for review.
Not directly. But you can control access scope via Custom Role and filtering policies.
MFA is user-based. You can enforce it during account setup regardless of role.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts