
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever worried about losing every file on your computer in a single second? Imagine opening your laptop to find a bright red screen. It tells you that your photos, documents, and business files are locked. You cannot open them. To get them back, you must pay a fee, usually in digital currency like Bitcoin. This is not a glitch. You are facing ransomware.
Ransomware is a type of malicious software, or malware, that blocks access to a computer system or data. Hackers use it to extort money from victims. They hold your digital life hostage until you meet their demands. But how does this happen, and can you truly protect yourself?
Ransomware works by using encryption to scramble your files. Encryption is normally a good thing. It keeps your data private. However, in the hands of a criminal, it becomes a weapon. The attacker holds the only key to unlock the data.
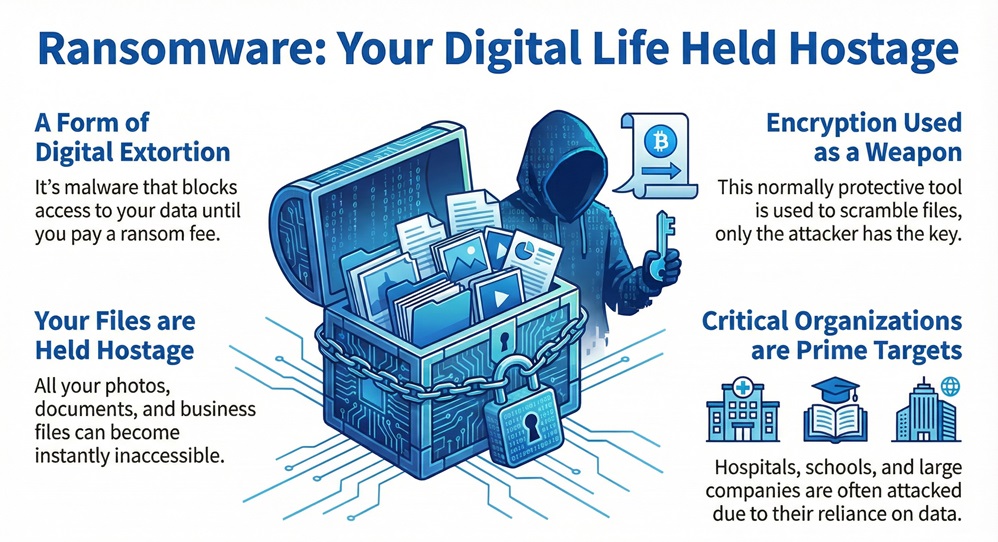
These attacks do not just target individuals. They hit hospitals, schools, and large companies. Why do hackers do this? They know these groups rely on their data to function. If a hospital cannot see patient records, lives are at risk. This pressure makes victims more likely to pay the ransom quickly.
To understand the threat, we must look at the different ways these programs behave. Not all attacks look the same.
| Feature | Locker Ransomware | Crypto Ransomware |
|---|---|---|
| Primary Goal | Blocks access to the entire device. | Encrypts specific files and folders. |
| Data Status | Files remain unencrypted but inaccessible. | Files are scrambled and unreadable. |
| Visibility | You see a lock screen or fake legal notice. | You can see the files but cannot open them. |
| Impact | Prevents you from using the computer at all. | Prevents you from using important data. |
| Recovery | Often fixed by removing the lock malware. | Requires a decryption key or data backup. |
Ransomware refers to the specific category of malware designed for financial gain through data kidnapping. It has evolved significantly over the last decade. In the early days, these programs were simple. They might just display a pop-up that was hard to close. Today, they are sophisticated.
These attacks now often use a "double extortion" tactic. The hackers do more than just lock your files. First, they steal a copy of your private data. Then, they encrypt the original files on your server. If you refuse to pay for the key, they threaten to leak your private information online.
Ransomware actors operate like a business. Some even offer "Ransomware as a Service" (RaaS). In this model, professional developers write the code. They then rent it out to other criminals. This allows people with very little technical skill to launch major attacks.
Also Read: What Is a Zombie Computer? Botnet Threats Guide
Ransomware enters your system through several common paths. Do you often click on links in emails from people you do not know? That is a primary risk.
Ransomware follows a specific sequence of events. Understanding these steps helps you spot an attack before it finishes.
1. Infection and Distribution
Ransomware must first find a way into the network. As we mentioned, this usually happens through phishing or unpatched software. The goal is to get a small piece of code running on a single computer.
2. Command and Control (C2)
Ransomware then connects back to the hacker's server. This is called a Command and Control server. The malware sends information about your computer to the hacker. It then receives instructions and the "public key" used for encryption.
3. File Discovery
It begins to look for valuable files. It searches for Office documents, PDFs, images, and databases. It also looks for network drives. If your computer is connected to a company server, the malware will try to spread there too.
4. Encryption
It starts the encryption process. It replaces your original files with encrypted versions. These files often have a new extension, like .locked or .crypted. During this time, your computer might feel slow because the processor is working hard to scramble the data.
5. The Ransom Note
Ransomware finally reveals itself. It drops a text file or changes your desktop wallpaper. The note explains what happened. It gives you a deadline and a link to a "leak site" or a payment portal.
Also Read: What is Network Sniffing? Attack and Prevention
Ransomware creates a massive ripple effect. It is not just about the money lost to the ransom. The real cost is much higher.
It causes downtime. When a business loses its data, work stops. Employees cannot log in. Customers cannot buy products. This loss of productivity can bankrupt a small company. According to CERT-In, the number of attacks in India has increased year over year, targeting critical sectors like finance and energy.
Ransomware also damages your reputation. If you are a doctor and you lose patient records, patients lose trust in you. If you are a bank and hackers steal customer data, your brand is ruined.
Ransomware recovery is expensive. Even if you do not pay the ransom, you have to hire experts. You must clean your systems, buy new hardware, and fix the security holes. This often costs ten times more than the actual ransom demand.
Ransomware is unique because it interacts with the victim. Most viruses try to stay hidden.
Also Read: What is Advanced Persistent Threat (APT)?
Ransomware prevention is easier than recovery. You can take simple steps today to keep your data safe.
Maintain Regular Backups
Ransomware loses its power if you have a backup. You should follow the 3-2-1 rule. Keep three copies of your data. Use two different types of media (like a hard drive and the cloud). Keep one copy "offline" or away from your network. If the malware cannot reach your backup, it cannot lock it.
Update Your Software Constantly
It often uses old bugs to enter systems. When you see a "system update" notification, do not ignore it. These updates include security patches. They close the doors that hackers use to get inside.
Use Multi-Factor Authentication (MFA)
Ransomware actors love stolen passwords. MFA adds a second layer of security. Even if a hacker has your password, they cannot log in without the code from your phone. This stops most RDP-based attacks.
Train Your Team
It often relies on human error. Do you know how to spot a fake email? You should look for strange sender addresses and urgent language. Teaching your employees to be skeptical is your best defense.
Ransomware attacks are scary, but you must stay calm. Acting quickly can limit the damage.
Ransomware is a growing threat in our digital world. It targets our most valuable asset: information. By understanding how these attacks work, you can build a stronger defense. Remember, security is not a one-time task. It is a habit. You must stay alert, keep your software updated, and always verify your backups.
Our team believes in a safer digital future for everyone. We focus on providing clear, actionable advice to help you stay ahead of cybercriminals. Your data security is our priority. We are here to help you navigate these challenges with confidence and integrity.

Ransomware spreads mostly through phishing emails. These emails contain attachments or links that download the malware when clicked.
It can sometimes be blocked by modern antivirus programs. These tools look for "behavior" rather than just a list of known viruses. However, hackers constantly change their code to bypass these tools.
Ransomware experts advise against paying. You are dealing with criminals. There is no "customer service." Many victims pay the money and never receive the decryption key.
It can encrypt a whole computer in just a few minutes. However, the hackers might have been inside your network for weeks before they started the encryption.
Ransomware is a serious crime. Using malware to extort money is a global offense.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts