
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how your private messages stay private? In the world of digital safety, symmetric encryption plays a vital role. It is a fundamental method used to protect data. But how does it really work, and why should you care about it? Let's explore this essential tool.
Symmetric encryption can be understood as a type of cryptography where only one secret key is used. This single key handles both symmetric encryption and decryption tasks. This means the sender and the receiver must share the same "password" or key before they can communicate safely.
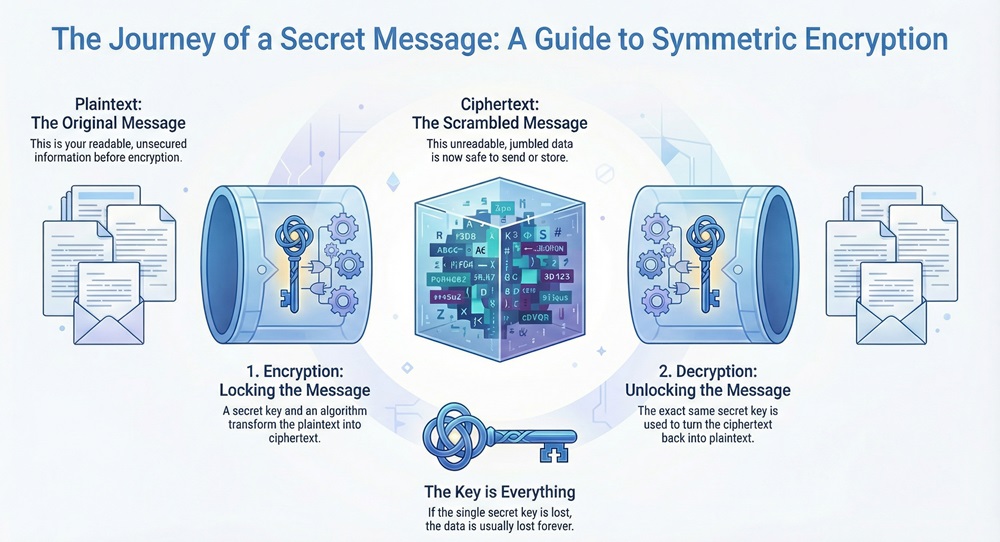
It is one of the oldest and most reliable methods in information security. In simple terms, it works like a physical lock and key. You use one key to lock a box. You must give that same key to your friend so they can open it. If anyone else finds the box, they cannot see what is inside without that specific key.
Consult with our Encryption Specialists
To understand symmetric encryption in information security, we must look at a few basic terms:
Symmetric encryption and decryption follow a very specific path. This process ensures that data remains confidential while it travels across a network.
First, the sender takes the plaintext message. They choose a specific symmetric encryption algorithm. Then, they apply the secret key to that algorithm. The result is ciphertext. This scrambled data is now ready to be sent over the internet or stored on a disk.
Next, the receiver gets the ciphertext. To read the message, they must use the exact same secret key. The receiver applies this key to the inverse of the algorithm. This turns the ciphertext back into the original plaintext.
What happens if the key is lost? If the key is lost, the data usually cannot be recovered. This is why key management is so important.
Also Read: What is Decryption and Encryption in Modern Data Security?
Symmetric encryption algorithm types are usually divided into two main categories. These are stream ciphers and block ciphers.
1. Block Ciphers
A block cipher breaks the data into fixed-size chunks. These chunks are called blocks. A common block size is 128 bits. The algorithm processes each block one by one.
2. Stream Ciphers
A stream cipher encrypts data one bit or one byte at a time. It does not wait for a full block of data to be ready. This makes it very fast.
When discussing information security, we often compare symmetric methods to asymmetric ones. Asymmetric encryption uses two different keys: a public key and a private key.
Let us look at a comparison to see the differences clearly.
| Basis for Comparison | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Number of Keys | Single secret key | Two keys (Public and Private) |
| Speed | Very fast | Slower due to complex math |
| Resource Usage | Low CPU and memory needs | High CPU and memory needs |
| Key Exchange | Key must be shared securely | No need to share private keys |
| Primary Use | Bulk data encryption | Secure key exchange and signatures |
| Data Size | Good for large files | Good for small data bits |
It is easy to get confused by different security terms. Many people ask, "what is not a symmetric encryption algorithm?" Understanding the exceptions helps clarify the definition.
Algorithms like RSA (Rivest-Shamir-Adleman) and Diffie-Hellman are not symmetric. They rely on the relationship between two different keys. If an algorithm requires a "public key" to work, it is not symmetric.
Hashing is also not encryption. While encryption is a two-way street (you can lock and unlock it), hashing is a one-way street. MD5 and SHA-256 are examples of hashing. You cannot "decrypt" a hash to get the original data back. Therefore, a hash is not a symmetric encryption algorithm.
Also Read: What is BIOS Security? Features & Protection
Symmetric encryption in information security provides three main things: confidentiality, integrity, and speed.
Ensuring Confidentiality
The primary goal is to keep secrets. By using a strong symmetric encryption decryption process, organizations ensure that hackers cannot read stolen data. Even if a database is leaked, the information remains useless without the key.
Maintaining High Performance
Why don't we use asymmetric encryption for everything? The answer is speed. Asymmetric math is very heavy. It would slow down your internet connection if every single packet used it. Symmetric encryption and decryption are much lighter. This allows for real-time video streaming and fast file transfers.
Secure Storage
Most modern hard drives use symmetric methods to protect "data at rest." When you set a password on your laptop, the system often uses AES to lock your files. This is a classic example of symmetric encryption decryption in daily life.
No system is perfect. Symmetric encryption faces one major hurdle: the "Key Distribution Problem."
The Key Distribution Problem
If you and I want to talk privately, I need to give you my secret key. But how do I send it to you? If I send it through an email, a hacker could steal it. If they have the key, the encryption is useless.
Scalability Issues
In a large network, the number of keys grows very fast. If 100 people want to talk to each other privately, they need thousands of individual keys. Managing these keys becomes a nightmare for IT departments.
To keep data safe, we must use verified standards. Using "custom" or "home-made" encryption is a bad idea.
1. Advanced Encryption Standard (AES)
AES is the gold standard for symmetric encryption algorithm use. It was chosen by the National Institute of Standards and Technology (NIST) after a long competition. It supports key lengths of 128, 192, and 256 bits.
2. Blowfish and Twofish
These are alternative block ciphers. They were designed to be fast and are not owned by any single company. They are often used in password managers and open-source software.
Also Read: Cloud Encryption Gateway (CEG): Keep Keys, Secure Data
How do developers use symmetric encryption in information security? They follow a standard workflow.
Symmetric encryption is the backbone of modern digital privacy. It allows us to send huge amounts of data safely across the globe. By using a single secret key, it balances high-level security with incredible speed. While key management remains a challenge, combining this method with other tools creates a solid defense.
At FSD-tech we believe that understanding your security is the first step toward staying safe. We focus on providing clear, expert guidance to help you navigate the digital world. Your data is your most valuable asset, and we are committed to helping you protect it. Whether you are building an app or securing a business, we are here to support your journey with proven expertise and a client-first approach.
Don't leave your data to chance. Let’s build a robust encryption strategy together. Contact Our Team Today

What is the main advantage of symmetric encryption?
The main advantage is speed. It can process large amounts of data very quickly with very little power. This makes it perfect for mobile devices and high-speed servers.
Is symmetric encryption less secure than asymmetric?
No, it is not "less secure." In fact, a 256-bit symmetric key is mathematically stronger than a 2048-bit asymmetric key. The main risk is how the key is shared, not the strength of the math itself.
Can symmetric encryption be cracked?
Modern algorithms like AES-256 are currently impossible to "brute-force" with today's computers. It would take billions of years to try every possible key. Most hacks happen because someone stole the key, not because they broke the algorithm.
What is a common example of symmetric encryption?
Your home Wi-Fi (WPA2 or WPA3) uses symmetric encryption. Both your router and your phone use the same "Wi-Fi Password" as a key to protect your data.
How are keys shared safely?
In modern systems, we often use asymmetric encryption to send a symmetric key. This combines the security of asymmetric methods with the speed of symmetric ones.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts