
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered why a regular employee can access the entire company server? In many cases, users have more power than they actually need to do their jobs. This creates a massive security gap. When you give everyone keys to every door, one lost key can lead to a total disaster. How do we stop this? The answer lies in a core security concept.
The concept of least privilege serves as a foundation for modern digital safety. It ensures that users only get the specific access they need. But what exactly does this look like in a real-world setting? Let us explore how this strategy protects your data and your business.
In simple terms, it is a security rule that limits access rights for users, accounts, and computing processes. You only provide the minimum permissions necessary to perform a task. If a person only needs to read a file, they should not have the right to edit or delete it.
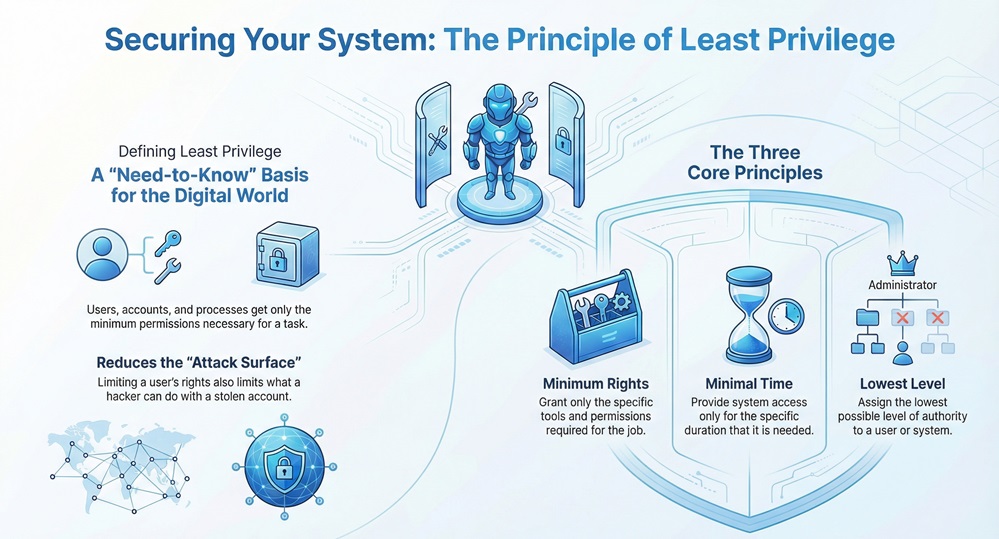
It is the practice of restricting access to the bare minimum. This applies to humans, but it also applies to applications, systems, and devices. Think of it as a "need-to-know" basis for the digital world.
Request a Comprehensive Access Audit
Least privilege principles focus on reducing the attack surface. When you limit what a user can do, you limit what a hacker can do if they steal that user's login.
It means your system must verify every request. It does not trust a user just because they are inside the network. Access control systems use this rule to decide who can see, change, or move data.
Least privilege access control works by creating strict boundaries. For example, a marketing manager does not need access to the payroll database. By blocking that path, the system stays secure.
Also Read: What Is Zero Touch Provisioning (ZTP)? All You Need to Know
To understand why least privilege security matters, we must compare it to the alternative. Many older systems use "all-or-nothing" access. This is dangerous.
| Basis for Comparison | Least Privilege Access | Excessive Privilege Access |
|---|---|---|
| Access Level | Minimum required for tasks | Full access to many systems |
| Security Risk | Low (contained) | High (widespread) |
| User Scope | Specific and restricted | Broad and open |
| Management | Requires regular audits | Often ignored or "set and forget" |
| Impact of Breach | Limited to one area | Potential for total system takeover |
Least privilege access is not just a suggestion; it is a necessity. Data breaches are expensive and common. Most attacks involve someone using a stolen account to move through a network.
Stopping Lateral Movement
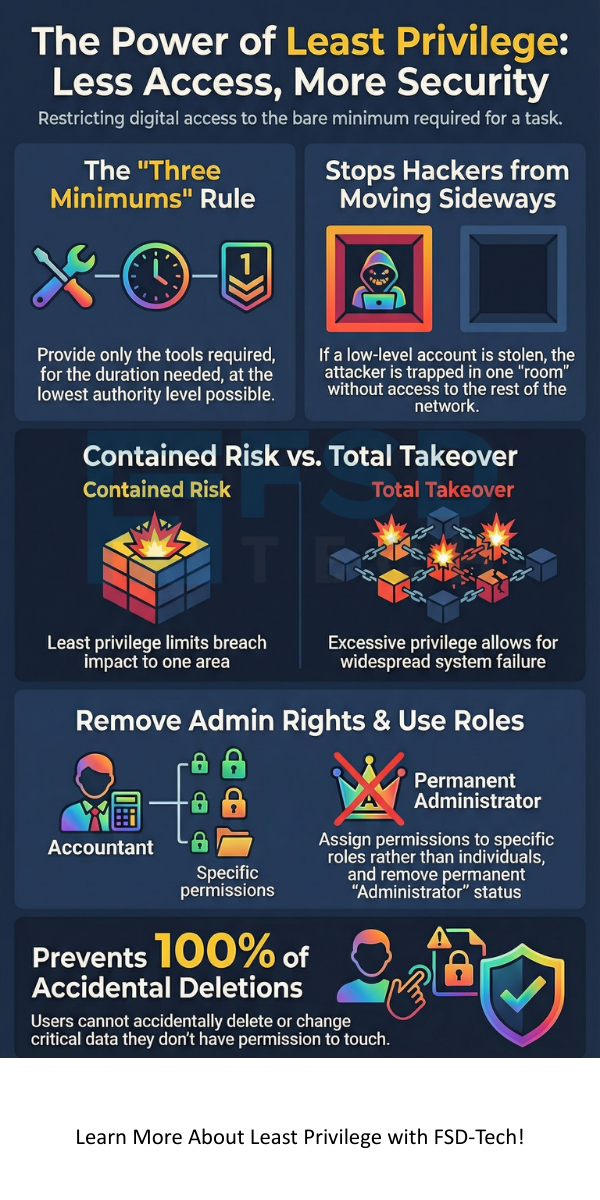
Least privilege security prevents hackers from moving sideways through your system. If a hacker enters through a low-level account, they find themselves stuck in a small "room" with no exit. They cannot reach your sensitive files because the account they stole does not have those rights.
Reducing Human Error
Least privilege access control protects you from mistakes. Even the best employees make errors. Someone might accidentally delete a database or change a setting. If they do not have the permission to do those things, the mistake never happens.
Meeting Compliance Standards
Many regulations like HIPAA or GDPR require you to protect data. They often mandate that you limit access. Using least privilege principles helps you pass audits and avoid heavy fines.
Also Read: What is Credential Stuffing? Detection and Prevention
It involves a few technical steps. It is not a one-time setup. It is a continuous process of checking and adjusting.
Step 1: Identify Critical Assets
The concept of least privilege starts with knowing what you own. You must list your databases, servers, and sensitive files. You cannot protect what you do not see.
Step 2: Categorize Users and Roles
Least privilege access relies on "Role-Based Access Control" (RBAC). Instead of giving permissions to a person, you give them to a role. For example, a "Developer" role gets access to the code, while an "Accountant" role gets access to invoices.
Step 3: Remove Admin Rights
Most users do not need to be administrators on their laptops. Removing these rights prevents them from installing unauthorized software or malware.
Step 4: Use Just-in-Time (JIT) Access
Least privilege security can be temporary. JIT access gives a user high-level rights only when they need them. Once the task is done, the system automatically removes those rights. This leaves no "always-on" doors for hackers to find.
Least privilege access control sounds easy, but it takes work. You might face some pushback from your team.
Also Read: Brute Force Attack in Cybersecurity - How it Works?
The concept of least privilege offers more than just security. It improves the way your whole IT department functions.
By adopting least privilege principles, you create a resilient environment that respects your data. Security is not just about building higher walls. It is about making sure that if someone gets over the wall, they find nothing of value.
At our core, we believe that your safety is our priority. We focus on providing solutions that protect your assets while keeping your team productive. Your trust is our most valuable asset, and we work every day to earn it through smart, simple, and effective security strategies.
"Don't give hackers an open door. Let us help you build a Zero Trust environment today. Contact Our Security Team
What is the principle of least privilege in simple terms?
It is the practice of giving people exactly what they need to do their job and nothing more. It is like giving a hotel guest a key that only opens their room, not the manager's office.
Why is least privilege important for remote work?
Remote workers often use unsecured Wi-Fi. If their device is compromised, least privilege access ensures the hacker cannot reach the corporate core.
Does least privilege apply to software?
Yes. Least privilege principles dictate that an application should only run with the permissions it needs. A calculator app should not have access to your contacts or location.
How do I start using least privilege?
Start by auditing your current users. See who has "Administrator" status and ask if they really need it. Most of the time, they do not.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts