
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Unplanned outages and network failures can disrupt operations, damage productivity, and hurt business continuity. To be honest, most of us have felt that sinking feeling when the "internet is down" at a major branch. Cato SASE addresses these challenges by offering built-in High Availability (HA) and redundancy features across your sites, edges, and links. You don't need complex setups or third-party failover solutions.
The beauty of Cato lies in its simplicity. This blog explores how Cato supports seamless uptime through active-active tunnels, automatic failover, site-level HA, and cloud backbone resilience. Are you ready to stop worrying about the next fiber cut?
Cato’s architecture is designed with redundancy at multiple levels:
To prevent internet outages at branch or HQ sites:
When a link degrades, traffic is shifted seamlessly to the healthier path without user disruption.
Also Read: Simplifying IT Operations with Cato SASE: Reducing Complexity and Enhancing Performance
Cato uses continuous tunnel health monitoring to assess each link’s quality. Probes are sent every few seconds to measure:
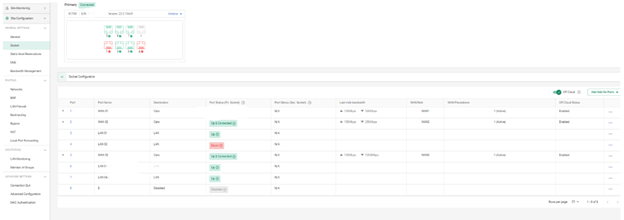
These metrics are visible in:
Cato automatically routes critical traffic over the healthier path based on this telemetry, ensuring the best user experience at any moment.
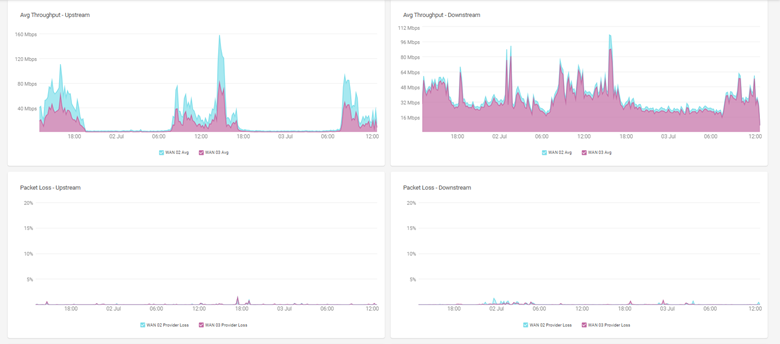
Cato also offers End-to-End Experience Monitoring, particularly useful for identifying issues in the local ISP (last mile). Using synthetic probes and performance baselines, you can:
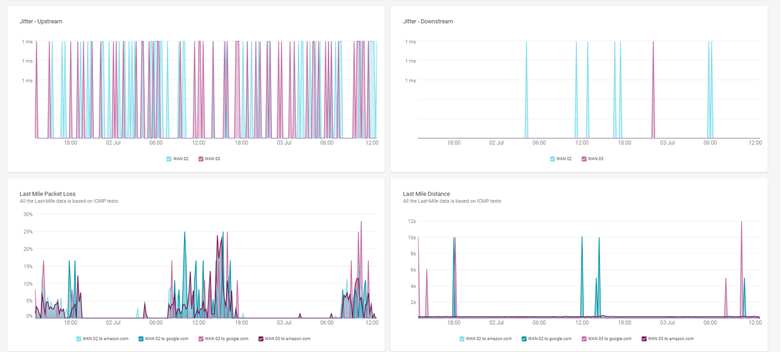
This allows IT teams to validate SLA compliance and hold ISPs accountable during performance degradation.
For critical sites, Cato supports High Availability using two Sockets in Active/Standby mode:
Steps:
Also Read: Preventing Insider Threats and Unauthorized Access with Cato SASE’s Context-Aware Security
A regional headquarters in the GCC has two internet links and redundant Sockets:
During a power event, Socket A went offline. Socket B seamlessly took over, and Smart Link Selection routed voice traffic over the LTE backup while prioritizing ERP access.
Business operations continued without any downtime or end-user impact.
You can monitor the health and performance of HA setups using:
Yes. You can still achieve link-level redundancy with a single Socket and multiple WAN links.
Yes, for any site with supported hardware and licensing.
Typically occurs within seconds and does not require manual intervention.
Yes. You can set link priorities and policies via Smart Link Selection.
No. HA is designed for site-level deployments, not individual client devices.
High Availability and redundancy aren’t just checkboxes—they’re critical for keeping your business online and your users productive. With Cato, you get these capabilities natively, and setting them up is easier than ever.
High Availability and redundancy aren’t just checkboxes—they’re critical for keeping your business online. With Cato, you get these capabilities natively, making setup easier than ever. We believe in empowering IT teams with tools that just work, so you can focus on growth rather than troubleshooting.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts