
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

When you work from a coffee shop or a home office, you likely need a secure way to reach your office files. You might wonder how your computer stays safe while talking to a private server miles away. This is where a specialized piece of networking hardware or software comes into play. It acts as a sentry, guarding the entrance to a private network. But how exactly does this "sentry" handle your data?
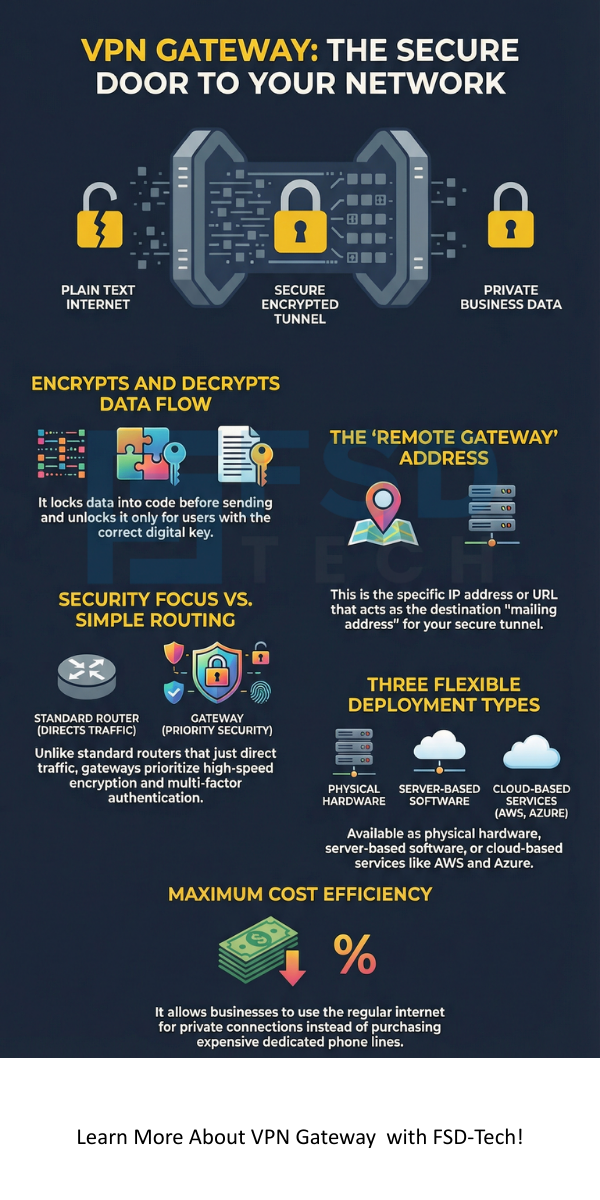
The VPN gateway is a networking device that connects two or more networks or devices in a VPN structure. To understand it simply, think of it as a physical or virtual door. This door only opens for data that has the right key. It sits at the edge of a local network. When you send data, the VPN gateway encrypts it. When data arrives, the gateway decrypts it. This ensures that even if someone intercepts your data on the internet, they cannot read it.
A VPN gateway provides a secure path through an unsecure network like the internet. Most businesses use it to link branch offices or to allow remote employees to log in safely. It uses protocols like IPsec or SSL to create a "tunnel." This tunnel wraps your data packets in a protective layer. Without this gateway, your private company data would travel across the web in plain text. Would you want your bank details or trade secrets floating around for anyone to see?
Before we dive deeper, it helps to see how a VPN gateway differs from a standard home router. While they look similar, their jobs are quite different.
| Feature | Standard Router | VPN Gateway |
|---|---|---|
| Primary Goal | Directs traffic between networks. | Secures traffic between networks. |
| Encryption | Usually none for transit data. | Encrypts all data in the VPN tunnel. |
| Authentication | Basic Wi-Fi password. | Strong certificates or multi-factor keys. |
| Hardware | Simple consumer-grade chips. | High-speed chips for encryption tasks. |
| Use Case | Home internet access. | Corporate remote access and site-to-site links. |
To define it more formally, a VPN gateway is a type of networking device that terminates VPN tunnels. It can be a dedicated router, a firewall, or even a software service in the cloud. It manages the connection between a local area network (LAN) and a remote device.
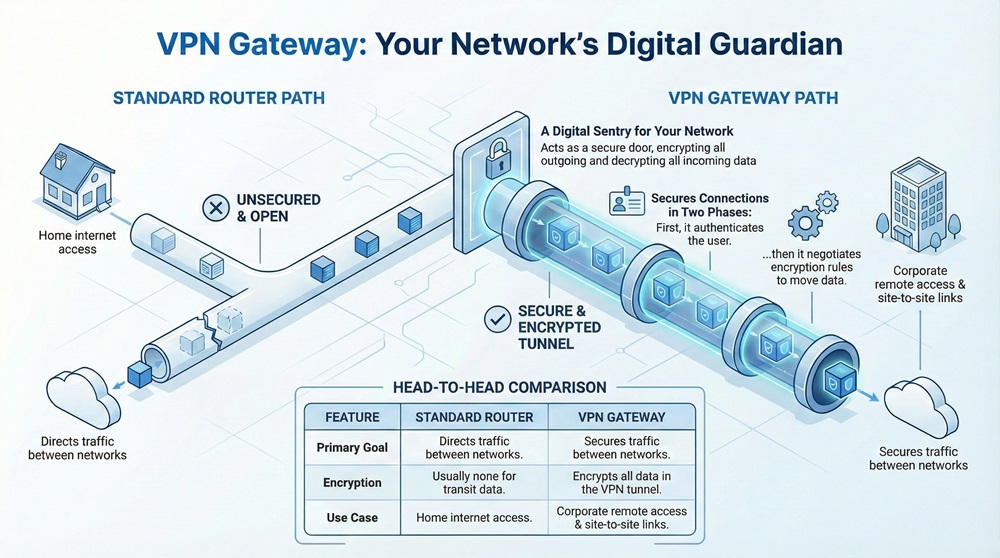
VPN gateway operations rely on two main phases. First, it establishes a secure handshake with the sender. It checks if the user is who they claim to be. Second, it negotiates the "ciphers" or rules for encryption. Once both sides agree, the gateway starts moving data. This device must handle a lot of math. Encrypting every single packet of data requires significant processing power.
Shop our latest enterprise-grade networking solutions.
You might see the term "remote gateway" when setting up your software. So, what is remote gateway in vpn settings? The remote gateway refers to the IP address or the URL of the device on the other end of your connection. If you are at home, your computer is the local client. The big server at your office is the remote gateway.
Remote gateway in vpn configurations tells your computer exactly where to send the encrypted "tunnel" packets. If you enter the wrong address here, your computer will not know where the secure door is located. Think of it as the mailing address for your private digital tunnel.
A VPN gateway works by using a set of rules called protocols. These protocols decide how the data is locked and unlocked. The most common protocol used by a VPN gateway is IPsec (Internet Protocol Security).
VPN gateway devices often include a firewall. This adds another layer of safety. It checks not just if the data is encrypted, but also if the data is "allowed" to enter based on company policy.
Also Read: What is Cloud Access Security Broker (CASB)?
Not every VPN gateway is a physical box. Depending on your needs, you might use different forms:
Many people look for free ways to stay secure. One common tool is the VPN Gate project. This leads to a common question: is vpn gate client safe?
VPN gate client safe concerns stem from the fact that it is an academic project. It relies on volunteers to provide the servers. While the software itself is usually clean, the "nodes" you connect to are owned by strangers. Unlike a corporate VPN gateway, you do not know who is on the other side.
If you use it for casual browsing, it might be fine. However, for sensitive work or banking, a volunteer-run system is risky. A volunteer could theoretically log your traffic before it leaves their server. For true safety, a private or managed VPN gateway is always the better choice.
A VPN gateway offers more than just privacy. It provides a foundation for modern business logic.
1. Secure Remote Access
A VPN gateway allows you to work from anywhere. It treats your home laptop as if it were plugged into the office wall. This keeps your internal apps off the public internet.
2. Site-to-Site Connectivity
A VPN gateway can link two entire offices. If you have a branch in New York and one in London, the gateway makes them feel like one big office. The staff in London can print to a printer in New York seamlessly.
3. Cost Efficiency
A VPN gateway saves money. In the old days, companies had to buy expensive private lines from phone companies. Now, you can use the regular internet to create a private network for a fraction of the cost.
4. Data Integrity
A VPN gateway ensures your data does not change during transit. It uses "hashes" to check if anyone tampered with the packets. If a single bit of data is changed by a hacker, the gateway will drop the packet..
Also Read: What is Geofencing Technology? All You Need to Know
Setting up a VPN gateway requires a few specific steps. You must be careful with the details to avoid security holes.
Step 1: Define Your Network Ranges
It needs to know which IP addresses are "inside" and which are "outside." You must ensure your home network and office network do not use the same IP numbers.
Step 2: Choose Your Protocol
Most experts suggest using IPsec for site-to-site links. For individual users, SSL/TLS is often easier. The VPN gateway must be configured to support the choice you make.
Step 3: Configure Authentication
How will the VPN gateway know it is you? You can use simple passwords, but certificates are much safer. A certificate is like a digital passport that is very hard to fake.
Step 4: Test the Tunnel
Once configured, you try to "ping" a device on the other side. If the VPN gateway logs show a "successful handshake," your tunnel is active.
While a VPN gateway is powerful, it is not perfect. You might run into some hurdles.
We live in a world where data is a primary target. A VPN gateway acts as your first line of defense. It allows your team to stay productive without risking the company's "crown jewels." By choosing the right gateway and configuring it with care, you build a wall that is hard for any intruder to climb.
Talk to an expert about securing your remote workforce.
A VPN gateway is an essential tool for any modern organization. It bridges the gap between convenience and security.
The primary goal is to provide a secure, encrypted entrance to a private network. It protects data as it moves across public spaces.
Yes. Many modern firewalls include VPN gateway features. This allows one device to handle both security filtering and encrypted tunneling.
No. A VPN service (like NordVPN or ExpressVPN) is for hiding your personal browsing. A VPN gateway is for connecting specific networks or remote workers to a private business environment.
Slowness usually comes from the processor. If the VPN gateway has a weak CPU, it cannot encrypt data fast enough for a high-speed fiber connection.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts