
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

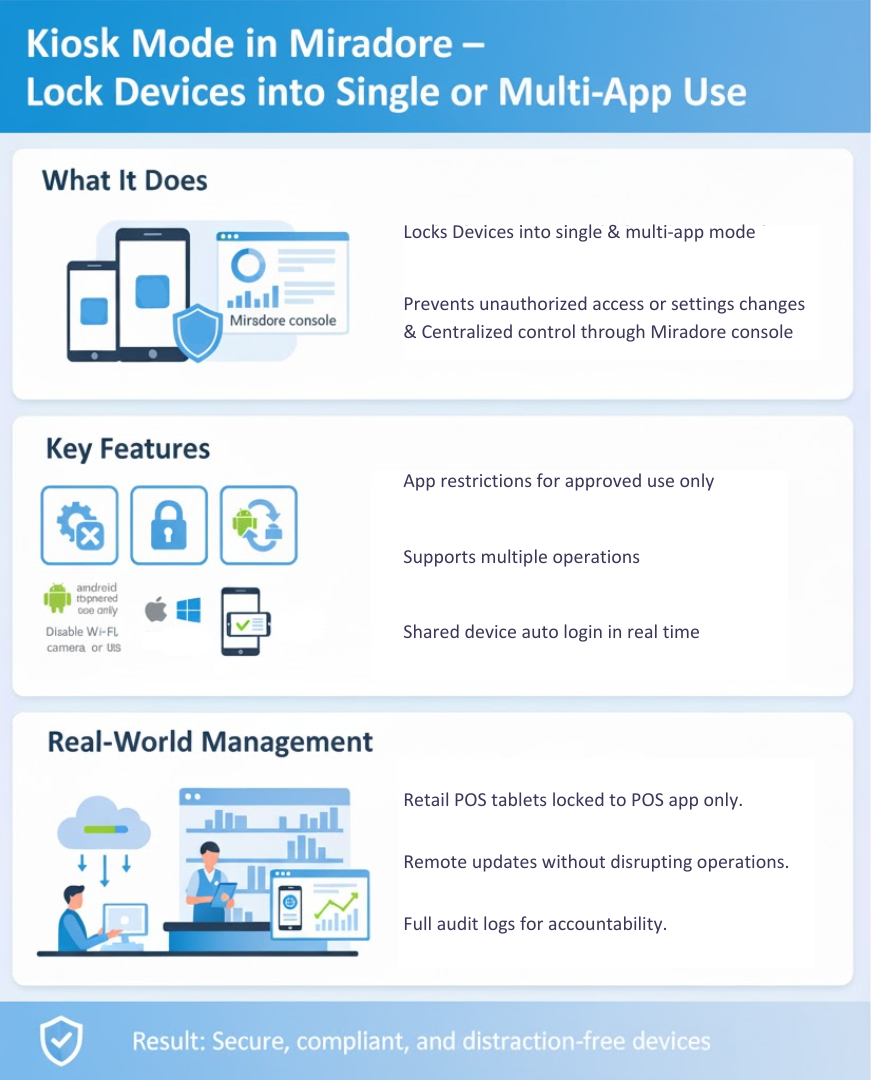
Some devices in enterprise environments are dedicated to a single function or a limited set of apps, such as point-of-sale systems, digital signage, or shared tablets in education. Managing these devices securely requires restricting access to only the intended apps and functions.
Miradore EMM offers Kiosk Mode, enabling IT teams to lock devices into single or multiple applications, enforce restrictions, and maintain compliance without constant manual supervision. This ensures the device is used as intended while protecting corporate data and resources.
Kiosk Mode is a configuration that restricts a device’s functionality to a predefined set of apps and features. In Miradore, this is not just about locking a screen—it’s about enforcing workflow-specific restrictions while retaining full remote management capabilities.
Kiosk Mode can be applied for:
A regional retail chain deployed tablets at checkout counters for billing and inventory scanning. By using Miradore Kiosk Mode:
The result was secure, focused, and efficient device usage without disrupting operations.
Kiosk Mode simplifies deployment and security of single or multi-purpose devices, making it ideal for retail, healthcare, education, and field operations. Miradore’s centralized console makes setup and ongoing management fast, secure, and reliable.
Enable Kiosk Mode today with Miradore EMM and secure your enterprise devices effortlessly.
If You Need Further Details On Setting Up Kiosk Mode, Configuring Multi-App Restrictions, Or Managing Shared Devices With Miradore EMM, Please Feel Free To Schedule A No-Obligation Requirement-Gathering Virtual Meeting With Our Miradore Implementation Experts. Schedule Now
Miradore Kiosk Mode is supported on Android Enterprise devices, iOS/iPadOS supervised devices, and Windows/macOS endpoints.
Yes. Miradore allows multi-app Kiosk Mode, giving access only to the selected business apps while restricting all others.
Miradore enforces restrictions at the OS level where supported, preventing unauthorized app installations or access to system settings.
Absolutely. Miradore supports auto-login and profile rotation, making shared devices secure and easy to manage.
Yes. IT administrators can update Kiosk apps, schedules, and restrictions remotely via the Miradore console.
No. Miradore Kiosk Mode works alongside existing security policies, including encryption, VPN enforcement, and compliance rules.
Yes. Miradore allows scheduling app updates or modifying Kiosk configurations remotely, ensuring devices remain compliant and up to date.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!

🕓 January 1, 2026

🕓 December 15, 2025

🕓 December 12, 2025
share your thoughts