
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

You use the internet every day for banking, shopping, and sharing information. You expect these actions to be safe. But how does your computer or smartphone know that the website you visit or the person you are communicating with is genuine?
This is where a digital certificate plays a vital role. This little file acts as your digital passport, proving your identity or the identity of a website, device, or individual online. It is a fundamental component of network security and online trust. Digital certificates ensure that your private information remains private and secure from cyber criminals.
In this comprehensive guide, we will explore what a digital certificate is, why it is essential, what it contains, and the various ways you use it every day without even realizing it.
A digital certificate can be understood as an electronic file that uses Public Key Infrastructure (PKI) to verify the identity of an entity. Think of it like a photo ID card or a driver’s license in the real world. This certificate is issued by a trusted third-party organization called a Certificate Authority (CA).
The primary function of a digital certificate is to bind a public key to an owner's identity. This binding ensures that the public key you receive truly belongs to the entity claiming that identity. Digital certificates are critical for enabling secure communication and transactions over the internet.
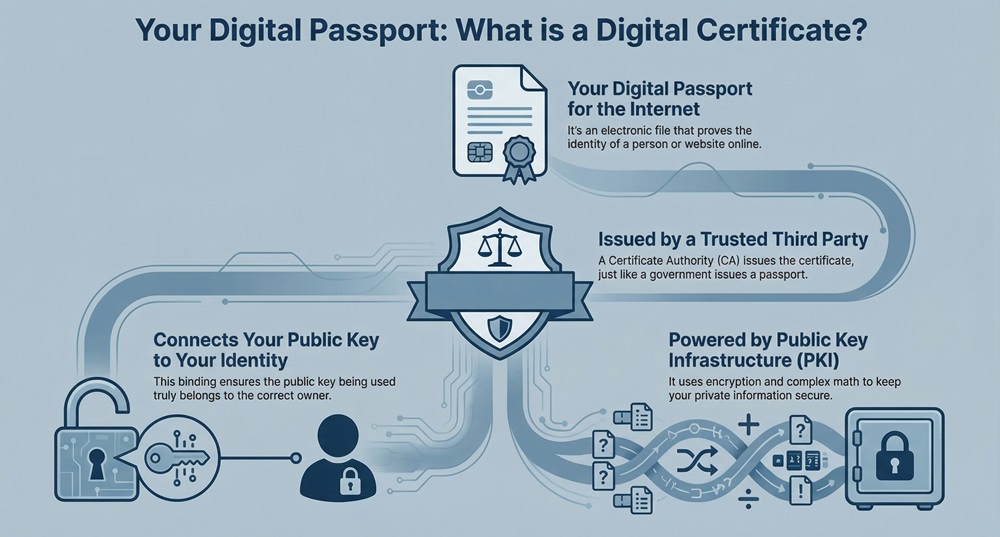
Now, the question arises: what makes this certificate secure? It all comes down to the cryptographic science of PKI. Digital certificates use encryption and mathematical algorithms to protect the data they contain.
PKI is nothing but a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. It is the entire security system that makes certificates work.
To understand this better, you must first know about public-key cryptography. This system uses a pair of mathematical keys:
The digital certificate ensures that the public key is authentic. It prevents someone else from pretending to be your bank by giving you a fake public key.
Also Read: Man-in-the-Middle (MITM) Attack - Prevention Guide
A digital certificate is a structured file, typically following the X.509 standard. It contains specific, essential pieces of information that ensure authenticity and functionality.
| Element | Description | Purpose |
|---|---|---|
| Subject's Public Key | The cryptographic key used to encrypt data sent to the certificate holder. | Enables secure communication and data encryption. |
| Subject's Identity | The name of the person, device, or organization the certificate belongs to. | Proves who the certificate is for. |
| Issuer's Identity | The name of the Certificate Authority (CA) that issued the certificate. | Proves the certificate's authenticity and trustworthiness. |
| Validity Period | The "Issued On" and "Expires On" dates. | Defines the time frame during which the certificate is considered valid. |
| Serial Number | A unique number assigned by the CA. | Distinguishes this specific certificate from all others. |
| Signature Algorithm | The algorithm used to sign the certificate. | Indicates the method used to secure the certificate data. |
| CA Digital Signature | A signature created with the CA's private key. | Ensures the certificate has not been tampered with and verifies the issuer. |
This detailed content within the certificate allows a computer to run a quick digital certificate checker process. Your browser checks the validity period and the CA's digital signature to ensure everything is correct before creating a secure connection.
The entity that issues a digital certificate is called a Certificate Authority (CA).
A Certificate Authority refers to the trusted organization that validates the identities of entities and issues the certificates. A few well-known CAs include DigiCert, Sectigo, and GlobalSign. These companies are audited and regulated worldwide.
You can compare a CA to a government agency that issues your passport. You trust the passport because you trust the issuing government agency. Similarly, your browser and operating system trust a CA because their root certificates are pre-installed in your software.
The process of getting a digital certificate involves the CA verifying the applicant's identity.
Once the CA validates the identity, it creates the certificate, signs it with its own private key, and sends it to the applicant.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
Digital certificates have various applications, which makes them essential for modern security. They play a vital role in four main areas: securing websites, protecting email, authenticating users, and facilitating legal documents.
1. Securing Websites (SSL/TLS)
The most common use is securing the connection between your browser and a website. When you see a padlock icon in your browser's address bar and the URL starts with https://, you are using a secure connection.
This security relies entirely on an SSL/TLS digital certificate. Digital certificates ensure the following:
2. Digital Signatures and Legal Documents
A crucial application is the creation of a digital signature. A digital signature provides the same legal standing as a physical signature on paper. It ensures the following two key things:
You need a Digital Signature Certificate (DSC) to create this signature. Where digital signature is used often includes:
3. Secure Email Communication (S/MIME)
Just like websites, you can use digital certificates to secure your email. Using the S/MIME protocol, you can:
4. Device and User Authentication
In large organizations and corporate networks, digital certificates are used to authenticate users and devices. Digital certificates act as credentials, eliminating the need for simple passwords.
Also Read: Spear Phishing: Learn About #1 CEO fraud
Understanding where digital certificates are stored is important for managing your security.
A digital certificate has two parts that must be stored securely: the public certificate (the file itself) and the private key.
People often use these terms interchangeably, but they represent different things. Let us now discuss the specific difference between a digital certificate and a digital signature.
| Basis for Comparison | Digital Certificate | Digital Signature |
|---|---|---|
| Nature | An electronic file used for identity verification. | A mathematical scheme used to prove the authenticity and integrity of a message or document. |
| Primary Goal | To verify the identity of the holder and secure a communication channel. | To guarantee the origin, integrity, and non-repudiation of a data item (a document or email). |
| Component Used | Contains the Public Key and identity information, signed by a CA. | Created using a person’s Private Key and a hash of the data. |
| Function | Enables secure encryption and authentication. | Proves that a specific person signed a specific document at a specific time. |
| Example | The SSL/TLS file that makes an "https" website secure. | The authenticated mark placed on an e-tender document. |
In simple terms, you need a digital certificate to create a digital signature. The certificate is the identity; the signature is the act of proving authenticity.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
It is a fundamental defense mechanism against some of the most common online threats. It plays a significant role in creating a trustworthy internet environment.
Digital certificates help prevent three major cyber threats:
Therefore, you can see that certificates are not just an extra feature; they are the bedrock for encrypted and trusted digital transactions worldwide.
A digital certificate is not just technical jargon; it is the invisible guardian of your online world. It is the core of trust that enables you to safely conduct transactions, send sensitive emails, and know that the website you are visiting is authentic. Digital certificates ensure that secure, authenticated communication is possible for everyone.
We believe in providing the tools and knowledge you need to navigate the digital world securely. By understanding what is a digital certificate and its powerful role, you can take control of your online safety.
If your business handles sensitive customer data or requires authenticated signatures on documents, you must implement the appropriate digital certificate solution.
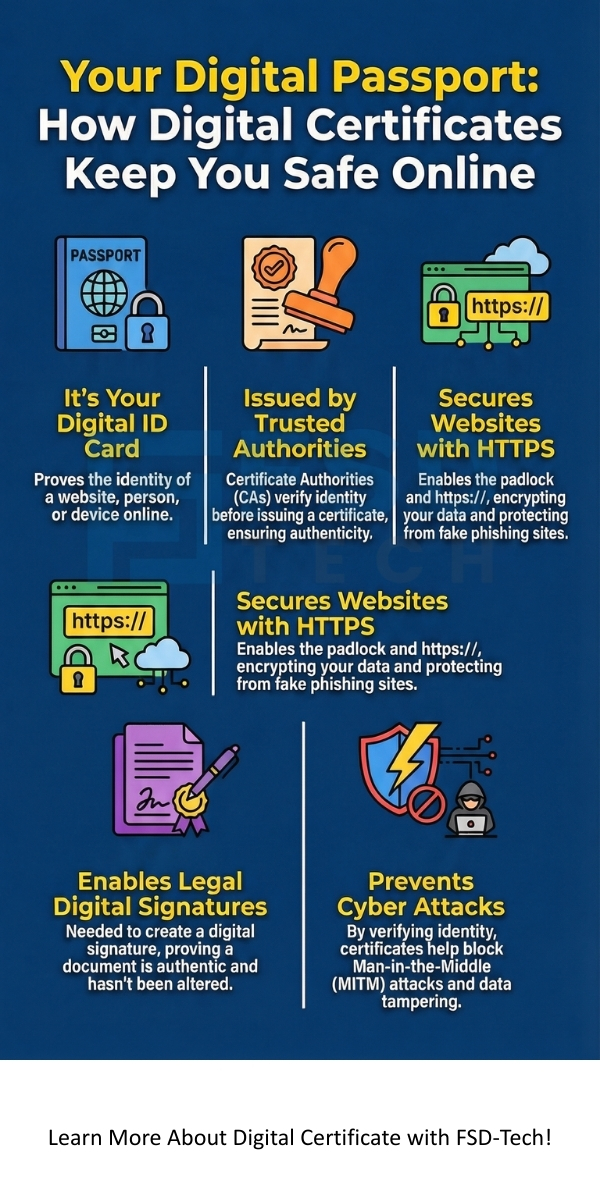
Here are five key takeaways summarizing the importance and function of digital certificates:
Your Digilocker documents are digital copies of your official papers (like your driver's license or academic mark sheets). Are Digilocker documents valid? Yes, they are legally valid and recognized as original documents under the IT Act, 2000.
The validity is largely guaranteed because they are issued by the original source (like the transport department or a university) and are secured within the Digilocker ecosystem.
While Digilocker uses various security measures, including digital certificates for platform security, the term digital certificate is mainly used for the Digital Signature Certificate used for signing documents or the SSL/TLS certificate securing the website connection.
When you visit a secure website, your browser performs an instant check using a four-step process:
You can manually inspect the certificate by clicking on the padlock icon in your browser's address bar.
To get digital signature certificate involves approaching a Registering Authority (RA) or a partner of a licensed Certificate Authority (CA) in your country.
In India, for example, CAs like e-Mudhra or Sify are licensed to issue these certificates. You must submit an application form, proof of identity, and proof of address. The CA or its RA will verify your documents before issuing the DSC, usually on a secure USB token.
The standard maximum lifespan for an SSL/TLS digital certificate (the kind used for websites) is currently 398 days (about 13 months). CAs must revoke older, longer-lived certificates.
Shorter validity periods ensure that keys are frequently rotated, which helps maintain higher security standards. For a Digital Signature Certificate for individuals, they are often issued for a one-year or two-year validity period.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts