.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Across Dubai, Abu Dhabi, and the wider GCC, cloud-native transformation is reshaping how enterprises build, deploy, and secure digital services. Fintech innovators, SaaS providers, logistics leaders, and smart infrastructure operators are leveraging microservices, containers, and serverless architectures to accelerate time-to-market and adapt to dynamic business demands.
This shift, however, brings a new set of challenges: ephemeral workloads, distributed APIs, and hybrid cloud deployments render traditional perimeter-based security and legacy WAN architectures obsolete. CTOs, DevSecOps leads, and platform engineers must now deliver seamless performance and airtight security—while ensuring compliance with UAE and GCC regulations.
To address these challenges, cloud-first enterprises in the UAE need a converged, cloud-native approach to networking and security.
Secure Access Service Edge (SASE) is a transformative architecture that merges networking (SD-WAN) and comprehensive security (Zero Trust, FWaaS, SWG, CASB, IPS) into a single, cloud-delivered platform. Unlike fragmented legacy stacks, SASE is designed for the distributed, dynamic nature of modern applications and users.
Cato Networks pioneered this model, delivering a platform that connects users, locations, clouds, and applications with consistent security and optimized performance—globally and locally.
Cato’s Points-of-Presence in Dubai and Fujairah bring SASE’s benefits directly to UAE and GCC enterprises:
Cato SASE is purpose-built for cloud-native environments:
Want to explore how Cato SASE can optimize your UAE workloads? Share your details and we’ll send you tailored insights. Click Here
Traditional security stacks chain multiple inspection engines, each adding latency and complexity. Cato’s Single Pass Cloud Engine (SPACE) processes traffic in a single, unified step:
Kubernetes and service mesh frameworks (e.g., Istio, Linkerd) are foundational to cloud-native architectures. However, their reliance on mTLS for secure service-to-service communication can introduce significant latency and consume CPU resources.
Cato SASE addresses this by offloading deep packet inspection, threat detection, and policy enforcement to its optimized PoPs. This reduces the burden on local nodes, allowing microservices to communicate securely at wire speed—without sacrificing security or compliance.
A Dubai-based fintech startup migrates its payment microservices to Kubernetes. By routing traffic through Cato’s Dubai PoP, the company achieves:
Cloud-native environments are in constant flux—new services are deployed, APIs are updated, and user access patterns shift daily. Manual policy management cannot keep pace.
Cato Autonomous Policies leverage AI to continuously analyze traffic patterns, threat intelligence, and workload changes. The system automatically tunes firewall and access rules in real time, ensuring:
Zero Trust security is essential for cloud-native stacks. Cato SASE enables identity-based microsegmentation—policies are enforced based on user, device, and application identity, not just IP addresses. This approach:
A logistics provider in Abu Dhabi integrates Cato SASE into its CI/CD pipeline. As new microservices are deployed, Autonomous Policies automatically adjust access controls, ensuring only authorized services can communicate. This reduces the risk of supply chain attacks and accelerates secure software delivery.
Curious how Autonomous Policies would fit your own environment? Share your details and we’ll map a use case for you. Click Here
Deploying SASE in a cloud-native environment requires deep understanding of application topologies, traffic flows, and regulatory requirements. FSD Tech, as a GCC-based systems integrator, provides:
UAE and GCC regulations mandate strict controls on data processing and storage. FSD Tech ensures that Cato SASE deployments:
From smart city platforms to SaaS providers, FSD Tech adapts Cato SASE to unique industry needs—whether securing IoT edge devices, enabling multi-tenant isolation, or supporting high-throughput analytics.
Service mesh frameworks are powerful but can become a performance bottleneck due to mTLS and policy enforcement overhead. By offloading inspection and security processing to Cato’s PoPs, enterprises can:
Cato SASE provides a single-pane-of-glass dashboard for monitoring all traffic—across clouds, data centers, and edge locations. Unified policy enforcement ensures that security controls are consistent, auditable, and easy to manage, even as workloads scale and evolve.
Cato SASE’s cloud-native, globally distributed architecture ensures that UAE enterprises can:
As the UAE accelerates smart infrastructure, IoT, and edge computing initiatives, Cato SASE provides the flexible, secure foundation needed to support:
Ready to secure and optimize your cloud-native apps with Cato SASE? Schedule a quick session with our experts today. Schedule now
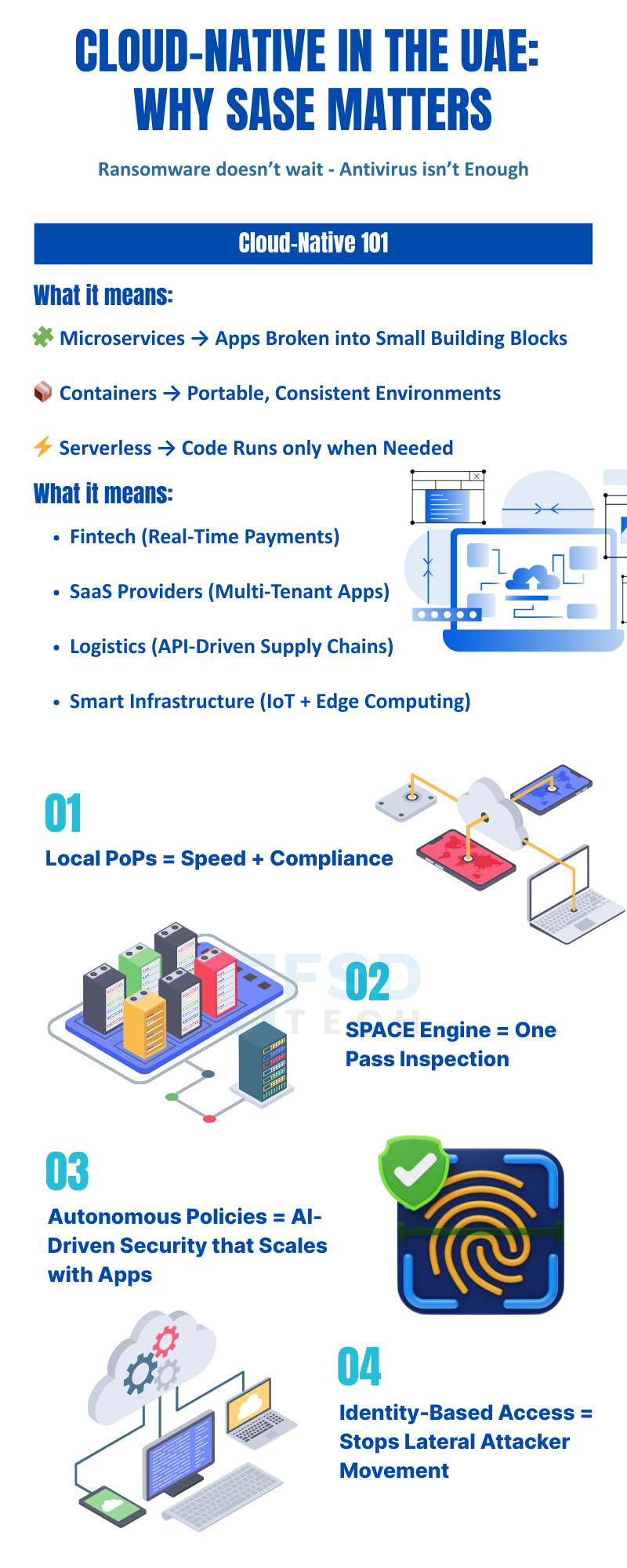
Cato SASE leverages local Points-of-Presence (PoPs) in Dubai and Fujairah to minimize latency and optimize traffic routing. This ensures high performance for microservices, containers, and serverless workloads by providing direct, low-latency connections to Cato’s global backbone. UAE-based enterprises benefit from sub-10ms latency for critical application flows, supporting both user experience and backend service responsiveness.
Cato SASE converges SD-WAN, Zero Trust Network Access (ZTNA), Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Intrusion Prevention System (IPS) into a single platform. This unified approach delivers identity-based security policies, deep traffic inspection, and consistent enforcement across all cloud-native workloads, whether on-premises or in the cloud.
Cato SASE offloads deep packet inspection and security processing to optimized PoPs, reducing the local resource and latency impact of service mesh frameworks like Istio or Linkerd. This approach allows Kubernetes and containerized environments to maintain secure mTLS communication without sacrificing performance or consuming excessive compute resources.
FSD Tech brings deep regional expertise in cloud-native transformation and regulatory compliance. As a GCC-based systems integrator, FSD Tech helps enterprises map service topologies, integrate Cato SASE into CI/CD pipelines, and tailor security policies to meet UAE and GCC data residency requirements. Their local presence ensures deployments are optimized for both performance and compliance.
Yes, Cato SASE supports automation and policy-as-code, enabling seamless integration into CI/CD workflows. This allows security controls and network policies to be automatically applied as new microservices or containers are deployed, supporting rapid, secure application delivery and minimizing manual intervention.
Cato SASE processes sensitive data within UAE-based PoPs, supporting data residency and sovereignty requirements. FSD Tech ensures that deployments maintain audit trails, reporting, and rapid response capabilities for regulatory changes or audits, helping enterprises meet the strict compliance standards of the UAE and GCC.
The SPACE engine inspects, secures, and re-encrypts traffic in a single operation, eliminating the latency and complexity associated with chained security appliances. For containerized and microservices-based architectures, this means wire-speed performance and consistent policy enforcement for both east-west and north-south traffic.
Cato Autonomous Policies use AI to continuously analyze traffic patterns and threat intelligence, automatically tuning firewall and access rules in real time. This ensures optimal security and throughput for dynamic cloud-native workloads, reducing the risk of human error and supporting rapid scaling.
Yes, Cato SASE offers unified visibility through a single management console, allowing enterprises to monitor traffic, enforce policies, and respond to incidents across on-premises, cloud, and edge deployments. This end-to-end observability is critical for maintaining security and compliance in distributed cloud-native environments.
By converging networking and security into a single, cloud-native platform, Cato SASE eliminates the need for multiple point solutions, manual policy updates, and complex integrations. This streamlines operations, reduces costs, and enables IT teams to focus on innovation rather than maintenance.
Fintech, SaaS, logistics, and smart infrastructure sectors in the UAE and GCC are prime beneficiaries. These industries require high-performance, secure, and compliant cloud-native environments to support rapid digital transformation, regulatory requirements, and global expansion.
Cato SASE enforces policies based on user, device, and application identity, rather than just IP addresses. This granular approach prevents lateral movement by attackers, supports Zero Trust architectures, and enables secure access for ephemeral containers and serverless functions.
FSD Tech begins by mapping service topologies and traffic flows, then integrates Cato SASE into existing CI/CD pipelines and cloud environments. They tailor security policies to the organization’s needs, ensure compliance with UAE regulations, and provide ongoing support and optimization.
Cato SASE’s globally distributed, cloud-native architecture allows enterprises to scale rapidly, support new locations or services, and adapt to evolving cloud and edge use cases. Its flexible policy engine and AI-driven automation ensure that security and performance keep pace with business growth.
Local PoPs in Dubai and Fujairah ensure that sensitive data is processed within the UAE, supporting data residency and sovereignty requirements. They also provide ultra-low latency connections for users and applications, improving both compliance and user experience.
FSD Tech works closely with enterprises to understand specific regulatory, operational, and technical needs. Whether securing IoT edge devices for smart infrastructure, enabling multi-tenant isolation for SaaS, or supporting high-throughput analytics in logistics, FSD Tech customizes Cato SASE deployments for optimal performance and compliance in the GCC context.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts