
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Let’s start with a scene that might feel all too familiar.
You’re the CEO of a mid-sized logistics company in Lagos. It’s Friday evening, and your team is preparing for the weekend rush of deliveries. Then, just as you’re about to leave the office, your operations manager bursts in, pale and frantic:
“Sir, the warehouse systems just froze. We can’t access orders. Files are locked. The screen says we need to pay $70,000 in Bitcoin to get our data back.”
Your stomach drops. You remember signing off on antivirus licenses last year. You thought you were protected. But clearly… you weren’t.
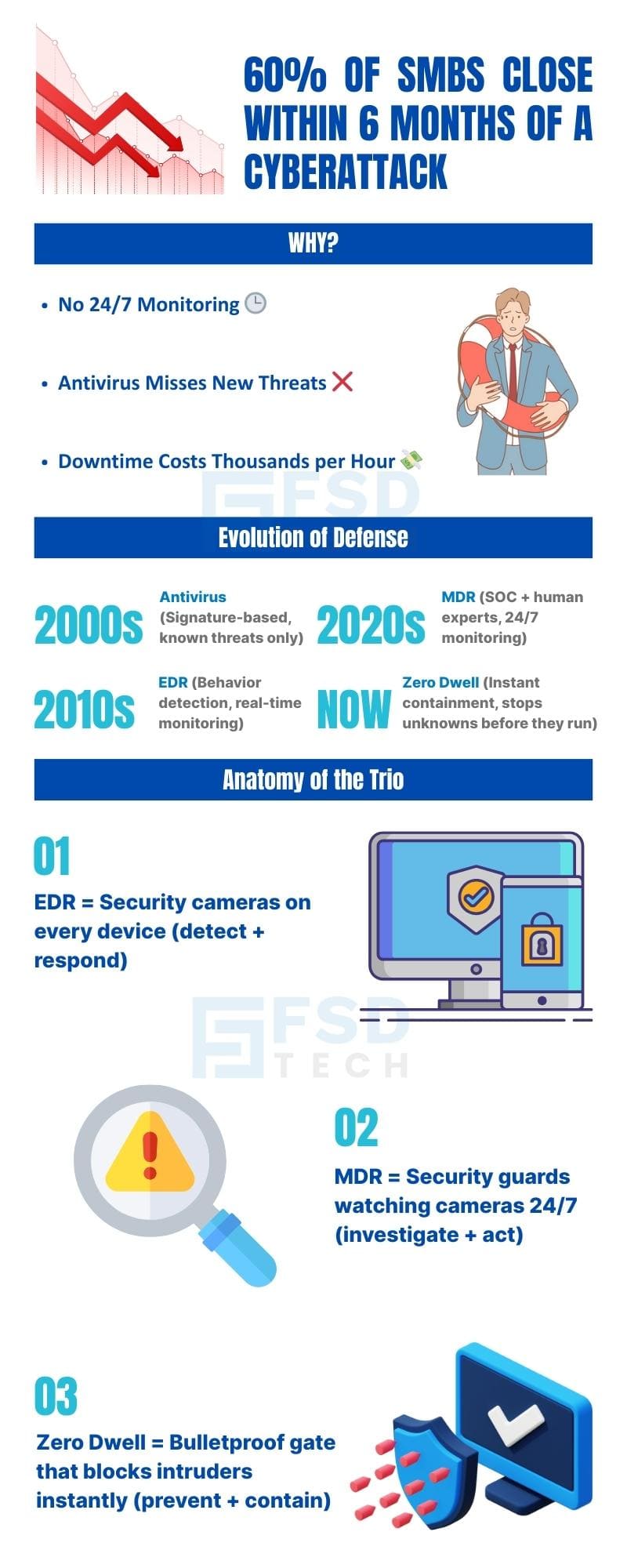
This is not a rare scenario. Across GCC and Africa, small and mid-sized businesses (SMBs) are now the number one target for cybercriminals. Why?
In fact, global studies show that 60% of SMBs shut down within six months of a major cyberattack.
But here’s the good news: You don’t need to build a massive IT department or spend millions to protect yourself like the big players do.
By combining three powerful technologies — EDR (Endpoint Detection & Response), MDR (Managed Detection & Response), and Zero Dwell Containment — you can create a security system that:
It’s like having a digital guard dog, a SWAT team on standby, and a bulletproof security gate all working together for your business — but at a price designed for SMBs.
Think about your business devices: laptops in Dubai, desktops in Nairobi, tablets in Johannesburg, and smartphones in Riyadh. Each of these is a doorway into your company.
If one of those doors is unlocked, a hacker can sneak in and wreak havoc.
This is where EDR comes in.
EDR is your always-on guard dog. It sits at every device and:
Analogy: Antivirus is like checking IDs at the door — but only for criminals you already know. EDR is like having security cameras inside every room, spotting unusual behavior, and locking down trouble before it spreads.
In other words, EDR doesn’t just recognize threats — it catches the unknowns that slip past antivirus.
Now imagine this: You’ve got those security cameras (EDR) in place. But who’s watching the footage at 3 AM?
If your business only has antivirus or EDR, you’re still relying on your IT manager — who is probably asleep, on leave, or overwhelmed by alerts.
That’s why you need MDR.
MDR is like hiring a 24/7 SWAT team for your business. It adds:
Analogy: Think of MDR as the emergency responders in your city. You hope you never need them. But when there’s a fire or a robbery, they arrive instantly — with training, tools, and strategies to save the day.
And the best part? With MDR-as-a-service, you don’t need to build that SOC yourself. It’s delivered to you on a monthly plan — enterprise-grade defense at SMB cost.
Here’s where it gets really powerful.
Most security systems work on a detect → respond model. They let a file run, then decide if it’s bad. That means there’s always a small window of risk.
But Zero Dwell Containment flips the model: contain → detect → allow.
It ensures that:
Analogy: Imagine an airport security check. Instead of letting passengers wander around and then chasing down the suspicious ones, Zero Dwell puts every new arrival into a holding area. Only after they’re cleared do they enter.
For SMBs, this means threats never even get a chance to start.
Many SMBs still think: “I have antivirus. I’m fine.”
The reality? Antivirus is yesterday’s protection. Hackers know how to bypass it easily.
Let’s break down why the EDR + MDR + Zero Dwell combo is unbeatable:
Together, they create defense in depth. If one layer misses something, the others catch it. If a file sneaks past, it’s still contained. If suspicious behavior is detected, experts jump in.
It’s prevention, detection, and response — all covered.
Want to see how this three-layer defense fits your business? Share your details and we’ll send you tailored insights. Click Here
Case: Logistics Company in Dubai
A logistics provider in Dubai received a Microsoft Word file from a trusted supplier. It looked routine — an invoice. But inside was a brand-new ransomware strain designed to bypass antivirus.
Here’s what happened with the trio in place:
Result:
The CEO later admitted: “Without this system, we would have been offline for days — maybe weeks. The cost would have been devastating.”
Curious how this trio would protect your own operations? Share your details and we’ll map a scenario for you. Click Here
Still wondering if this is worth it? Let’s look at the numbers.
Without EDR + MDR + Zero Dwell:
With the Trio:
Key Point: Prevention costs a fraction of recovery.
When you partner with FSD-Tech, you don’t just get tools — you get a fully managed security solution tailored for SMBs in GCC & Africa.
Here’s what’s included:
And most importantly: You don’t need extra staffing. Everything is managed for you.
One of the biggest fears SMBs have is: “Will this be too complicated for us?”
The truth? It’s simple. Here’s how onboarding works:
Consultation – FSD-Tech assesses your current IT setup.
Deployment – EDR, MDR, and Zero Dwell are installed across all devices remotely.
Monitoring – The SOC team begins 24/7 watch immediately.
Protection – You operate safely, knowing threats are stopped before they even start.
No need for expensive hardware. No disruption to your employees. Just instant peace of mind.
Let’s imagine three different SMB scenarios:
Your retail chain processes hundreds of card payments daily. One phishing email could expose customer data, triggering fines under NDPR and loss of customer trust. With the trio, phishing attempts are blocked before harm.
You’re responsible for compliance under UAE PDPL. Regulators demand proof of proactive monitoring. With the trio, you get compliance-ready reports showing exactly how threats are detected, contained, and neutralized.
You oversee operations across warehouses. Downtime from ransomware could halt supply chains. With the trio, suspicious files are isolated instantly, keeping operations smooth.
These aren’t just technical solutions — they’re business survival tools.
And perhaps most importantly: It gives you the same level of protection as global enterprises — without the massive cost or complexity.
Cybersecurity today isn’t optional. It’s as essential as insurance, accounting, or even electricity.
But here’s the good news: With EDR + MDR + Zero Dwell Containment, SMBs in GCC & Africa don’t have to choose between affordability and protection.
This trio delivers:
Together, they give you peace of mind, regulatory compliance, and the confidence to grow your business without fear of cyberattacks.
Final Thought: Cybercriminals don’t care whether you’re big or small. They only care if you’re unprotected. With this trio, you’re not just protected — you’re untouchable.
Ready to secure your business with EDR + MDR + Zero Dwell? Schedule a quick session with our experts today. Schedule Now
This is a three-layer cybersecurity system that gives small and mid-sized businesses enterprise-level protection.
Because each layer solves a different problem:
Together, they give prevention + detection + response — no gaps.
No. Antivirus mostly detects known threats using virus signatures. This trio stops both known and unknown threats, even if they’ve never been seen before.
Zero Dwell catches and isolates suspicious files instantly.
EDR then monitors and investigates the file’s behavior. If it’s dangerous, it’s blocked and reported.
EDR is automated. MDR adds human intelligence. The MDR team reviews alerts, confirms real threats, and responds — ensuring false alarms don’t slow your business.
No. With FSD-Tech’s SMB pricing, businesses in GCC & Africa can get the same security as a Fortune 500 company — at a cost they can afford.
No. Zero Dwell works in the background while employees continue working. EDR and MDR are optimized for performance.
Yes. Laptops and devices outside your office are protected the same way as in-office systems — essential for today’s work-from-anywhere model.
Zero Dwell acts instantly. EDR automation responds within seconds. MDR experts respond within minutes — even at 3 AM.
You’ll get detailed reports from the MDR team, including what was blocked, when, and how it was handled.
No. FSD-Tech deploys the system remotely across all your devices — usually in a single day — without disrupting work.
Yes. It meets GCC and African compliance requirements like UAE NESA, KSA NCA, South Africa POPIA, and Nigeria NDPR.
FSD-Tech offers flexible SMB plans. The cost is a fraction of what a single breach or ransomware payment would be.
We’re a GCC & Africa-based security partner offering:

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts