
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

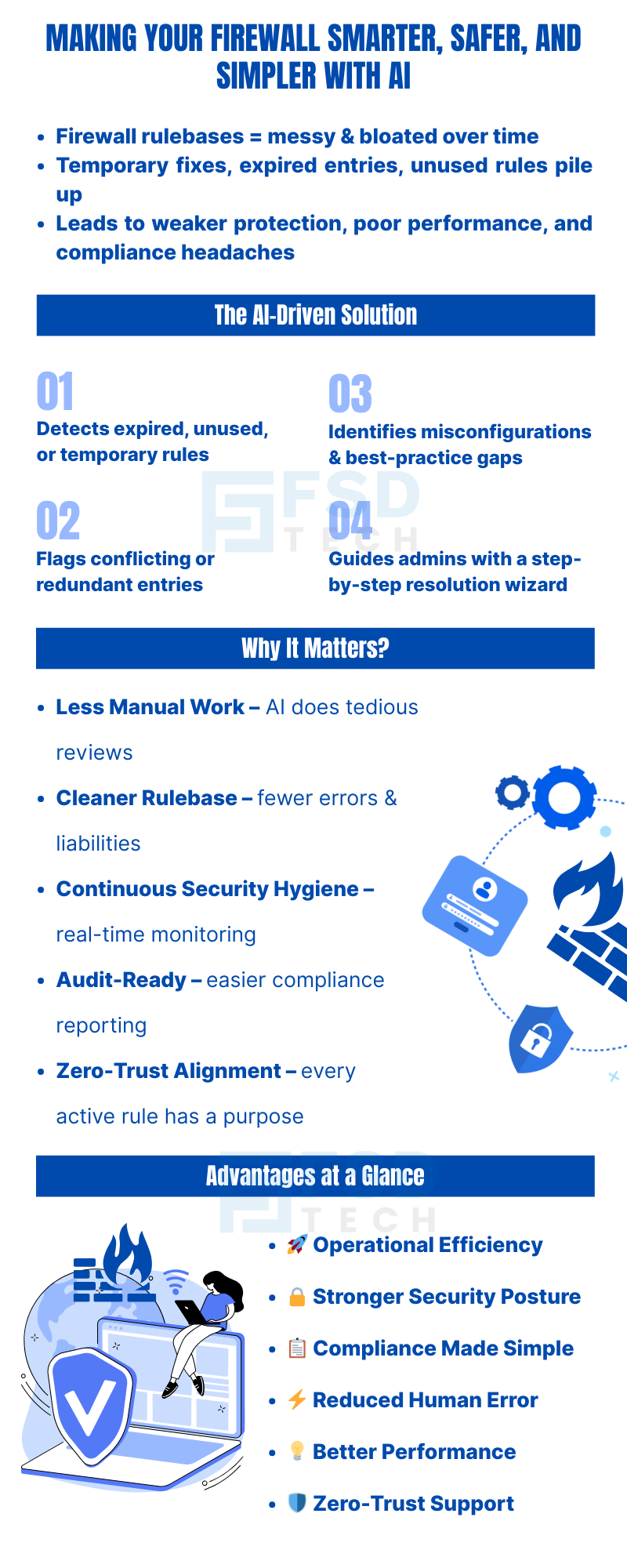
Firewall rulebases are at the heart of enterprise network security—but let’s be honest: they’re messy. Over time, temporary fixes, expired entries, and redundant rules accumulate, creating complexity that weakens both performance and protection. Security teams often spend hours manually combing through policies, only to miss risky configurations or face compliance headaches later.
Cato is addressing this challenge head-on with the introduction of AI-Driven Firewall Analysis and Insights, an enhancement to the Internet Firewall policy powered by the Autonomous Firewall engine. This feature brings automation, intelligence, and best-practice guidance to what used to be a time-consuming, error-prone task.
In this blog, we’ll explore what this means for IT administrators, how it helps simplify daily operations, and why it’s a game-changer for enterprise security and compliance.
The Autonomous Firewall Insights engine automatically analyzes the Internet Firewall rulebase and provides actionable recommendations. Instead of forcing admins to manually inspect hundreds of rules, it continuously scans for misconfigurations, redundant entries, and overlooked risks.
All of these findings are presented through a Firewall Configuration Wizard that guides administrators step by step in resolving issues—whether that’s deleting, disabling, or updating a rule.
From an administrator’s perspective, the feature translates into tangible improvements in daily security operations.
a) Less Manual Work, More Impact
Reviewing rulebases is one of the most tedious and repetitive security chores. With AI doing the heavy lifting, admins get clear, actionable insights—no more line-by-line reviews or chasing down stale entries.
b) A Cleaner, Leaner Firewall
A cluttered firewall isn’t just an annoyance; it’s a liability. By removing expired, unused, or temporary rules, admins maintain a streamlined rulebase that’s easier to manage and less prone to error.
c) Proactive Security Hygiene
Rather than waiting for a breach or audit to reveal a problem, the system continuously monitors and flags risks in real time. This allows teams to stay ahead of potential threats before they escalate.
d) Easier Compliance and Auditing
Auditors love clean, documented rulebases. With AI surfacing expired rules and enforcing best practices, organizations reduce compliance headaches and shorten audit preparation time.
e) Consistency With Zero-Trust Principles
The feature supports least-privilege access by pruning excessive or unnecessary permissions. Every rule that stays active has a purpose, reinforcing zero-trust security.
Let’s look at how this plays out in day-to-day operations:
Morning Check-In
An admin logs into the Cato Management Application and immediately sees flagged items: “Rule #45 expired yesterday” or “Testing rule active but unused for 30 days.” With a few clicks, they clean it up before it becomes a problem.
Midday Troubleshooting
A user reports blocked traffic. Instead of hunting through dozens of overlapping rules, the admin checks the insights panel, where conflicting rules are already highlighted. Resolution takes minutes, not hours.
Audit Prep
Compliance reviews no longer mean frantic policy rewrites. The system continuously validates rule health, so by the time auditors arrive, the firewall is already in top shape.
Long-Term Maintenance
Over months and years, rules don’t pile up unchecked. The AI ensures unused or outdated entries are flagged and removed, keeping the firewall consistently efficient.
Want a clearer view of your firewall risks? Get Your free Firewall Health Checklist.
Here’s what organizations gain from adopting this AI-driven capability:
| Advantage | What It Means |
|---|---|
| Operational Efficiency | Automates routine rule reviews, saving time and resources. |
| Stronger Security Posture | Removes weak points like expired or conflicting rules. |
| Audit & Compliance Readiness | Keeps rulebase clean, documented, and aligned with standards. |
| Reduced Human Error | AI highlights issues admins might overlook. |
| Improved Performance | Fewer rules = faster processing and leaner system operations. |
| Zero-Trust Alignment | Ensures firewall access remains minimal and purposeful. |
| Simplified Management | Delivered through an intuitive wizard in the Cato console. |
The Autonomous Firewall Insights feature isn’t a standalone upgrade—it’s part of Cato’s broader strategy to integrate AI-driven automation across its entire SASE platform.
Broader Enhancements Include:
The long-term vision is clear: shift security operations from reactive firefighting to proactive governance.
Scenario 1: The Forgotten Temporary Rule
A contractor was granted temporary internet access for a migration project. The rule was supposed to expire last month but didn’t. The AI flags it immediately, allowing the admin to remove a potential backdoor.
Scenario 2: Redundant “Allow” Policy
A broad “Allow All” rule sits unused for 45 days. The engine highlights it as unused, and the admin deletes it—reducing the attack surface significantly.
Scenario 3: Conflicting Entries
One rule allows access from a subnet, while another denies the same traffic. The insights tool lists them as contradictory, prompting a quick resolution.
The daily convenience is important, but the strategic benefits go even deeper:
For decades, firewall administration has been stuck in a manual loop: create, test, document, review, repeat. This cycle leads to bloated rulebases, missed risks, and overworked teams.
Cato’s Autonomous Firewall Insights marks a turning point. It’s not just about making administration easier—it’s about transforming how enterprises approach security policy altogether. By embedding AI-driven intelligence into daily workflows, organizations can move from a reactive mindset (fixing problems as they come) to a proactive, optimized posture where risks are anticipated and resolved automatically.
The introduction of AI-Driven Firewall Analysis and Insights is more than a new feature—it’s a rethinking of firewall management in the modern era.
For IT teams, it means fewer tedious reviews, a leaner and safer rulebase, and simplified compliance. For CISOs, it translates into stronger governance, reduced risk exposure, and operational efficiency. And for the business as a whole, it ensures that the network security foundation remains resilient, agile, and aligned with zero-trust best practices.
In an environment where threats evolve daily, autonomous, AI-driven security isn’t just nice to have—it’s essential.
See how Cato’s Autonomous Firewall Insights can simplify your security. Book your free Consultation today
AI-Driven Firewall Analysis And Insights is a feature powered by Cato’s Autonomous Firewall engine that continuously scans firewall rulebases for expired, unused, or conflicting rules. It provides actionable recommendations to simplify firewall management, strengthen enterprise network security, and ensure compliance.
Cato’s Autonomous Firewall Insights improves security by detecting temporary rules, redundant entries, unused “allow” policies, and misconfigurations. This ensures a cleaner, leaner, and safer firewall aligned with zero-trust security principles.
Yes. The AI engine automates rulebase reviews by flagging expired, testing, and unused rules, helping administrators eliminate clutter. This firewall optimization reduces complexity, minimizes risk, and boosts overall firewall performance.
By continuously monitoring firewall rules and highlighting expired or risky entries, AI-driven firewall analysis ensures rulebases remain audit-ready. This reduces compliance overhead, shortens audit preparation time, and aligns policies with industry standards.
The AI engine detects:
AI-Driven Firewall Analysis enforces least-privilege access by pruning unnecessary permissions. Every firewall rule that remains active serves a clear purpose, ensuring alignment with zero-trust firewall policies and reducing the attack surface.
Key benefits include:
Admins can quickly see flagged items like expired or unused rules during daily check-ins. Instead of manually scanning hundreds of rules, firewall analysis automation highlights issues in real time, saving hours and preventing misconfigurations.
Yes. The AI firewall engine scales seamlessly across hybrid, cloud, and multi-branch networks. It continuously optimizes rulebases regardless of size, making it ideal for large enterprise firewall management.
Enterprises should adopt this feature to reduce operational risk, maintain compliance, cut down manual effort, and proactively secure firewalls. By shifting from reactive fixes to autonomous firewall management, organizations achieve stronger governance and resilience.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts