
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how complex computer networks keep your data safe and moving? Most people use the internet daily without thinking about the invisible rules that govern it. One of the most important concepts in this field is the Triad. But what exactly does this term mean in a technical sense?
The Triad refers to a structural model used to manage information, security, and networking tasks. It is not just one thing. Instead, it acts as a three-pronged approach to solving digital problems. Whether you are looking at cybersecurity, data routing, or software design, these three pillars ensure everything runs smoothly.
Do you want to know how these systems protect your private files? Or perhaps you are curious about how they speed up your connection? Let us explore the world of the Triad and see why it is the backbone of modern tech.
The Triad can be understood as a framework that balances three competing or complementary elements to reach a specific goal. In the world of networking and security, it usually refers to the CIA Triad. This stands for Confidentiality, Integrity, and Availability.
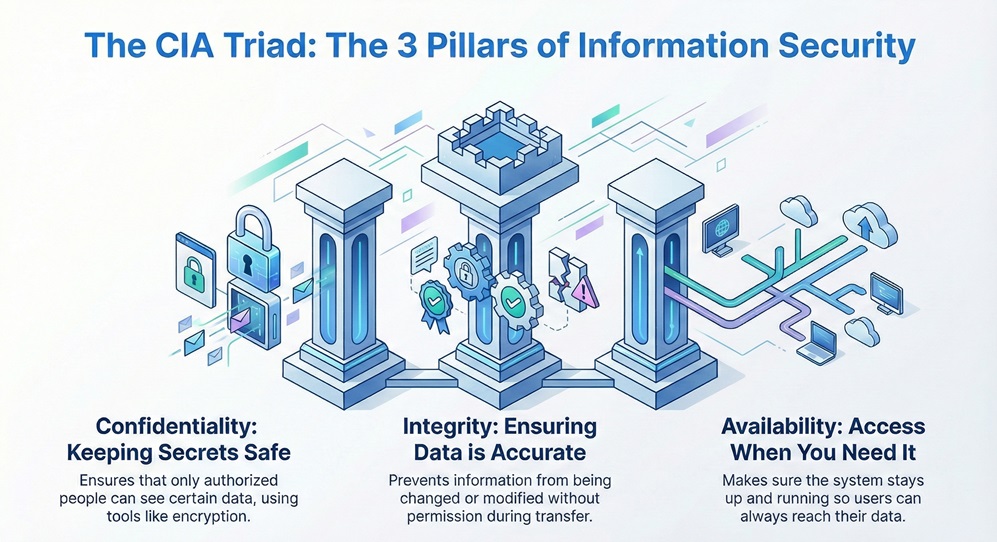
These three words form the holy trinity of information security. If one part fails, the whole system might crash or leak data. Engineers use this model to find weak spots in a network. By focusing on these three areas, they can build tools that resist hackers and hardware failures.
Is your system balanced? Get a Triad audit here.
To understand the Triad better, we should look at how different industries use three-part systems. While the security model is famous, networking and software have their own versions.
| Feature | CIA Triad (Security) | AIC Triad (Networking) | Strategic Triad (Defense) |
|---|---|---|---|
| Primary Goal | Data Protection | System Uptime | National Security |
| Core Element 1 | Confidentiality | Availability | Land-based assets |
| Core Element 2 | Integrity | Integrity | Sea-based assets |
| Core Element 3 | Availability | Confidentiality | Air-based assets |
| Key Risk | Data Breach | Service Outage | Total Failure |
Also Read: What is SQL Injection (SQLi) Attack? Examples & Prevention
The Triad plays a vital role in how we design content-centric networking. In older systems, the network cared about "where" a file was located. Now, modern systems care more about "what" the content is.
Content-routing allows a network to find the closest copy of a file. This reduces lag and saves bandwidth. To do this safely, the network must follow the Triad rules. It must verify that the content is real (Integrity) and make sure it is always ready (Availability).
The Triad acts as a guide for Content Delivery Networks (CDNs). Have you noticed how fast videos load on major platforms? That is because the data is spread across many servers.
This process relies heavily on the Integrity and Availability parts of the model. Without these, the internet would be slow and full of corrupted files.
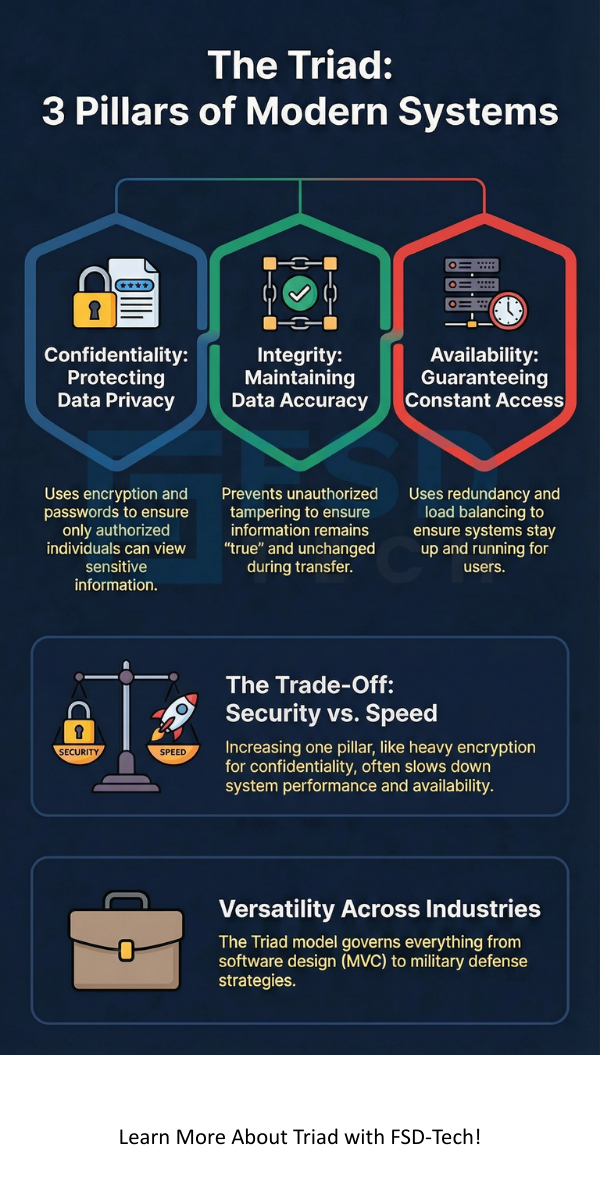
The Triad refers to specific design patterns in software engineering as well. One common example is the Model-View-Controller (MVC). This is a three-part system that separates how data is stored, how it looks, and how it moves.
The Triad in software helps developers work faster. Since the parts are separate, one person can fix the "look" of an app while another fixes the "database" without breaking everything.
By using this Triad, apps become much more stable. If the "View" has a bug, your data in the "Model" stays safe.
Also Read: What is Container Security? Best Practices, Tools, and Risks
The Triad is the first thing students learn in cybersecurity. It is the standard by which all security tools are measured. If you buy a new firewall, you ask: "Does this help my Confidentiality?"
The Triad focuses on keeping secrets. In a world of identity theft, this is crucial. Companies use Multi-Factor Authentication (MFA) to satisfy this pillar.
Now, the question arises: Is a password enough? Most experts say no. You need a second layer, like a code on your phone. This creates a stronger Triad defense.
The Triad also covers the "truth" of data. Imagine if a hacker changed the balance in your bank account. Even if they didn't steal the money, they ruined the Integrity of the data.
To prevent this, systems use digital signatures and hashing. These are mathematical tools that prove a file has not changed since it was sent.
The Triad must scale as companies grow. A small blog and a global bank both use these ideas, but at different levels. Scalability is the ability of the Triad to handle more work without failing.
The Triad helps manage distributed computing. When millions of people log in at once, the system must stay available.
These methods ensure the Availability pillar of the Triad remains strong even during peak hours.
Also Read: What is Network Sniffing? Attack and Prevention
The Triad sounds perfect, but it is hard to balance. Often, improving one pillar hurts another. This is known as a trade-off.
The Triad often creates friction. For example, if you add heavy encryption to protect Confidentiality, the system might slow down. This hurts Availability.
Engineers must find the "sweet spot." They want enough security to be safe, but enough speed to be useful. How do they decide? They look at the value of the data. A bank needs more security than a weather app.
The Triad also has a non-digital meaning. In defense, the Nuclear Triad refers to a three-part military structure. It includes land-based missiles, submarine-launched missiles, and strategic bombers.
The Triad in defense is about survivability. If an enemy destroys one part, the other two can still respond. This is very similar to how a computer network works. If one server goes down, the others take over.
The Triad is more than just a technical term. It is a philosophy of balance. By looking at the world through these three lenses, we can build better, safer, and faster systems. Whether you are a student or a business owner, understanding the Triad helps you make better choices about your digital life.
Our company believes in putting your data security first. We work hard to maintain the Integrity of every project we touch. Your trust is our most valuable asset. We are committed to providing reliable solutions that never leave you waiting. Let us help you build a system that stands the test of time.
Build a resilient network; contact our experts today.
The Triad is only as strong as its weakest link. If Confidentiality fails, you have a data breach. If Integrity fails, your data is wrong. If Availability fails, you cannot do your work.
The Triad is a goal, not a destination. It is very rare to have 100% success in all three. Most companies aim for "five nines" (99.999%) of Availability while keeping high levels of the other two.
The Triad remains the most used model in tech. Even with Artificial Intelligence and Cloud Computing, these three rules still apply. Every new gadget you buy follows these principles to stay safe.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts