
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Managing hundreds or thousands of devices can quickly become overwhelming without proper organization and categorization. IT teams need tools to segment devices by department, role, location, compliance status, or other custom parameters to maintain control, enforce policies effectively, and generate meaningful reports.
Miradore EMM provides robust tags and custom fields capabilities, allowing administrators to categorize devices with precision. This improves visibility, simplifies policy assignment, and enhances reporting for compliance and operational efficiency.
Large-scale device management requires more than simple device lists. Tags and custom fields help IT teams:
This granular categorization enables automated policy application, targeted notifications, and accurate reporting, reducing manual intervention and operational errors.
Tags are flexible labels that can be applied to devices manually or automatically based on predefined rules. Examples include:
While tags provide labels, custom fields allow IT teams to capture unique device attributes or organizational information. Examples include:
Custom fields can be text, numeric, or date types, providing structured data for reporting, automation, and analytics. They are particularly useful in large enterprises with complex device environments or regulatory obligations.
Miradore enables dynamic grouping, where devices automatically join groups based on tags, custom fields, or other attributes. This allows:
For example:
Tags and custom fields enhance reporting by:
This structured metadata ensures that enterprises remain audit-ready and simplifies demonstrating regulatory compliance, such as GDPR or ISO 27001 standards.
A multinational firm manages over 2,500 devices across multiple departments and sites. Using Miradore’s tags and custom fields, the IT team was able to:
This reduced manual work, improved operational visibility, and strengthened security and compliance enforcement across the organization.
Tags and custom fields are not just labels—they are powerful organizational tools that enhance security, compliance, and operational efficiency. Miradore EMM provides everything IT teams need to categorize devices accurately and enforce policies consistently across Android, iOS, macOS, and Windows.
If You Need Further Details On Any Specific Feature Or On Using Miradore EMM In Your Organization, Please Feel Free To Schedule a No-Obligation Requirement Gathering Virtual Meeting With Our Endpoint Management Experts. Schedule Now
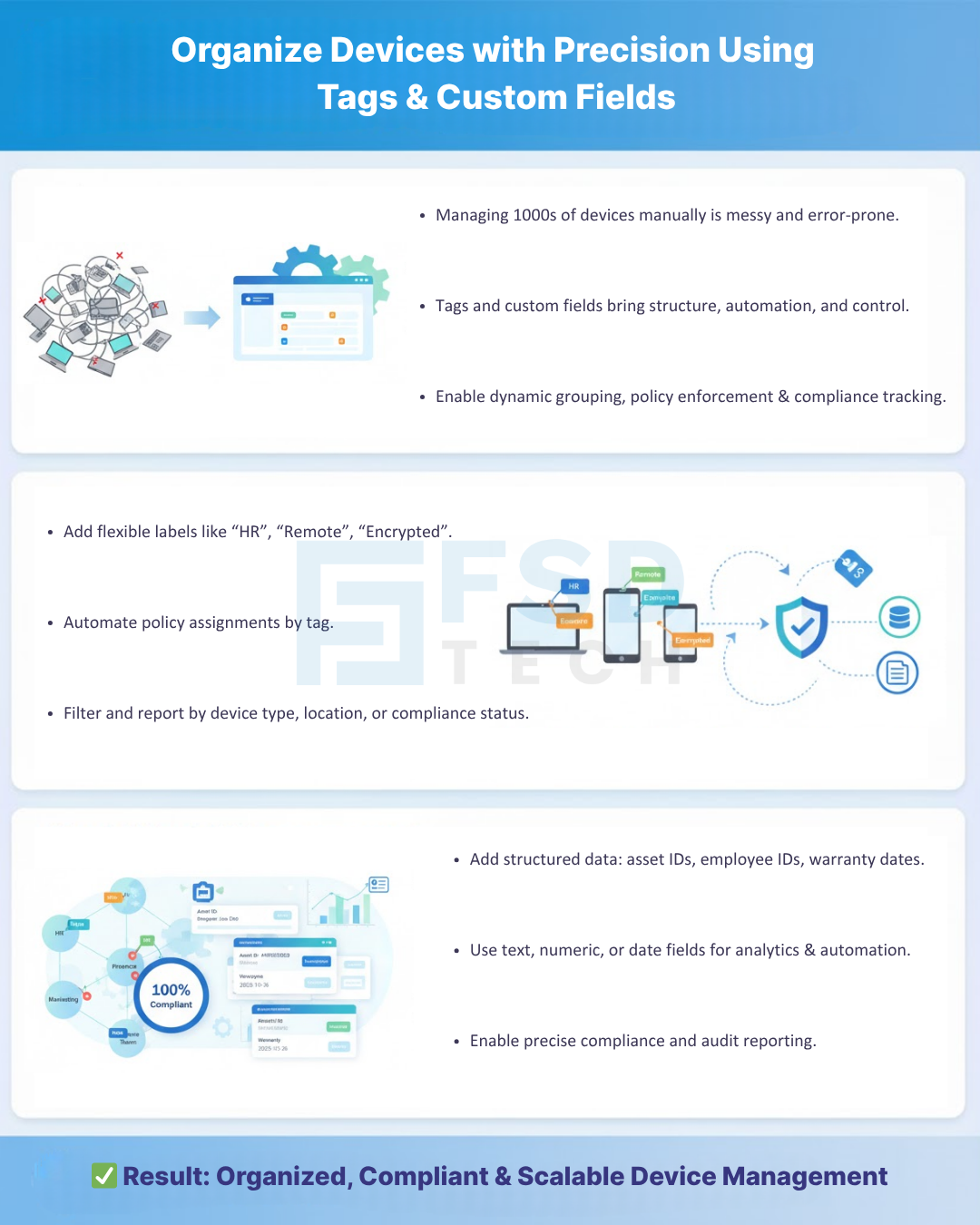
In Miradore EMM, tags are customizable labels applied to devices to logically group them by department, device type, location, compliance status, or any other attribute. Tags simplify device management and policy enforcement.
Miradore EMM custom fields allow IT teams to capture structured metadata about devices, such as asset IDs, employee IDs, warranty dates, or other organizational information, providing context beyond simple tags.
Yes. Miradore EMM supports dynamic policy assignment using tags and custom fields, automatically applying security, app, and compliance rules to relevant devices without manual intervention.
Absolutely. Miradore EMM allows devices to automatically join groups based on tags, custom field values, OS type, or other attributes, streamlining policy enforcement, reporting, and compliance management.
Yes. Miradore EMM provides structured metadata through tags and custom fields, enabling filtered, exportable, and auditable reports for regulatory compliance and internal audits.
Yes. Miradore EMM supports tagging and custom fields for BYOD devices, allowing IT teams to enforce corporate policies while maintaining user privacy.
Definitely. Miradore EMM tags and custom fields allow IT teams to organize devices across multiple sites, departments, and roles, enabling consistent device management, visibility, and reporting.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!

🕓 January 1, 2026

🕓 December 15, 2025

🕓 December 12, 2025
share your thoughts