
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

In today’s hybrid enterprise, devices are everywhere — laptops at home, IoT sensors in warehouses, mobile endpoints in the field. Yet, most organizations still rely on fragmented tools that only tell half the story about what’s connecting to their network.
Cato SASE changes that.
Through its Device Management Connectors for Microsoft Intune, CrowdStrike Falcon, and Zoom, Cato unifies endpoint intelligence across every device, user, and location — and brings it all together in a single pane of glass.
The result?
A seamless blend of visibility, compliance, and control that empowers IT and security teams to confidently enforce Zero Trust Network Access (ZTNA) policies — without complexity.
Traditional network tools struggle to connect the dots between device identity, compliance posture, and access behavior. Cato solves this challenge by introducing Device Management Connectors (DMCs) — built-in integrations that merge third-party endpoint data directly into the Cato Management Application (CMA).
These connectors collect metadata from trusted sources — such as CrowdStrike, Intune, and Zoom — and automatically combine it with Cato’s native Device Inventory engine, creating a single, dynamic view of every device in your organization.
This means IT teams can:
No more switching between consoles. No more manual mapping.
Just one Cato SASE platform — intelligent, unified, and always up to date.
Cato designed its Device Management Connectors to work the way modern enterprises do — open, API-based, and effortlessly scalable.
Integrates directly through OAuth authorization in CMA. Once connected, Intune device metadata (like OS version or model) syncs seamlessly into Cato’s Device Inventory.
Result: Gain visibility into every corporate endpoint — even before it connects to the network.
Links to the Falcon platform using API credentials to import security intelligence from managed devices.
Result: Identify and classify CrowdStrike-protected endpoints — and instantly separate compliant from non-compliant assets.
Connects via OAuth with your enterprise Zoom tenant to enrich device context with OS-level information.
Result: Extend visibility to collaboration endpoints — ensuring even meeting devices meet enterprise hygiene standards.
Each connector is displayed under Resources → Integrations → Integrated Apps in the CMA, complete with a Connected status indicator for verification.
Once integrated, these connectors become the foundation of intelligent access control inside Cato SASE.
Every connector enriches Cato’s Device Inventory engine, providing attributes like:
These attributes can be applied directly in WAN and Internet Firewall policies, enabling admins to define precise access logic such as:
“Allow only Dell Windows 11 laptops with CrowdStrike protection to access Office 365.”
Beyond visibility, Cato enforces compliance with Device Posture Profiles — checking for Anti-Malware, Disk Encryption, Firewall status, and even Running Processes (like the CrowdStrike agent).
Together, these tools form a multi-layered Zero Trust enforcement fabric, ensuring that both identity and device health are validated before granting access.
The Cato Management Application centralizes everything IT teams need to monitor connector health and device compliance:
Every decision — allow or block — is logged, auditable, and compliance-ready.
With Cato, enterprises gain a complete audit trail of who connected, from where, and on what device — all without relying on multiple vendors or standalone agents.
Cato’s Device Management Connectors are part of the Device Inventory license, included under Cato’s IoT/OT Security service.
Cato doesn’t just aggregate data — it connects intelligence across every control point.
By merging external endpoint insights with Cato’s own traffic analysis, organizations get the industry’s most unified visibility and control framework — built for Zero Trust, not retrofitted onto it.
In a landscape full of point solutions, Cato’s approach stands apart:
When every endpoint matters, every connection counts — and Cato ensures each one is secure, compliant, and context-aware.
If You Need Further Details On Any Specific Feature Or On Using Cato SASE In Your Organization, Please Feel Free To Schedule a No-Obligation Requirement Gathering Virtual Meeting With Our Network Security Experts. Schedule Now
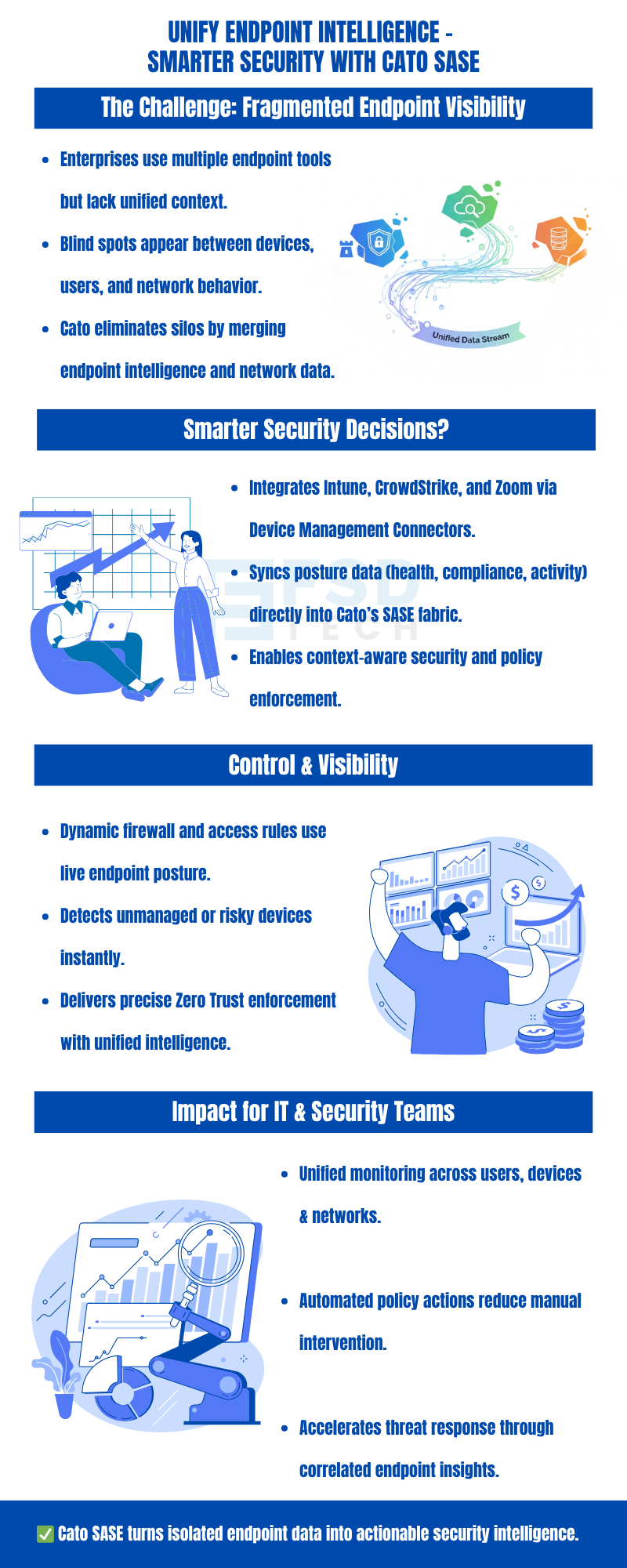
Cato’s Device Management Connectors integrate third-party platforms like Microsoft Intune, CrowdStrike, and Zoom to bring external device intelligence into Cato’s SASE platform, enabling complete endpoint visibility and Zero Trust enforcement.
By merging identity, posture, and device attributes, Cato SASE ensures that only verified, compliant, and contextually trusted devices can access the network — forming a key layer in Zero Trust policy enforcement.
Yes. Cato’s Device Inventory license, part of its IoT/OT Security service, is required to activate Device Management Connectors within the CMA.
Connectors enhance visibility and classification, while Device Posture Profiles enforce compliance through active checks like Anti-Malware, Firewall, or Disk Encryption before allowing network access.
Administrators can verify connector health under Resources → Integrations → Integrated Apps in the CMA. Each connector shows a Connected status, and all merged data appears in the Device Inventory and Device Dashboard pages.
Yes. Firewall rules can include Device Attributes derived from connector data, allowing admins to block unverified or unmanaged devices from network access.
Cato centralizes device and policy data within the CMA, offering dashboards and events that show posture results, policy hits, and connected device types — all exportable for audits and compliance verification.
Enable TLS Inspection and DHCP Service, verify license prerequisites, and ensure devices communicate regularly with the network. These measures maintain synchronization accuracy and device visibility.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts