.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

For enterprises operating in regulated environments—like banking, telecom, government, or healthcare—downtime is more than an inconvenience. It’s a breach of compliance, a disruption to end-user services, and a potential financial or legal liability.
Unfortunately, managing upgrades in OpenStack and Kubernetes clusters typically means scheduling outages, coordinating multi-day windows, and accepting operational risk. Traditional methods force ops teams to weigh feature updates against the cost of interruption.
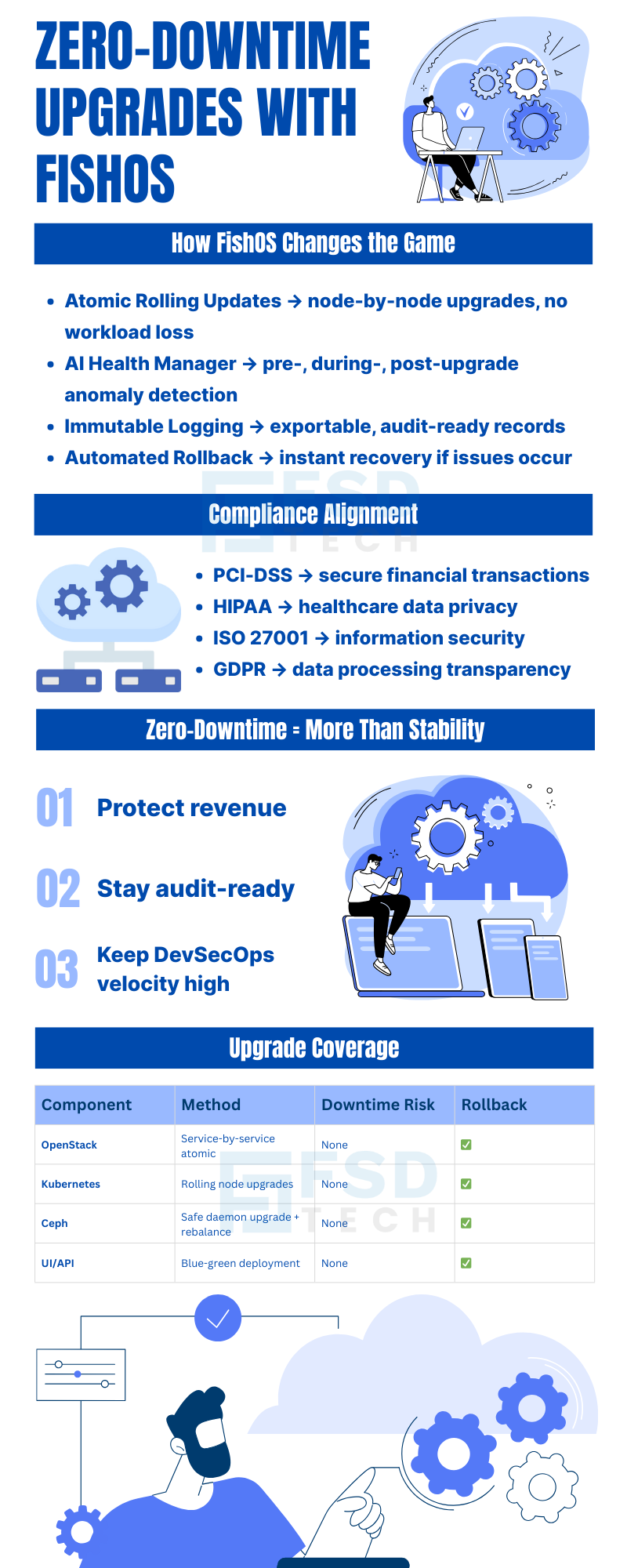
FishOS by Sardina Systems changes that equation. Through automation and atomic rolling update processes, FishOS Upgrader enables zero-downtime upgrades across the entire private cloud stack—including OpenStack, Kubernetes, Ceph, and supporting services.
This blog explores how FishOS accomplishes this, and why it’s becoming the gold standard for enterprise-grade cloud lifecycle management.
| Benefit | What It Means for You |
|---|---|
| Zero-Downtime Upgrades | No service disruption, no downtime planning required |
| Simplified Process | Automated, hassle-free upgrades with fixed-price license |
| Always Up-to-Date | Continuous access to the latest OpenStack features & security enhancements |
| Expert Assistance | Sardina’s technical team provides planning & execution tailored to your systems |
In legacy OpenStack and Kubernetes environments, upgrades are notoriously fragile. Common challenges include:
In regulated industries, these risks are unacceptable. Downtime must be avoided at all costs, and upgrade logs must be traceable and secure.
FishOS performs updates in a granular rolling manner:
This ensures:
Before upgrades:
During upgrades:
After upgrades:
This resilience guarantees safe, reversible upgrades every time.
Every action is:
Suitable for regulated environments requiring PCI-DSS, HIPAA, ISO 27001, GDPR compliance.
Need to guarantee uptime while keeping your infrastructure patched and secure? Book a Free consultation with our experts today.
Imagine being a cloud platform owner at a FinTech provider in the UAE, responsible for:
With FishOS Upgrader, you can:
Enterprises using FishOS in regulated environments report:
Zero-downtime upgrades aren’t just a technical achievement—they’re a business advantage.
FishOS proves that private cloud can be agile, compliant, and always-on—if designed with automation and reliability at its core.
Need to guarantee uptime while keeping your infrastructure patched and secure?
Request a free consultation with our experts to see how FishOS Upgrader can transform your private cloud lifecycle. Schedule Now
The FishOS Upgrader automates rolling updates across controllers, compute nodes, and services, ensuring workloads—including stateful ones—remain online.
A full upgrade typically completes in 2 working days: one for the upgrade and one for post-upgrade checks.
Yes—upgrades are fully automated but policy-controlled. Sardina or FSD admins initiate the process, while the system executes orchestration, validation, and rollback safety.
All actions are immutably logged, exportable for PCI-DSS, HIPAA, GDPR, and ISO 27001 audits. CVE patches are applied quickly without downtime, aligning with compliance expectations.
Yes. FishOS is designed to manage over 1000 physical servers with a single operator, making it suitable for large-scale regulated enterprises.
Downtime can breach SLAs and trigger audit failures. FishOS ensures compliance while applying updates, preventing costly outages in FinTech, healthcare, telecom, and government sectors.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts