.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Zero Trust does not start at the firewall.
It starts before a connection is ever allowed.
Many organizations focus on controlling what users can access after they connect. However, this approach leaves a critical gap: unverified users and devices are still allowed onto the network fabric. Cato SASE closes this gap by enforcing access decisions pre-connection using the Client Connectivity Policy.
This blog explains how the Client Connectivity Policy functions as the first enforcement gate in Cato SASE—controlling who can connect, under what conditions, and why this model is foundational to scalable Zero Trust.
In traditional remote access architectures:
This sequence assumes trust too early.
Zero Trust requires the opposite approach:
The Client Connectivity Policy enables this shift by enforcing access decisions before traffic reaches the WAN or Internet firewall layers.
The Client Connectivity Policy defines who is allowed to connect to Cato SASE and under what conditions.
Rather than controlling application access, it controls network admission.
This makes the policy a foundational component of Zero Trust enforcement within Cato Networks.
Cato SASE enforces security in layers, not silos.
The Client Connectivity Policy operates upstream of firewall enforcement, ensuring only compliant users and devices ever reach policy evaluation.
The Client Connectivity Policy evaluates two critical signals:
If these requirements are not met, the connection is denied—without exposing the network.
Non-compliant devices never enter the network fabric, reducing lateral movement risk.
Firewall rules no longer need to compensate for unverified endpoints.
Every connection follows the same admission logic, regardless of location.
This design aligns Zero Trust with operational reality—simple, enforceable, and scalable.
The Client Connectivity Policy is not a black box.
Security teams gain visibility into:
This transparency supports both operational troubleshooting and audit readiness.
By enforcing Zero Trust before connection, organizations gain:
Rather than reacting to threats inside the network, Cato SASE prevents them from entering in the first place.
Zero Trust fails when enforcement begins too late.
Cato SASE succeeds because:
The Client Connectivity Policy transforms Zero Trust from a concept into an enforceable operating model.
Need help enforcing identity- and device-based access in Cato SASE→ Schedule your 30-minute Zero Trust strategy session today.
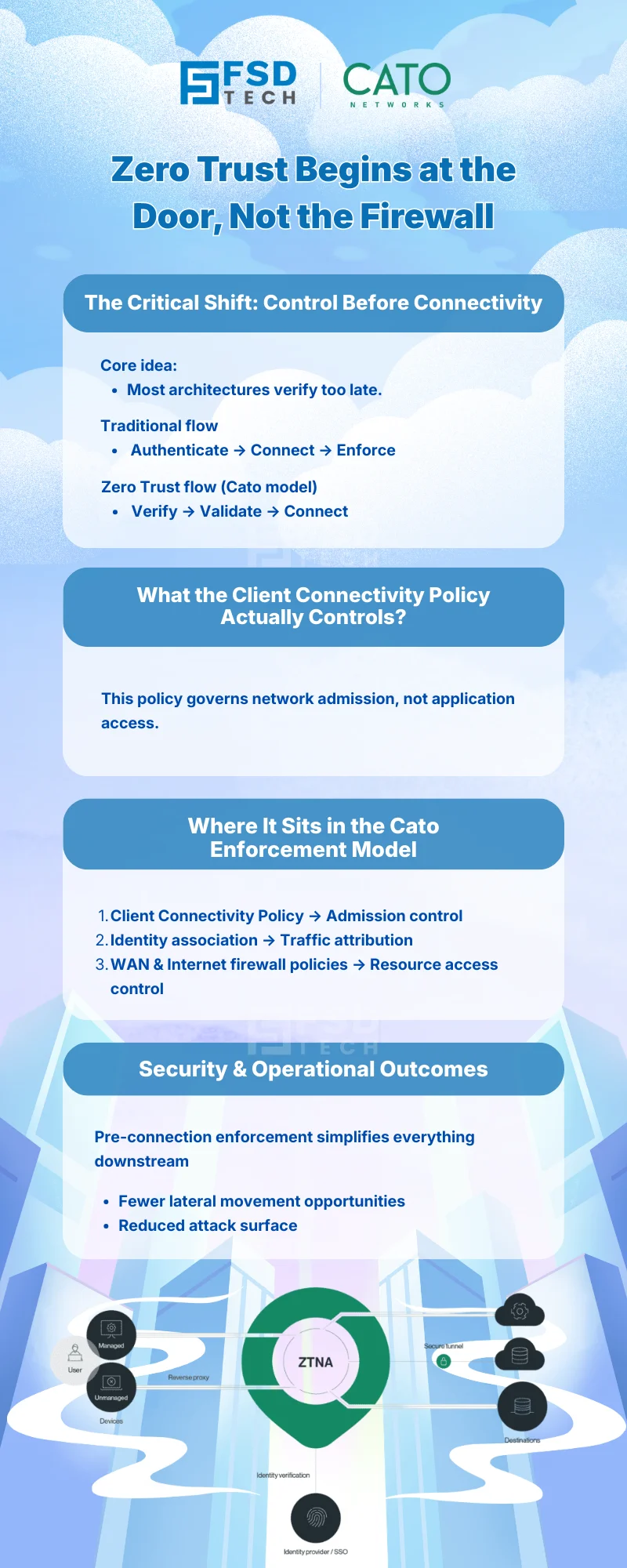
The Client Connectivity Policy in Cato SASE controls whether a user and device are allowed to connect to the network at all, enforcing Zero Trust principles before any network access is granted.
Client Connectivity Policy governs network admission, while Cato SASE firewall policies control resource access after connection. Both work together, but at different stages.
Yes. The Client Connectivity Policy is essential in Cato SASE to ensure identity and device posture are verified before connectivity, which is fundamental to Zero Trust.
Yes. Cato SASE enforces Client Connectivity Policy upstream of firewall evaluation, preventing unverified users or devices from entering the network fabric.
By stopping non-compliant connections early, the Client Connectivity Policy reduces firewall complexity, lowers alert noise, and simplifies troubleshooting.
Yes. Cato SASE applies Client Connectivity Policy uniformly, ensuring the same Zero Trust admission logic regardless of user location.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts