.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

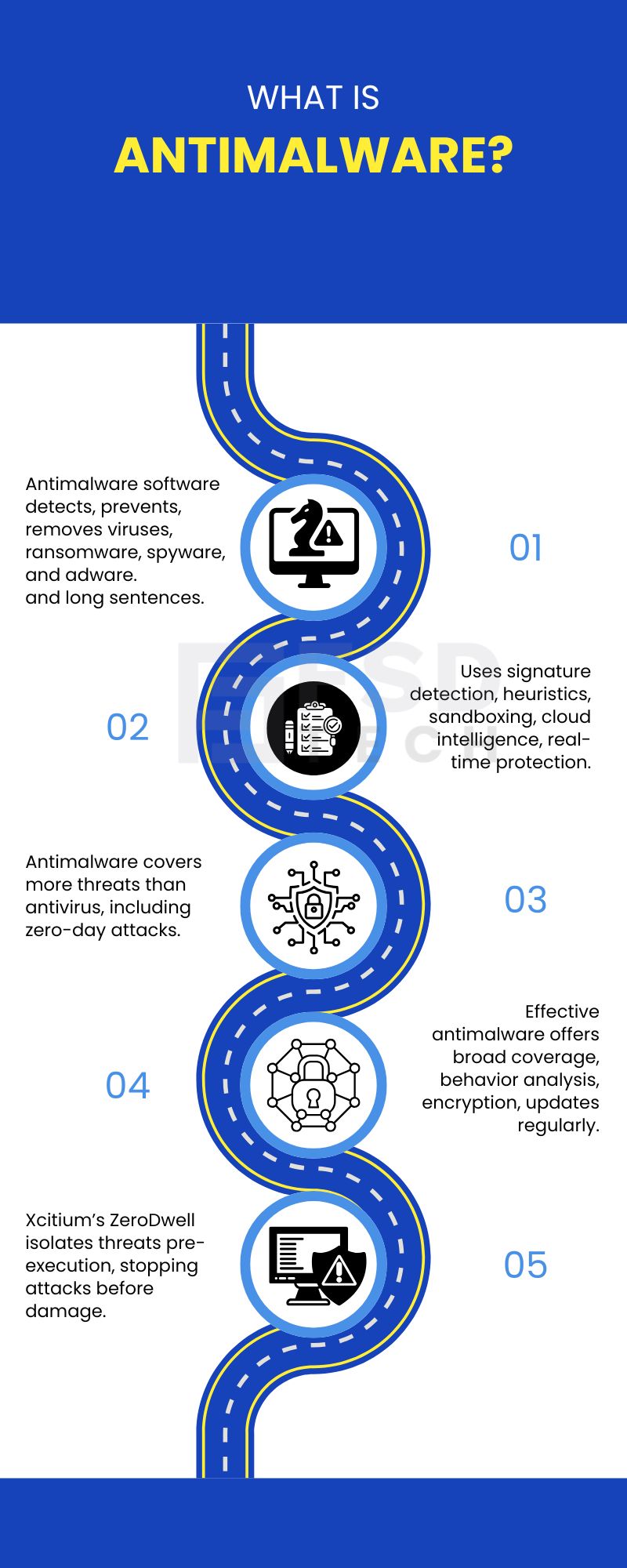
Nowadays, a single malicious file is enough to stop your business cold. Malware isn’t just a threat—it’s the most common doorway into system compromise, data loss, and operational shutdowns. That’s why antimalware matters. It is the specialized software designed to detect, prevent, and remove harmful programs such as viruses, ransomware, spyware, and adware.
But here’s something many organizations overlook:
Most antimalware tools still rely on identifying the threat after it has begun executing.
That tiny window—measured in milliseconds—is where ransomware wins.
Modern antimalware must go beyond old detection logic. It needs stronger, smarter methods capable of defending against both known threats and completely new, never-seen-before attacks.
Your data, systems, and business continuity depend on it.
To understand antimalware in clearer terms, you must know its different defense layers. Antimalware tools use various methods to keep your systems safe. They don't rely on just one trick.
There are several steps to how anti-malware works:
But here’s the crucial limitation:
all of these methods still depend on detection—meaning the file is allowed to start running.
And modern threats don’t need long to cause damage.
This is the gap Xcitium eliminates.
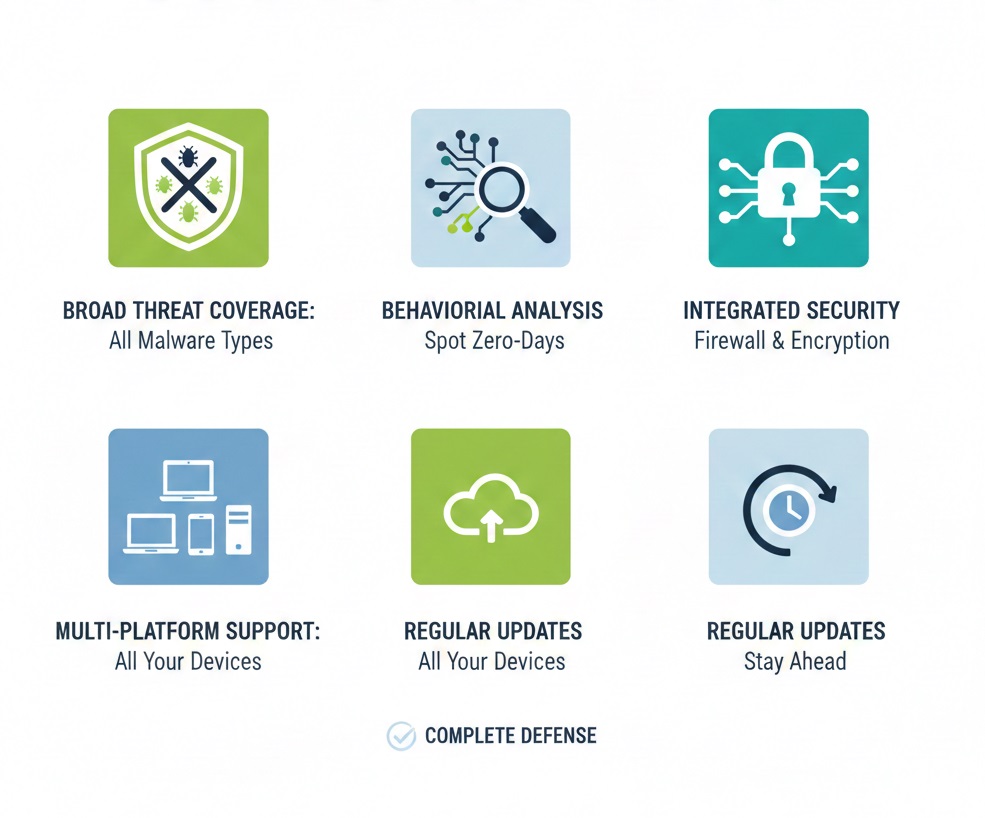
A strong antimalware solution is more than just a basic scanner. It is to be noted that it must offer several key features for complete threat defense.
Here are the most important characteristics:
But even with all this, detection-based systems still leave a gap for unknown threats.
This is where Xcitium’s approach becomes far more compelling.
Also Read: Why Cybersecurity Is a Business Growth Strategy – Not Just a Cost
The terms antimalware and antivirus are often used as if they mean the same thing. However, they are different tools. Antimalware can be understood as an evolution of traditional antivirus.
To understand the difference between antimalware and antivirus in clearer terms, consider the following key points:
| Feature | Antimalware | Antivirus |
|---|---|---|
| Scope of Protection | Broad protection against various malware (ransomware, spyware, etc.) | Mainly focused on viruses |
| Malware Types Covered | Viruses, spyware, ransomware, adware, etc. | Primarily viruses |
| Behavioral Analysis | Emphasizes behavior-based detection | Mostly signature-based |
| Scanning Techniques | Heuristics, sandboxing, cloud lookups | Signature-based file scanning |
Selecting the right product is a critical decision for your security. Always remember, the best antimalware solution is one that meets your specific needs.
When selecting an antimalware product, you should consider these specified factors:
And one more critical factor:
How does the solution handle unknown threats?
This is where Xcitium changes the entire equation.
Also Read: Cybersecurity ROI – Why Investing in Protection Saves SMBs More Than It Costs
At FSD Tech, we understand that modern cyber risks cannot be addressed with detection-based tools alone. That is why we partner with Xcitium, a leader in Zero Trust endpoint security, to provide advanced antimalware capabilities designed for today’s threat landscape.
Xcitium’s patented ZeroDwell™ Containment technology brings a breakthrough approach that stops unknown threats before they ever touch your operating system. Instead of trying to detect whether an unknown file is malicious, Xcitium isolates it instantly — eliminating the risk of ransomware, zero-days, or fileless attacks causing damage.
This pre-execution model is the key reason Xcitium stands out from traditional antimalware vendors.
Xcitium uses a multi-layered, prevention-first approach that is fully aligned with Zero Trust principles. Here are the capabilities that make it unique:
ZeroDwell™ Containment (Patented)
Xcitium automatically isolates unknown or untrusted files in a secure virtual environment before they execute.
This ensures that even if the file is malicious, it cannot impact the real system.
No other vendor offers this patented, kernel-level containment technology.
Suspicious files are analyzed using a combination of:
This delivers fast, accurate verdicts without guesswork.
Monitors application behavior in real time to detect malicious actions such as privilege escalation, keylogging, or code injection.
Includes advanced heuristics, machine learning classification, and cloud lookups to identify known and emerging malware.
Endpoint Protection & Hardening
Xcitium includes additional security layers such as:
Xcitium offers 24/7 expert-led monitoring, threat hunting, and incident response for organizations that need continuous security operations support.
All of these capabilities work together to ensure full visibility, rapid detection, and—most importantly—pre-execution protection that stops attacks before they begin.
Below is a clear comparison against traditional antimalware vendors:
| Feature | Traditional Antivirus / NGAV | Xcitium ZeroDwell™ |
|---|---|---|
| Unknown File Handling | Allowed to run → then detected | Contained instantly → cannot harm |
| Zero-Day Protection | Depends on detection speed | Guaranteed by isolation |
| Ransomware Prevention | Often too slow | Blocked before encryption starts |
| Fileless Attacks | Hard to identify | Contained automatically |
| False Positives | Frequent | Minimal due to safe containment |
| Dependency on Signatures | High | Low – uses verdicting |
Technology alone is not enough. You need the right partner to deploy, configure, and optimize your cybersecurity stack.
FSD Tech brings:
Deployment Expertise
We implement Xcitium’s ZeroDwell™, NGAV, and cloud-based analysis capabilities with the right policies for your environment.
Security Architecture Tailored to Your Organization
Proper containment rules, endpoint policies, access controls, and monitoring setups ensure maximum protection without interrupting productivity.
Continuous Support & Monitoring
Our team ensures your environment stays protected, updated, and fully optimized.
Integration Across Your Entire IT Landscape
We help integrate Xcitium with SIEMs, cloud workloads, on-premise systems, and your incident response workflows.
Together, Xcitium and FSD Tech deliver a complete, prevention-first antimalware strategy designed for today’s rapidly evolving threat landscape.
Strong antimalware is essential to securing your business. But modern cyber threats demand more than detection-based tools. They require a prevention-first approach — one that stops unknown threats before they ever have the chance to execute.
Xcitium’s ZeroDwell™ Containment brings exactly that.
And with FSD Tech’s implementation expertise, your organization gets a tailored, fully optimized security experience that ensures business continuity, data protection, and long-term resilience.
If you want prevention instead of reaction —
Xcitium with FSD Tech is the right choice.
Antimalware: Offers broad protection against many types of malicious software, including viruses, ransomware, spyware, and adware, using advanced detection methods like heuristics.
Antivirus: Primarily focuses on known viruses with signature-based detection.
Yes, it is to be noted that antivirus alone may not be enough for modern threats. Antimalware provides essential additional layers of protection, especially against advanced malware like ransomware, fileless malware, and zero-day exploits.
Yes, modern antimalware solutions include real-time protection, behavioral analysis, and sandboxing. These features detect and block ransomware before it can encrypt your files or demand payment.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts