.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Ransomware in 2025 is defined by rapid evolution and increasing attacker sophistication. The number of active ransomware groups has surged by 20–30% year-over-year, even as overall attack volumes fluctuate. This fragmentation, combined with the emergence of agile, specialized gangs, has made attribution and defense more challenging for security operations centers (SOCs).
Attackers now routinely employ double and triple extortion—encrypting data, threatening public leaks, and targeting supply chain partners to maximize leverage. Industrial and critical infrastructure sectors are prime targets, with adversaries exploiting zero-day vulnerabilities and supply chain relationships to bypass traditional defenses.
The financial and operational consequences of ransomware continue to escalate. In 2025, the average cost of a ransomware breach has reached USD 5.08 million, with global damages projected to exceed USD 275 billion annually by 2031. Beyond direct financial loss, organizations face reputational damage, regulatory penalties, and prolonged operational downtime.
For cybersecurity strategists and SOC leads, the imperative is clear: resilience requires not only rapid detection but also unified, proactive defense that adapts as quickly as the threat landscape evolves.
Attackers are refining their initial access techniques. In 2025:
The convergence of social engineering and technical exploitation demands layered, adaptive defenses.
The median time from initial intrusion to ransomware execution has dropped to just 5 days. Only 17% of attacks are detected during the reconnaissance phase, underscoring the need for continuous monitoring and automated response. Attackers prioritize speed and stealth, often moving laterally and escalating privileges before deploying ransomware payloads.
Modern ransomware campaigns leverage:
These tactics amplify the impact and complexity of response, requiring organizations to rethink traditional perimeter-based defenses.
Zero trust has become foundational for ransomware defense in 2025. By continuously authenticating and authorizing every user and device, zero-trust architectures prevent attackers from moving laterally—even after initial compromise. This approach is especially critical as hybrid work models blur the boundaries between corporate networks and remote endpoints.
Fragmented security stacks create dangerous blind spots. Unified SASE platforms deliver:
This level of integration is now considered a baseline requirement for ransomware resilience.
Operational complexity is a silent enabler of breaches. Multi-vendor or piecemeal SASE deployments can result in inconsistent policy enforcement, delayed response, and increased management overhead. Converged platforms, such as Cato SASE, apply security policies uniformly and instantly, minimizing gaps and maximizing resilience.
Cato SASE’s cloud-native architecture processes all security and networking functions in a single pass. This reduces latency and operational friction, ensuring that:
are applied consistently, regardless of user location or device type. The result is a unified security posture that adapts to evolving ransomware tactics without introducing complexity.
Cato SASE leverages real-time threat intelligence and automated response to identify and block ransomware payloads before execution. Inline inspection of both encrypted and unencrypted traffic ensures that even sophisticated attacks—such as those exploiting zero-day vulnerabilities—are detected early. Automated containment mechanisms further reduce the window of exposure.
Hybrid work introduces new attack surfaces. Cato SASE’s zero-trust network access (ZTNA) secures both remote and on-premises users, enforcing least-privilege access and continuous verification. This prevents attackers from exploiting compromised credentials or moving laterally within the network, even as workforces become more distributed.
Also Read: How SASE Supports the Security Needs of SMBs
FSD Tech acts as the GCC’s regional enabler for Cato SASE, ensuring that enterprises benefit from world-class ransomware defense tailored to local requirements. This partnership bridges the gap between global innovation and practical, region-specific deployment.
FSD Tech delivers:
This regional enablement is critical for organizations seeking to balance advanced security with operational realities in the Middle East.
Consider a multinational manufacturer in the GCC targeted by a phishing campaign aimed at remote workers. Employees receive emails with malicious attachments designed to deploy ransomware. With Cato SASE enabled by FSD Tech:
This scenario illustrates how unified SASE platforms can disrupt the ransomware kill chain at multiple stages.
In Q2 2025, industrial organizations experienced a surge in attacks exploiting zero-day vulnerabilities. Enterprises relying on fragmented security stacks struggled with visibility and response, resulting in significant downtime. In contrast, those using unified SASE platforms like Cato SASE detected and contained threats within hours, preserving operational continuity and demonstrating the value of architectural simplicity.
Stop Ransomware Before It Starts -> Book Your Cato SASE Ransomware Resilience Consultation Now.
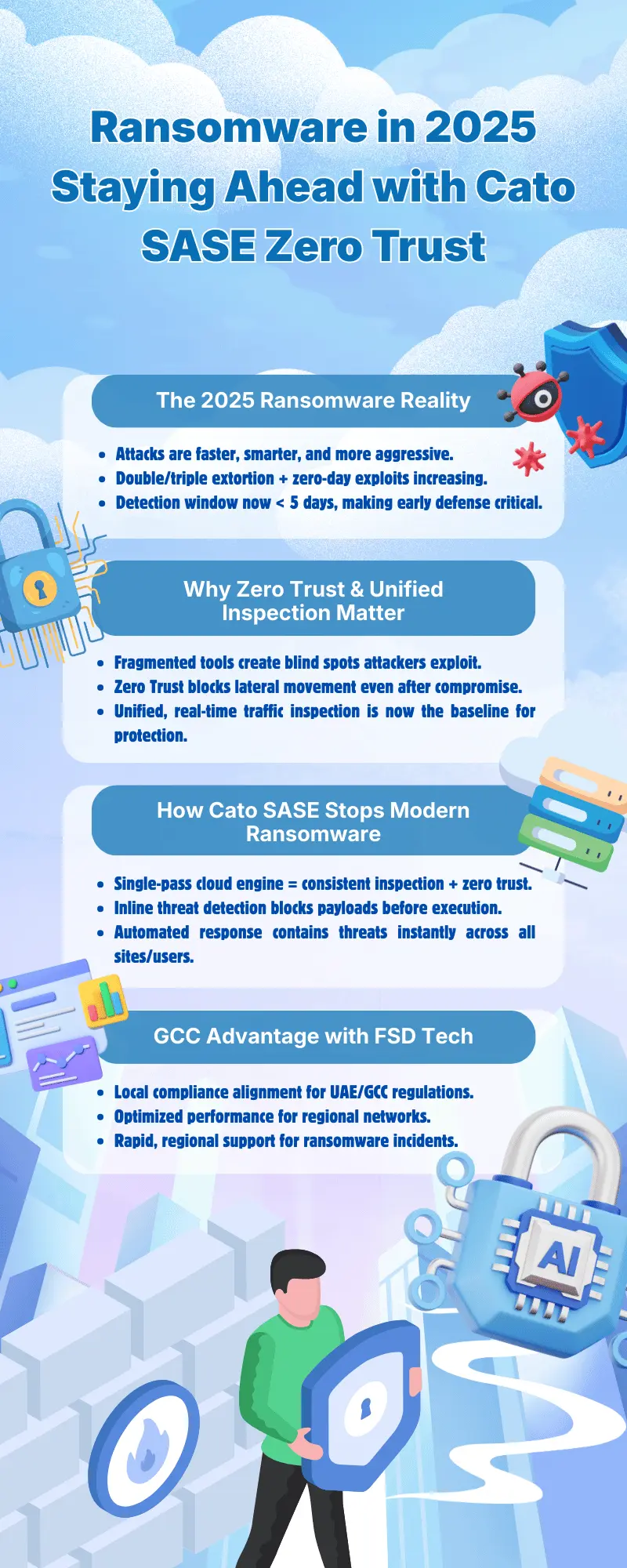
Ransomware attacks in 2025 are characterized by increased sophistication, including double and triple extortion, exploitation of zero-day vulnerabilities, and a rise in supply chain attacks. The number of active ransomware groups has also grown significantly, making attribution and defense more complex.
Zero trust ensures that every user and device is continuously authenticated and authorized, preventing attackers from moving laterally within the network even if they gain initial access. This approach is essential for defending against modern ransomware tactics that bypass traditional perimeter defenses.
Cato SASE’s single-pass cloud engine delivers unified security and networking functions in one streamlined process. This reduces operational complexity and eliminates the gaps and blind spots often found in multi-vendor or fragmented SASE solutions, providing more consistent and effective ransomware protection.
FSD Tech acts as the regional enabler for Cato SASE in the GCC, ensuring that deployments are tailored to local regulatory, operational, and performance requirements. Their expertise bridges global innovation with local execution, supporting compliance and providing rapid, region-specific support.
Yes, when implemented with real-time threat detection, inline inspection, and zero-trust access, SASE platforms can detect and block ransomware before data encryption occurs. The unified approach of platforms like Cato SASE is particularly effective against fast-moving campaigns.
The first step is to assess your current security architecture for gaps in visibility, access control, and threat detection. Prioritizing the deployment of a unified SASE platform with integrated zero-trust and real-time detection is key to comprehensive protection.
Unified traffic inspection ensures that all network traffic—whether encrypted or unencrypted—is analyzed for malicious activity. This helps detect ransomware payloads and command-and-control communications early, enabling faster response and containment.
Fragmented security stacks often lead to inconsistent policy enforcement, delayed response times, and blind spots in visibility. Attackers can exploit these gaps to bypass defenses or move laterally within the network, increasing the risk of successful ransomware attacks.
Cato SASE provides seamless zero-trust network access (ZTNA) for both remote and on-premises users. This ensures that access is always least-privilege and continuously verified, regardless of user location, reducing the risk of credential-based attacks and lateral movement.
FSD Tech ensures that Cato SASE implementations meet GCC-specific regulatory requirements, such as data residency, privacy, and sectoral compliance mandates. This helps organizations avoid penalties and maintain trust with local stakeholders.
Cato SASE’s real-time threat detection and automated response mechanisms enable organizations to detect and contain ransomware threats within hours, significantly reducing the window of exposure compared to traditional or fragmented solutions.
The leading causes include exploited vulnerabilities, phishing attacks, compromised credentials, lack of cybersecurity expertise, and unknown security gaps. Unified SASE platforms help address these issues by providing consistent visibility and automated protection.
Cato SASE performs inline inspection of both encrypted and unencrypted traffic, ensuring that threats hidden within encrypted flows are detected and blocked without introducing significant latency or operational overhead.
FSD Tech offers rapid incident response, local expertise, and ongoing support to help organizations contain and recover from ransomware attacks. Their regional presence ensures that support is aligned with local business practices and regulatory requirements.
Organizations should track detection and response times, regularly test incident response plans, monitor for unknown security gaps, and use unified dashboards for visibility. Continuous improvement and adaptation to evolving threats are essential for maintaining resilience.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts