
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

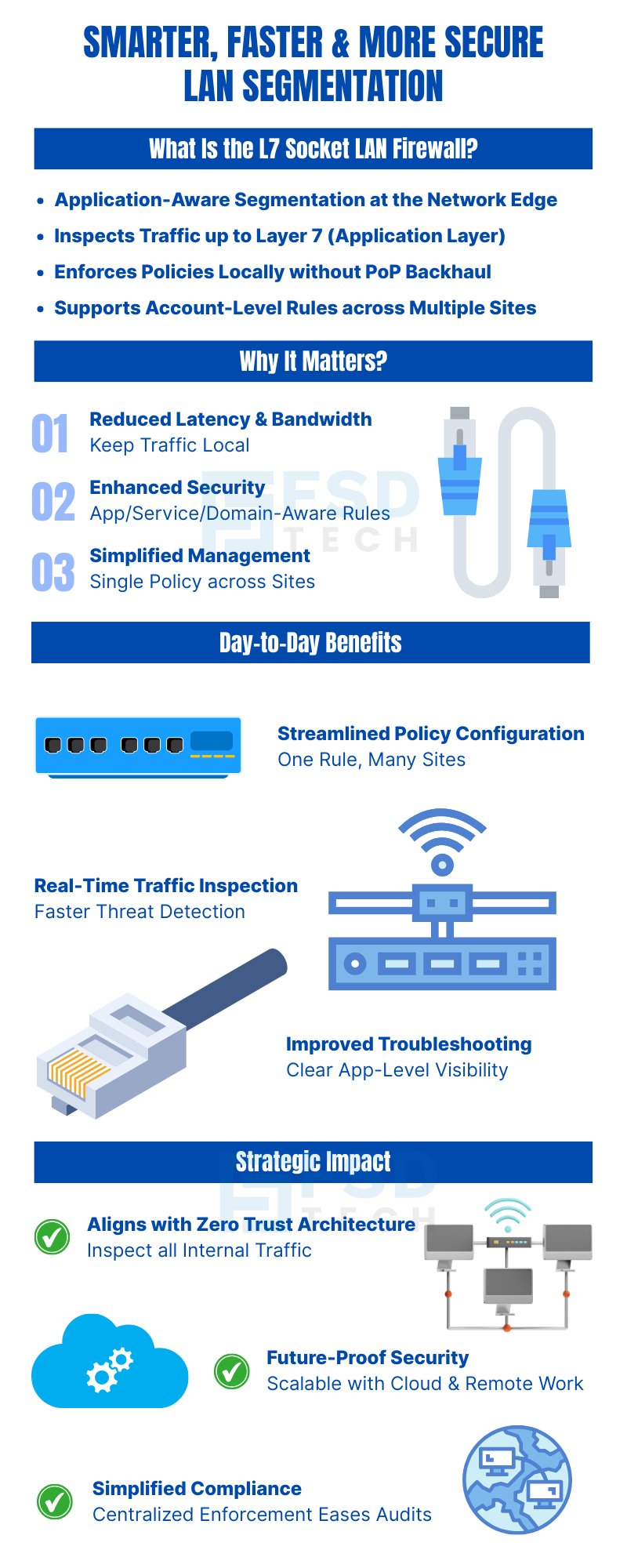
In today's enterprise networks, internal traffic—often referred to as east-west traffic—has become a primary vector for lateral movement by cyber adversaries. Traditional LAN segmentation methods, while effective, often route this traffic through centralized cloud points of presence (PoPs), introducing unnecessary latency and consuming bandwidth. Cato's new Layer 7 Socket LAN Firewall addresses these challenges by enabling intelligent, application-aware segmentation directly at the network edge, without the need to backhaul traffic to the cloud.
The Socket LAN Firewall is an enhancement to the Local Routing policy, allowing organizations to define and enforce security policies for internal traffic at the Socket level. This means that traffic between devices within the same site can be inspected and controlled locally, reducing the need to send this traffic over the last mile to the PoP.
With the introduction of Layer 7 (L7) enforcement, the firewall can now inspect traffic up to the application layer. This enables more granular control based on applications, services, and domains, rather than relying solely on IP addresses and ports.
Key features include:
By keeping internal traffic local, the Layer 7 Socket LAN Firewall minimizes the need to backhaul traffic to the PoP. This not only reduces latency but also offloads bandwidth from the cloud, leading to improved application performance and reduced operational costs.
Traditional firewalls often operate at Layers 2–4, inspecting traffic based on IP addresses and ports. The Layer 7 Socket LAN Firewall adds an application-aware layer of security, allowing organizations to enforce policies based on specific applications, services, and domains. This deeper inspection helps in identifying and mitigating threats that might bypass traditional firewalls.
Managing security policies across multiple sites can be complex and time-consuming. With account-level policies, administrators can define a single rule that applies across multiple sites, simplifying management and ensuring consistent security posture across the organization.
Instead of configuring individual rules for each site, administrators can define centralized policies that are automatically enforced across all sites. This reduces the administrative overhead and ensures consistency in policy enforcement.
With Layer 7 enforcement, administrators can inspect traffic in real-time, identifying and responding to threats more quickly. This proactive approach enhances the organization's ability to detect and mitigate potential security incidents.
By having a clear view of application-level traffic, administrators can more easily identify the source of issues and apply targeted fixes, reducing downtime and improving overall network reliability.
Ready to strengthen your LAN security? Fill out the form to get started.
An organization can configure the firewall to enforce the use of secure protocols like SMBv3 while blocking outdated and vulnerable versions like SMBv1. This ensures that internal communications remain secure and compliant with organizational standards.
Using custom applications as destinations, administrators can dynamically configure access to on-premise applications, ensuring that only authorized users and devices can connect, thereby reducing the risk of unauthorized access.
For environments with Internet of Things (IoT) and Operational Technology (OT) devices, the Layer 7 Socket LAN Firewall allows for precise segmentation, ensuring that these devices can operate securely without interfering with other parts of the network.
The Layer 7 Socket LAN Firewall supports the principles of Zero Trust by ensuring that all internal traffic is inspected and controlled, regardless of its origin. This approach minimizes the risk of lateral movement within the network.
As organizations continue to adopt cloud services and remote work solutions, the need for robust internal security becomes even more critical. The Layer 7 Socket LAN Firewall provides a scalable solution that adapts to evolving network architectures and security requirements.
With centralized policy enforcement and detailed traffic inspection, organizations can more easily demonstrate compliance with industry regulations and standards, reducing the complexity of audits and assessments.
The introduction of the Layer 7 Socket LAN Firewall represents a significant advancement in network security, offering organizations a more efficient, secure, and scalable solution for managing internal traffic. By combining application-aware inspection with centralized policy management, Cato empowers IT administrators to enforce robust security measures without compromising performance.
For organizations looking to enhance their security posture while simplifying management, the Layer 7 Socket LAN Firewall provides a compelling solution that meets the demands of modern network environments.
See how Cato’s Layer 7 Socket LAN Firewall works in action — book your Free Consultation today.
The Layer 7 Socket LAN Firewall is an advanced firewall enhancement that enables application-aware LAN segmentation at the network edge. It inspects east-west traffic up to the application layer, enforcing security policies locally without routing traffic through cloud PoPs.
Layer 7 LAN segmentation provides granular control based on applications, services, and domains instead of just IP addresses and ports. This prevents unauthorized lateral movement, enforces secure protocols, and strengthens zero trust network security.
Unlike traditional firewalls that operate at Layers 2–4, application-aware Layer 7 firewalls inspect traffic at the application level. This allows organizations to block vulnerable protocols, restrict access to on-premise apps, and enforce granular firewall policies that reduce risks.
By inspecting and controlling traffic locally, the Socket LAN Firewall eliminates the need to backhaul internal traffic to cloud PoPs. This reduces network latency, optimizes bandwidth usage, and improves application performance for enterprise users.
Yes. The firewall allows precise segmentation of IoT and OT devices at the LAN level. This ensures operational technology and connected devices are secured, isolated from critical assets, and prevented from introducing vulnerabilities into the network.
With account-level firewall policies, administrators can define one centralized rule that applies across multiple sites. This streamlines firewall policy automation, reduces manual configurations, and ensures consistent security across all branch locations.
The firewall enforces least-privilege access by inspecting all internal traffic, regardless of its origin. Every rule is purpose-driven, blocking unauthorized access and preventing lateral movement—key to a zero trust architecture.
Practical use cases include:
With Layer 7 real-time traffic inspection, admins can detect anomalies, resolve conflicts, and identify threats instantly. This improves incident response times, reduces downtime, and enhances overall enterprise network resilience.
Enterprises should adopt the Layer 7 Socket LAN Firewall to achieve:

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts