.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

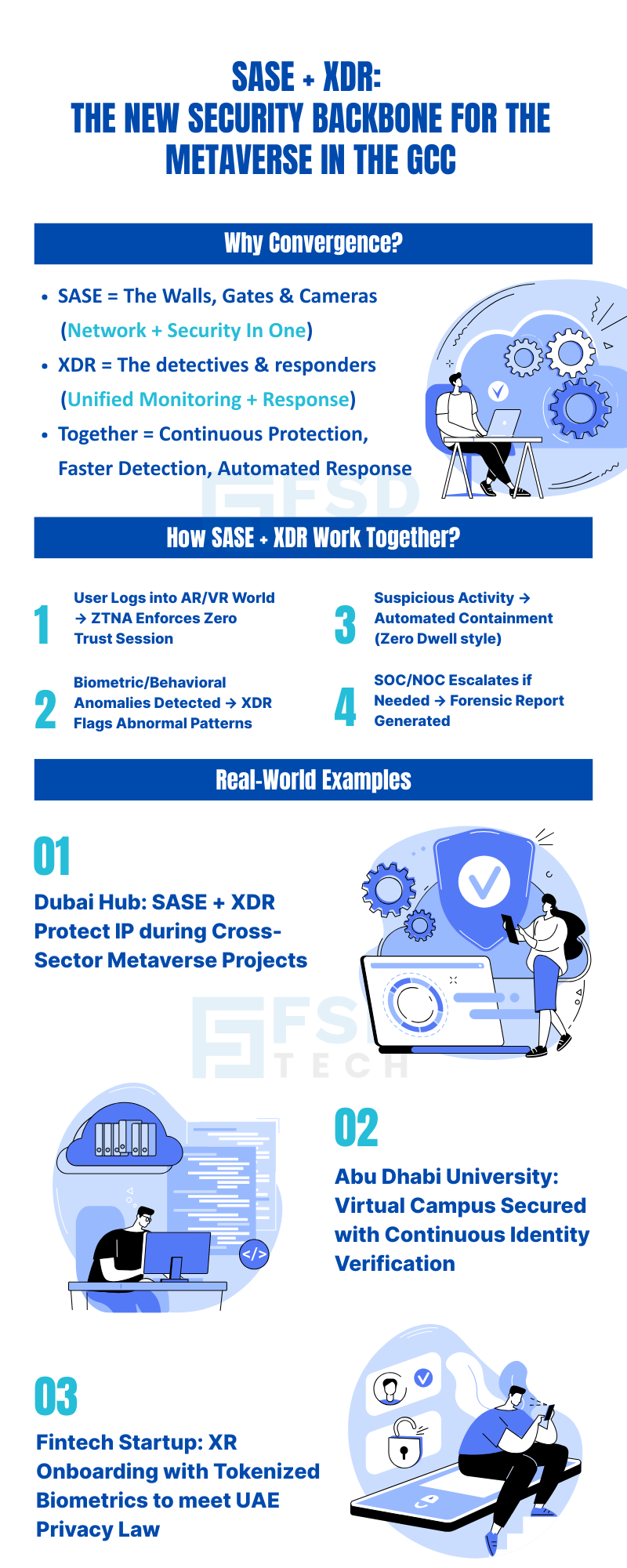
The Metaverse is rapidly reshaping digital transformation across the Gulf Cooperation Council (GCC). From Dubai’s innovation districts and Abu Dhabi’s smart city pilots to Riyadh’s digital twin initiatives, immersive AR/VR platforms and virtual worlds are moving from concept to operational reality. As GCC enterprises, ministries, and universities accelerate their Metaverse strategies, the security stakes have never been higher.
Identity-driven threats—such as deepfake impersonation, avatar spoofing, and session hijacking—are no longer theoretical. The exposure of sensitive biometric, behavioral, and spatial data, coupled with evolving regional regulations, demands a new approach to security. Traditional perimeter-based models are insufficient for these borderless, distributed environments.
Secure Access Service Edge (SASE) and Extended Detection and Response (XDR) are converging to deliver a unified, cloud-native security architecture—one that is purpose-built for the demands of the Metaverse. Cato SASE, enabled by FSD Tech’s regional expertise, provides Zero Trust, identity-based access, and real-time threat detection for immersive platforms. This convergence is not just a technical evolution; it is a strategic imperative for security leaders, architects, and digital transformation teams across the GCC.
Are deepfakes and avatar spoofing on your radar? Fill out the form to explore how FSD Tech can secure your Metaverse deployments today
Identity is foundational in the Metaverse. Unlike legacy IT environments, immersive platforms require continuous, context-aware authentication to prevent sophisticated threats such as deepfake impersonation and avatar spoofing. In virtual meetings, digital campuses, and smart city simulations, attackers can exploit weak identity controls to hijack sessions, exfiltrate data, or manipulate digital assets.
Cato SASE, as deployed by FSD Tech, addresses these challenges with:
These capabilities are critical for GCC-based organizations piloting Metaverse initiatives, where the integrity of digital identities underpins trust, compliance, and operational resilience.
The Metaverse generates and processes vast amounts of sensitive data, including:
This data is highly valuable—and highly regulated. With data privacy and e-identity laws rapidly evolving across the UAE and broader GCC, organizations face mounting pressure to secure immersive environments.
Cato SASE delivers:
FSD Tech works closely with GCC clients to implement these controls, aligning Metaverse deployments with both current and anticipated regulatory requirements.
Zero Trust is the new security baseline for the Metaverse. In immersive environments, where users, devices, and applications are highly dynamic, traditional perimeter defenses are obsolete. Cato’s native ZTNA model enforces:
FSD Tech’s expertise ensures that these controls are tailored to the unique needs of GCC enterprises, ministries, and educational institutions—enabling secure, scalable Metaverse adoption.
The convergence of SASE and XDR is a game-changer for threat detection and response in virtual worlds. Cato’s unified platform provides:
FSD Tech’s SOC/NOC services add a critical layer of operational resilience, enabling:
Ready to see SASE + XDR in action for your immersive environments? Click Here
Consider a digital innovation hub in Dubai, where startups, government agencies, and academic partners collaborate on Metaverse projects. FSD Tech deploys Cato SASE to:
This approach empowers innovation while maintaining robust security and compliance—critical for attracting investment and fostering cross-sector collaboration in the UAE.
In Abu Dhabi, a leading university launches a virtual campus, enabling students and faculty to interact in immersive 3D environments. Cato SASE provides the foundation for:
FSD Tech manages ongoing SOC/NOC operations, policy enforcement, and compliance reporting—allowing the university to scale its Metaverse initiatives without compromising security or user experience.
Similarly, GCC government agencies piloting digital twins of smart cities rely on Cato SASE and FSD Tech to:
An Abu Dhabi fintech startup integrates XR-based customer onboarding. Cato’s DLP and tokenization features protect sensitive biometric and financial data, ensuring compliance with UAE data privacy regulations. FSD Tech orchestrates the deployment, from access policy setup to ongoing monitoring and incident response.
Regulatory frameworks for data privacy, e-identity, and virtual assets are rapidly evolving across the GCC. Organizations must navigate a complex landscape that includes:
Cato SASE, enabled by FSD Tech, supports compliance through:
FSD Tech’s regional expertise ensures that deployments are aligned with both current and anticipated regulatory standards—reducing risk and accelerating time-to-value.
Auditability is essential for regulatory compliance and risk management. Cato SASE provides:
FSD Tech assists clients in configuring and maintaining these capabilities, ensuring that security leaders can respond confidently to regulatory inquiries and audits.
Performance is a critical success factor for Metaverse platforms. High latency or jitter can degrade user experience, disrupt collaboration, and undermine the value of immersive applications.
Cato’s globally distributed Points of Presence (PoPs) provide:
FSD Tech tunes PoP selection and last-mile connectivity for each deployment, ensuring that users across Dubai, Abu Dhabi, Riyadh, and beyond experience seamless, high-performance access to Metaverse environments.
User experience and security must go hand in hand. Cato SASE, with FSD Tech’s deployment expertise, delivers:
This approach empowers GCC enterprises and institutions to innovate confidently, knowing that security and user experience are never compromised.
The Metaverse is a dynamic, rapidly evolving ecosystem. Threat actors are constantly developing new tactics, while regulators introduce new requirements for privacy, identity, and digital assets.
Cato SASE and FSD Tech enable organizations to:
By building on a unified, cloud-native security platform, GCC organizations can future-proof their Metaverse investments—ensuring resilience, compliance, and operational excellence.
As the Metaverse matures, GCC-based enterprises, ministries, and universities will face new opportunities—and new risks. The convergence of SASE and XDR, enabled by Cato and FSD Tech, provides a robust foundation for:
By partnering with regional experts and leveraging best-in-class security architectures, organizations can unlock the full potential of immersive digital platforms—driving growth, collaboration, and leadership in the global digital economy.
Do you know if your Metaverse initiatives are regulation-ready? Book a Free consultation with FSD Tech’s experts. Schedule your session today.
Cato SASE enforces continuous, identity-based authentication and integrates with advanced verification technologies such as biometrics and self-sovereign identity (SSI). This approach detects and blocks impersonation attempts, including deepfakes and avatar spoofing, ensuring that only legitimate users can access Metaverse environments. FSD Tech customizes these controls for GCC deployments, aligning with local threat profiles and regulatory expectations.
FSD Tech acts as the regional systems integrator for Cato SASE, managing everything from initial identity validation and access policy setup to PoP latency optimization, SOC/NOC integration, and ongoing compliance management. Their expertise ensures that GCC enterprises, ministries, and educational institutions can deploy secure, scalable Metaverse platforms tailored to local requirements.
Cato SASE provides centralized policy enforcement, audit-ready reporting, and data protection tools that help organizations comply with evolving data privacy, e-identity, and virtual asset regulations in the region. FSD Tech ensures that deployments are aligned with current and anticipated regulatory standards, simplifying audits and reducing compliance risk.
Yes, Cato’s globally distributed Points of Presence (PoPs) and cloud-native architecture enable seamless, scalable protection and optimized connectivity for large-scale AR/VR and digital twin deployments. FSD Tech tunes each deployment for optimal performance across Dubai, Abu Dhabi, Riyadh, and other GCC locations.
Key threats include identity theft, deepfake-driven impersonation, DDoS attacks, malware injection, social engineering, and regulatory uncertainty. The convergence of SASE and XDR, as delivered by Cato and FSD Tech, provides unified protection against these evolving risks.
Cato SASE leverages data loss prevention (DLP), tokenization, and privacy-preserving AI techniques such as differential privacy and federated learning. These controls safeguard biometric, behavioral, and spatial data from unauthorized access or exposure, supporting compliance with GCC data privacy laws.
ZTNA is a security model that requires continuous authentication and least-privilege access for every user and device, for every session. In the Metaverse, where users and devices are highly dynamic, ZTNA prevents unauthorized access, lateral movement, and session hijacking—making it essential for immersive environments.
FSD Tech analyzes user distribution, application requirements, and network conditions to select the optimal Cato PoP locations and configure last-mile connectivity. This ensures low-latency, high-performance access for immersive applications across the GCC, enhancing user experience and operational efficiency.
Cato SASE captures comprehensive logs of all access, authentication, and data movement events. Automated compliance reporting tools generate detailed reports aligned with GCC regulatory frameworks, simplifying audits and demonstrating proactive risk management. FSD Tech assists clients in configuring and maintaining these capabilities.
Cato SASE supports differential privacy, homomorphic encryption, and federated learning. These techniques enable organizations to analyze biometric and behavioral data without exposing sensitive information, reducing privacy risks in AR/VR and digital twin environments.
Cato’s unified threat detection platform continuously monitors network traffic for signs of DDoS attacks. Automated mitigation workflows block malicious traffic at the edge, while FSD Tech’s SOC provides rapid response and escalation for large-scale or sophisticated attacks targeting Metaverse infrastructure.
Yes, Cato SASE is designed to integrate with SSI and blockchain-based identity solutions, enabling decentralized, interoperable identity management for Metaverse platforms. FSD Tech helps GCC organizations implement and operationalize these integrations to enhance trust and security.
Cato SASE provides scalable onboarding workflows, including biometric and behavioral verification, device posture assessment, and automated policy assignment. This enables rapid, secure provisioning of new users and devices, supporting the dynamic growth of Metaverse environments.
Cato SASE offers a unified, cloud-native security platform with global reach and advanced threat detection. FSD Tech brings deep regional expertise, handling everything from regulatory alignment to performance optimization. Together, they deliver practical, scalable, and compliant Metaverse security solutions for GCC enterprises, ministries, and universities.
By adopting a unified SASE and XDR architecture, organizations gain the flexibility to adapt to new threats, integrate emerging technologies, and respond to regulatory change. FSD Tech’s ongoing support ensures that security strategies remain aligned with business objectives and regional developments, enabling sustainable digital transformation in the GCC.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts