.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Most small and mid-sized business owners think cyberattacks are a problem for big corporations.
The truth?
In the last 2 years, over 60% of cyberattacks in GCC & Africa targeted SMBs.
Why?
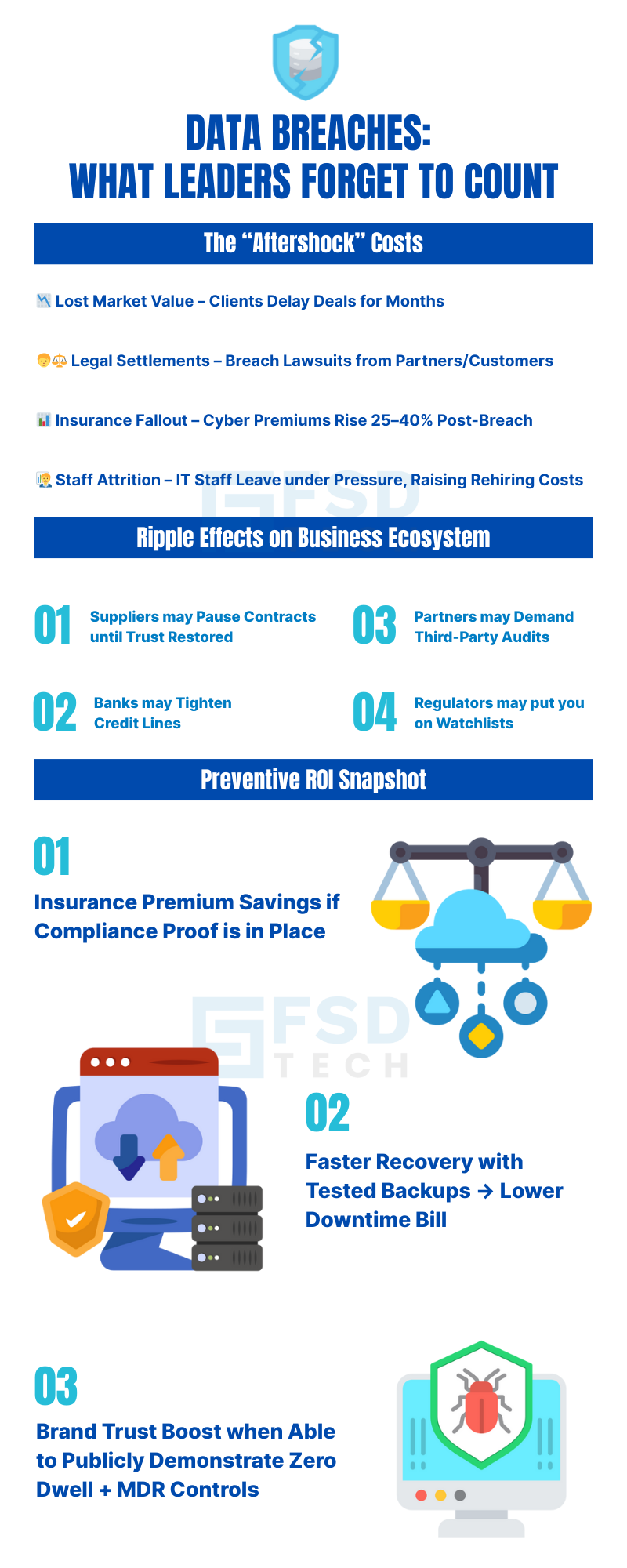
A single data breach can be the most expensive problem your business ever faces — not just in money, but in reputation, compliance penalties, and lost customer trust.
Direct losses from ransomware or stolen data can range from $50,000 to over $500,000 for SMBs in GCC & Africa.
This includes:
The average SMB takes 3–6 weeks to recover fully after a breach.
That’s weeks of:
If you operate in UAE, KSA, or parts of Africa, you must comply with data protection laws like UAE NESA, KSA NCA, South Africa POPIA, and Nigeria NDPR.
A breach could mean heavy fines for not protecting sensitive customer data.
Customers who hear about your breach might never trust you again.
Losing even 10% of your clients due to trust issues can devastate future revenue.
Hackers know these weaknesses — and exploit them.
Don’t let limited IT resources put your business at risk. Click Here
The most effective defense? A multi-layered security approach with EDR + MDR + Zero Dwell Containment.
Case Study – SME in Nairobi
A mid-sized law firm received an email with what looked like a client PDF.
Result: No breach, no downtime, no legal trouble.
Paying for EDR + MDR + Zero Dwell is far cheaper than paying for a breach.
Example:
It’s like paying a small monthly insurance fee instead of risking financial ruin.
With FSD-Tech, you get:
Ready to secure your SMB with enterprise-grade protection at SMB-friendly pricing? Click Here
Cyberattacks are no longer a “maybe” — they’re a “when”.
For SMBs in GCC & Africa, the cost of doing nothing is far higher than the cost of prevention.
With FSD-Tech’s EDR + MDR + Zero Dwell Containment, you can:
Want to know how much a breach could cost your SMB? Book a free 30-minute cyber health check with our experts. Schedule your session today.
A data breach happens when someone gets into your company’s systems without permission and steals or exposes your data. This could be customer information, business documents, financial records, or anything stored on your computers or servers.
Because hackers know SMBs often have weaker defenses, smaller IT teams, and no 24/7 monitoring. They see them as easier targets than large corporations.
In GCC & Africa, the cost can range from $50,000 to $500,000 or more. This includes ransom payments, downtime losses, IT recovery costs, and possible government fines.
Beyond direct money loss, there are:
No guarantee. Many businesses pay and still never get their data back. That’s why prevention is much safer than relying on ransom negotiations.
For most SMBs, full recovery takes 3–6 weeks. That’s weeks of lost productivity, missed sales, and damaged trust.
Use a multi-layered security approach:
EDR (Endpoint Detection & Response) watches all your devices for suspicious actions, stops dangerous behavior, and alerts you instantly.
MDR (Managed Detection & Response) adds a team of security experts who monitor your systems all day and night, investigate alerts, and respond to real threats immediately.
It’s technology that isolates every unknown file the moment it appears, checks it in a safe space, and blocks it if it’s dangerous — before it can cause damage.
These tools help you meet regional data protection laws like UAE NESA, KSA NCA, South Africa POPIA, and Nigeria NDPR by ensuring sensitive data is secured.
Yes. It protects laptops, desktops, and devices no matter where they are — in the office, at home, or on the move.
No. FSD-Tech offers SMB-friendly pricing. Protection often costs less than your monthly internet bill — and is far cheaper than a breach.
FSD-Tech can deploy it across all your devices in one business day, without disrupting your work.
We’re a local GCC & Africa partner offering:

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts