.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Site deployment is the backbone of any secure, global network strategy. In Cato’s SASE platform, setting up sites is a foundational task — whether you’re connecting a branch office, a cloud workload, or a virtual location within your data center. With the new CMA UI, site onboarding is not only streamlined but also built around deployment realities like bandwidth constraints, security posture, and failover readiness.
In this guide, we’ll break down how to set up different types of sites, clarify where to find each function in the CMA, and walk you through real-world tips that can save you hours of troubleshooting.
Log into the CMA, then go to:
Network > Sites > Add Site
From there, you can choose between: - Socket Site: For hardware-based site connections using a Cato Socket - vSocket Site: For virtualized environments using supported hypervisors - Cloud-Only Site: For connecting cloud-native environments without any appliance
Use a Socket site when deploying to: - Branch offices with stable WAN access - HQs needing high-throughput connections - Locations requiring dual-WAN redundancy
If your location has an existing router/firewall, place the Cato Socket in bridge mode to avoid NAT conflicts.
Use a vSocket for: - Data centers - Virtual labs and SDN test environments - Edge locations without space for physical hardware
Always validate time sync (NTP) in your hypervisor or vSocket may fail to authenticate with Cato.
Go Cloud-only if you need to connect: - SaaS environments like Microsoft 365 or Salesforce - Cloud-hosted apps in AWS, Azure, or GCP - Remote infrastructure you don’t control physically
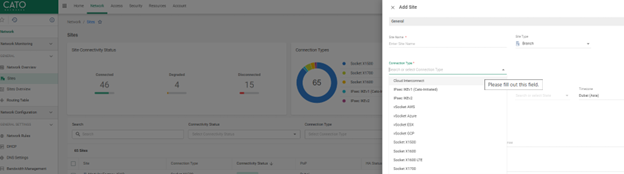
Use Cloud-only sites with Cato’s CASB and FWaaS capabilities for more granular security at the data layer.
Let’s walk through a hybrid deployment:
Within 30–60 minutes, the site should be production-ready.
After setup, go to Home > Experience Monitoring to confirm app performance and site latency. Schedule a bandwidth test or simulate failover using the Network > Tools suite to validate your deployment under real load conditions.
No. vSocket requires a virtual host. Use Cloud-only sites for SaaS or IPsec-based cloud apps.
No. You’ll need to delete and recreate the site with the correct type.
Cato auto-assigns based on latency, or you can override manually.
Yes. Under WAN settings, select manual configuration.
Yes. Configure dual Socket deployment for failover scenarios.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts