.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

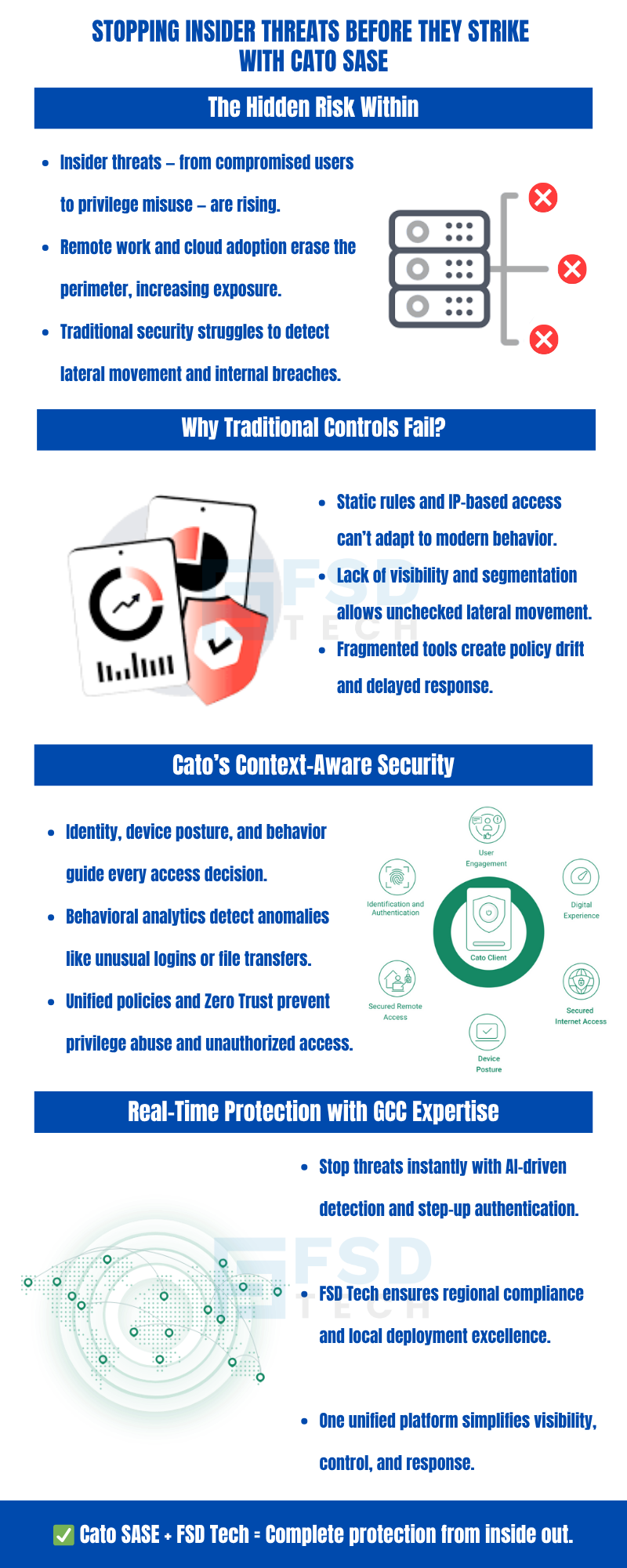
Insider threats—ranging from malicious employees to compromised credentials—are among the most persistent and costly risks for modern enterprises. Unlike external attackers, insiders already possess some level of legitimate access, making their actions harder to detect and stop. Privilege misuse, whether deliberate or accidental, can result in data breaches, operational disruption, and regulatory penalties.
The shift to cloud applications, remote work, and distributed teams has dissolved the traditional network perimeter. Attackers exploit this by leveraging stolen credentials or manipulating insiders to move laterally within the environment, escalate privileges, and access sensitive data. Traditional perimeter-based defenses are often blind to these activities once the attacker is inside.
These scenarios highlight why advanced, context-aware security is essential for detecting and stopping insider threats in real time.
Legacy security models focus on defending the network perimeter with firewalls, VPNs, and static access rules. However, as organizations adopt cloud services and hybrid work, the perimeter is no longer clearly defined. Users, devices, and applications operate across multiple locations, creating blind spots for traditional controls.
Static policies based on IP addresses or network segments cannot adapt to dynamic user behavior or device risk. Once an attacker—or a malicious insider—gains access, they often move freely within the environment, exploiting inconsistent controls and policy drift.
Lateral movement is a hallmark of advanced insider threats. After initial access, attackers probe for additional systems, escalate privileges, and seek out sensitive data. In environments without granular segmentation, real-time monitoring, or adaptive access controls, these activities can go undetected for weeks or months.
This is especially problematic in large, distributed enterprises or organizations with hybrid cloud deployments, where maintaining consistent security policies is challenging. The result: a single compromised account can lead to a full-scale breach.
Cato SASE fundamentally changes the approach to access control by leveraging identity, device posture, application context, and behavioral patterns for every access request. Instead of static rules, policies are dynamically enforced based on real-time risk assessment.
Key elements include:
This enables true zero trust —never trust, always verify—ensuring that elevated privileges are only granted under secure, verified conditions.
Cato SASE integrates advanced behavioral analytics to continuously monitor user and device activity. The platform establishes baselines for normal behavior and flags anomalies, such as:
When suspicious activity is detected, Cato SASE can automatically trigger step-up authentication, restrict access, or alert SOC teams for investigation. This proactive approach is essential for stopping insider threats before they escalate.
One of the most persistent challenges in enterprise security is maintaining consistent policy enforcement across on-premises, cloud, and remote environments. Cato SASE addresses this with a single, cloud-native platform that centralizes policy management and provides full visibility into all user, device, and application activity.
Security teams can:
This eliminates the risk of policy drift and misconfiguration, which are common vectors for insider threats and privilege abuse.
Consider a scenario in a GCC-based enterprise: a user’s credentials are compromised through a phishing attack. The attacker attempts to access sensitive financial records and download large files. Cato SASE’s behavioral analytics detect this deviation from normal activity, enforce step-up authentication, and block the download. SOC analysts are alerted in real time, enabling rapid investigation and containment—preventing data loss and regulatory exposure.
Many organizations struggle with fragmented security architectures, stitching together multiple products for access control, monitoring, and incident response. This complexity increases operational overhead and creates gaps that insiders can exploit.
Cato SASE delivers networking and security as a single, unified cloud-native service . SOC leads and IAM managers benefit from:
This unified approach enables security teams to focus on proactive threat detection and rapid response, rather than managing disparate tools.
Cato SASE’s cloud-native architecture supports continuous feature delivery and global threat intelligence updates . Security policies and analytics are updated in real time, without manual intervention or hardware refreshes.
This agility is especially valuable for organizations in the GCC and Middle East, where regulatory requirements and threat landscapes evolve rapidly. Enterprises can adapt their security posture to new risks—such as emerging insider threat tactics—without delay.
Enterprises in the GCC face unique regulatory, operational, and cultural challenges. As the regional enabler for Cato SASE, FSD Tech bridges global innovation with local execution by providing:
This partnership ensures that organizations in the UAE, Saudi Arabia, and across the GCC can leverage Cato SASE’s advanced capabilities while meeting stringent regional mandates.
A leading financial institution in the GCC needed to enable secure remote access for hundreds of employees during a rapid shift to hybrid work. Partnering with FSD Tech, the organization deployed Cato SASE, activating context-aware access controls and real-time behavioral analytics. The result:
This real-world example demonstrates how Cato SASE, enabled by FSD Tech, delivers measurable security and operational benefits for regional enterprises.
Secure Your Enterprise from Insider Threats. Talk to Our Cato SASE Experts Today.
An insider threat refers to risks posed by individuals within an organization—such as employees, contractors, or partners—who have legitimate access to systems and data. These threats are difficult to detect because insiders often operate within the bounds of their assigned privileges, making malicious or negligent actions blend in with normal activity. Traditional security tools focused on external threats may miss these subtle indicators.
Cato SASE uses context-aware access controls, behavioral analytics, and continuous monitoring to detect unusual access patterns, privilege misuse, and lateral movement. By analyzing user identity, device posture, and behavioral deviations, the platform can block threats before they escalate, alert SOC teams, and enforce adaptive policies in real time.
Unlike legacy solutions that rely on static perimeter defenses and fragmented point products, Cato SASE unifies networking and security in a single cloud-native platform. This enables consistent, adaptive policy enforcement and full visibility across all users, devices, and locations, reducing complexity and the risk of policy drift.
Cato SASE enforces granular, identity-driven access controls that adapt to user roles, device security posture, and behavioral context. Step-up authentication and real-time monitoring ensure that elevated privileges are only granted under secure, verified conditions, reducing the risk of accidental or malicious misuse.
Yes. Cato SASE uses micro-segmentation and behavioral analytics to detect and block lateral movement attempts. Independent testing has shown that the platform can block up to 100% of simulated lateral movement and privilege escalation attacks, dramatically reducing the risk of internal breaches.
Behavioral analytics establish baselines for normal user and device activity, then flag anomalies such as unusual login times, large file transfers, or access to sensitive resources outside typical patterns. This allows Cato SASE to detect and respond to insider threats that would bypass traditional rule-based controls.
FSD Tech is the regional enabler for Cato SASE in the GCC, providing tailored deployment, compliance alignment, and ongoing support. Their expertise ensures that enterprises in the UAE, Saudi Arabia, and neighboring countries can leverage Cato’s global innovation while meeting local regulatory and operational requirements.
Cato SASE’s centralized policy management and full visibility make it easier to enforce compliance controls and generate audit-ready reports. FSD Tech further assists by aligning deployments with GCC-specific regulations, including data residency and privacy mandates.
Absolutely. Cato SASE is designed for distributed environments, enabling secure, context-aware access for users regardless of location. The platform ensures consistent policy enforcement and risk-based controls for both on-site and remote employees.
Deployment timelines vary by organization size and complexity, but FSD Tech’s regional expertise enables rapid rollout—often within weeks. Their tailored approach ensures minimal disruption and alignment with local compliance requirements.
By consolidating networking and security into a single platform, Cato SASE provides SOC teams with unified visibility, real-time alerts, and streamlined workflows. This reduces response times and enables faster containment of insider threats.
A unified SASE platform like Cato eliminates the need for multiple point solutions, reducing operational overhead, simplifying policy management, and minimizing integration challenges. This leads to improved security outcomes and lower total cost of ownership.
Yes. Cato SASE supports integration with leading IAM solutions, enabling organizations to leverage existing identity infrastructure while enhancing security with context-aware, adaptive controls.
Cato SASE’s cloud-native architecture enables continuous feature delivery and global threat intelligence updates. The platform adapts to new attack techniques and regulatory changes, ensuring organizations remain resilient against emerging risks.
Enterprises with distributed workforces, hybrid cloud environments, or stringent compliance requirements—such as financial institutions, government agencies, and large enterprises in the GCC—benefit significantly from Cato SASE’s unified, context-aware security delivered by FSD Tech.
Organizations can work with FSD Tech to conduct a readiness assessment, evaluating current access controls, behavioral monitoring, and policy enforcement. Cato SASE’s unified platform provides actionable insights and rapid remediation of identified gaps, strengthening the overall security posture.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts