.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

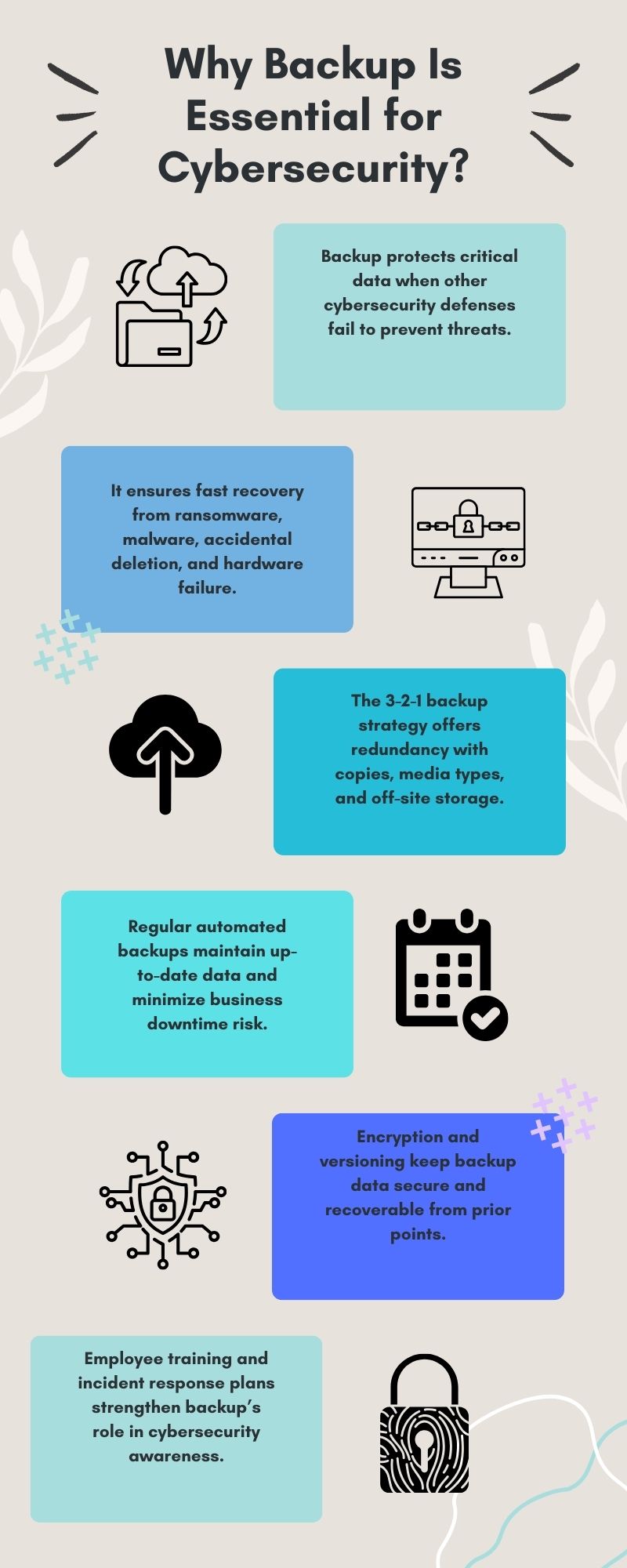
Always remember, in the digital world, losing your data is not just a problem; it is a major business disaster. Today, more than ever, cybersecurity needs a solid safety net. This is why backup is essential for cybersecurity. It is the first line of defense when everything else fails.
With ransomware attacks growing bigger and accidental file deletions happening daily, losing important information is a real risk. A trustworthy backup solution acts as your safety net. It makes sure you can get your critical data back fast and safely.
Take a read of this to find out why backup is a cornerstone for protecting your digital assets. You will also get to know about the best ways to set up a robust backup plan to guard against modern threats.
Data backup refers to making exact copies of your important files and storing them in a secure place away from your main computer or server.
Data backup can be understood as: creating a spare copy of all your digital things—documents, photos, emails, address books, videos, and system files. It explains the purpose of ensuring that this data can be retrieved quickly and safely in the event of an issue with the original.
To understand data backup in clearer terms, it’s about making sure your business operations do not stop because of a lost file.
A strong backup strategy can be the main difference between a small issue and a major, costly loss of data.
So, how do you make sure you have the right copies in the right places?
Get Started with Vembu Backup!
You likely use firewalls, antivirus software, and access controls as part of your cybersecurity plan. These tools focus mainly on prevention—stopping threats before they enter your system.
On the other hand, backup is different. It acts as a crucial recovery layer. It protects your data even when your prevention methods fail.
When a cyberattack happens and sensitive information is compromised, or your systems crash, backup provides the ultimate safety net. It allows your organization to restore operations with minimal disturbance, saving you time and money.
It is to be noted that without a good backup, you are fully exposed to losing your business data forever.
Also Read: What Is Vembu? A Deep Dive Into the All in One Backup & Disaster Recovery Platform
Why is backup so important today? Because the threats are real and constant. Several categories of threats exist that make a reliable backup solution non-negotiable:
Experts agree on a gold standard for making sure your data is always safe. It is called the 3-2-1 backup strategy. This simple rule greatly increases the chance that your data will be recoverable, even if one backup method fails.
To understand the strategy in clearer terms, here are the three parts:
By using this strategy, you build a layered defense for your digital assets.
Backup is about more than just getting your files back. It is about cyber resilience—the ability of your organization to quickly bounce back from an incident. Organizations that invest in a solid backup plan can respond to issues faster, cut down on downtime, and ensure business continuity.
A strong strategy includes specific key features:
Also Read: Who Uses Vembu? Real-World Use Cases for SMBs, MSPs & IT Teams
Cybersecurity awareness is an ongoing need for every company. Employees must understand that backup is not just an "IT thing." It is a shared responsibility that protects the entire business.
Implementing a robust backup strategy involves more than just buying software. It requires a thoughtful approach.
Backup is essential for business continuity planning. In the event of a cyberattack, system failure, or a physical disaster, a good backup ensures your operations can resume quickly.
This keeps your financial losses low, protects your customer trust, and maintains your organization’s strong reputation.
Here at FSD Tech, we know that great data protection is critical for your success. We offer Vembu Backup as a powerful, flexible solution for businesses and individuals seeking complete and easy-to-manage data protection.
Vembu Backup uses cutting-edge technology to give you automated, real-time backups across all your different platforms. This ensures your data is always up-to-date and ready for recovery.
With strong AES-256 encryption, flexible cloud integration, and full support for the 3-2-1 backup rule, Vembu helps your organization meet modern cybersecurity needs and maintain full business continuity.
By choosing Vembu Backup through FSD Tech, you get a scalable, secure, and reliable backup solution. This choice simplifies your data protection efforts and keeps your critical information safe from cyber threats, device failures, and accidental loss. You should take a read of the following features to see why Vembu stands out.
Vembu’s BDRSuite and BDRCloud bring complete, flexible, and affordable data protection for every environment you can imagine. Let's look at what makes them shine and stand out from the crowd.
Protect everything you rely on: virtual machines (VMware, Hyper-V), physical servers, endpoints (laptops/desktops), SaaS applications (Google Workspace), databases, and cloud VMs (Azure, AWS). It is to be noted that Vembu supports your entire modern IT environment.
You have complete control over where your data lives. Keep it on-premise (local), in the cloud, or use a flexible mix of both. Storage options include AWS, Azure, Google Cloud, Wasabi, or any storage target that is S3-compatible.
Manage all your backups from one simple dashboard. This helps simplify monitoring, reporting, and control across all your different environments. You can pick between the BDRCloud-hosted or the BDRSuite self-hosted console for full flexibility.
Recover from data loss in minutes, not hours or days. Built-in ransomware detection, encryption, and data immutability secure your backups end-to-end. This power helps keep your business running even when disaster strikes.
So, what exactly makes Vembu different from other backup vendors?
You do not need to juggle multiple, separate tools. You manage all your workloads—virtual, physical, SaaS, and cloud—under one unified solution.
You get enterprise-grade security and performance that is available at SMB-friendly prices. Importantly, there are no hidden charges.
From small startups to large enterprises, Vembu scales easily to match your exact data protection needs today and as you grow tomorrow.
Every feature is built around ease of use, speed, and complete control. Therefore, you spend less time managing backups and more time working to grow your business.
When your business's uptime is most important, Vembu delivers peace of mind with proven, trusted backup solutions that are built for today’s complex hybrid IT world.
So, to conclude, a solid backup is not optional; it is a must-have part of any serious cybersecurity strategy. It acts as the key recovery layer, protecting your critical data against every kind of threat, from ransomware and malware to simple accidental loss and hardware failure.
By investing in strong backup solutions, your organization can quickly improve its cyber resilience, ensure business continuity, and maintain the trust you have built with your customers.
As cyber threats continue to change and become more complex, backup remains an essential part of effective cybersecurity, providing both peace of mind and operational stability in this unpredictable digital world.
When the stakes are high, you need the right partner.
Ready to secure your business's future?
Contact FSD Tech today to implement Vembu Backup.
Vembu Backup supports a wide and comprehensive range of data. This includes files, folders, system state, registry settings, virtual machines (VMs), and application servers such as Exchange, SQL, and SharePoint. Furthermore, it offers robust backup for cloud instances like AWS and Azure VMs.
You can schedule backups as frequently as your business requires—hourly, daily, or weekly. This flexibility ensures your data is always up-to-date and protected against sudden loss.
Yes, your data is highly secure. Vembu Backup utilizes strong AES-256 encryption to protect your data both in transit and at rest. This ensures that your sensitive information remains protected, meeting all modern security standards.
Vembu Backup offers flexible and fast restore options. This includes instant boot recovery for virtual machines and file-level recovery for individual files or folders. These features make data restoration both fast and efficient, minimizing your downtime.
Yes, it fully supports the 3-2-1 backup strategy. Vembu Backup allows you to store backups in multiple locations, including public cloud storage and private off-site repositories, for maximum protection against localized disasters.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!

🕓 November 24, 2025

🕓 September 16, 2025

🕓 September 5, 2025
share your thoughts