
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Imagine this:
You own a growing retail chain in Dubai.
It’s Monday morning, and your team is busy processing weekend orders.
Your accountant gets an email from what looks like your bank:
“Important: Security Alert on Your Account. Please click here to verify.”
The logo looks right.
The tone feels urgent.
Without thinking too much, your accountant clicks the link.
Within seconds, a malicious file downloads.
It doesn’t scream “virus.” It hides. It starts collecting sensitive login information.
And just like that, your company’s data is at risk — all because of one click.
Cybercriminals know that hacking into a secure system is hard.
It’s easier to trick people into opening the door for them.
The most common tricks?
According to recent data, over 90% of cyberattacks start with a human error.
In GCC & Africa, small and mid-sized businesses are especially at risk because:
1. They use logos and branding — copying from real companies.
2. They spoof sender addresses so emails look like they come from a trusted contact.
3. They create urgency — “Pay now,” “Verify account,” “Security alert.”
4. They use local references — GCC banks, African suppliers, familiar business names.
Here’s what can happen after just one click:
Don’t let one click put your business at risk. Fill out the form to explore Zero Dwell + EDR + MDR protection for your SMB today
Even if an employee clicks a bad link or downloads a suspicious file, Zero Dwell isolates the file instantly.
It checks it in a secure container so it can’t run and cause harm.
Monitors all devices in real time.
If anything suspicious happens — like files encrypting or strange data transfers — EDR stops it and alerts you.
Your 24/7 human security team.
They review alerts, investigate threats, and take immediate action — even at midnight.
Ready to protect your team from phishing and ransomware? Click Here
Case Study – Abu Dhabi Trading Company
An employee received a fake supplier invoice in PDF format.
Outcome: No breach. No ransom. No disruption to business.
Yes, staff awareness training is important — but even the best-trained employee can make a mistake.
That’s why technical safety nets like Zero Dwell, EDR, and MDR are essential.
Think of it like driving:
With Protection:
Without Protection:
We offer:
Compliance with UAE NESA, KSA NCA, POPIA, NDPR.
Your employees are your greatest asset — but also your biggest security risk.
With FSD-Tech’s 3-layer cybersecurity, one mistake won’t cost you your business.
Want to see how FSD-Tech can protect your employees in less than 24 hours? Book a free consultation with our cybersecurity experts. Schedule your session today.
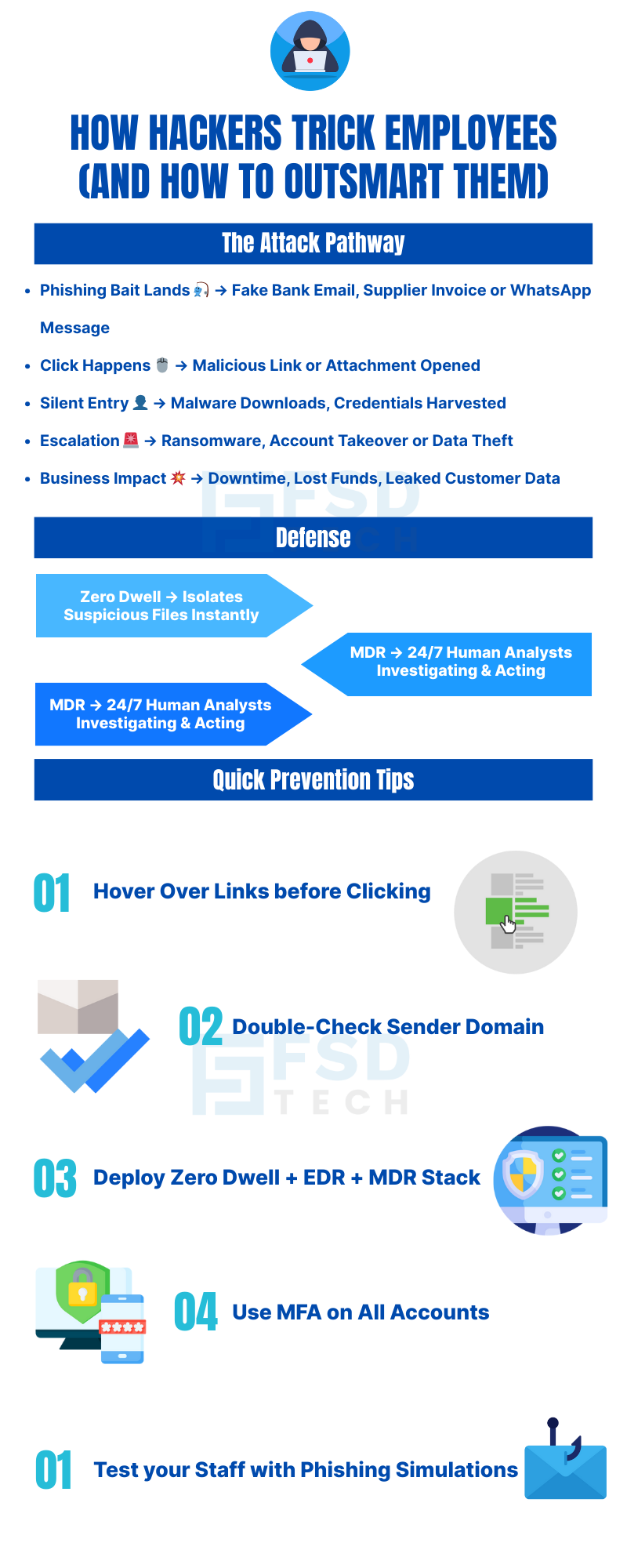
Phishing is when a hacker sends fake emails, messages, or links that look real to trick someone into sharing passwords, bank details, or clicking harmful files. These fake messages can look like they’re from your bank, supplier, or even a colleague.
Because people are easier to fool than machines. Hacking into a secure server takes skill and time, but tricking an employee to click a link or open a file can take just a few seconds.
It often uses:
A single click can download malware, steal passwords, or start ransomware encryption. Once inside, hackers can spread to other devices and servers quickly.
Yes. Smaller businesses often lack big IT teams, have fewer security tools, and may not train staff regularly, making them easier targets for cybercriminals.
No. Training reduces mistakes, but no one is perfect. That’s why technical tools like Zero Dwell Containment, EDR, and MDR are necessary as a safety net.
It instantly isolates suspicious files before they run. If the file is safe, it’s released. If it’s dangerous, it’s blocked. This stops threats before they can cause harm — even if an employee clicks on them.
EDR watches all endpoint activity in real time. If an employee accidentally opens a malicious file, EDR detects unusual behavior and stops it before it spreads.
MDR adds a 24/7 human team to review alerts, investigate threats, and respond instantly — even outside business hours. This means threats don’t wait until Monday morning to be handled.
Yes. Zero Dwell, EDR, and MDR work anywhere — in the office, at home, or while traveling. This is especially important for hybrid and remote teams.
Fake invoice or payment requests are common. Hackers send emails pretending to be suppliers or clients, asking for urgent payment or account verification.
We can deploy protection across all your devices in as little as one business day — without stopping your operations.
No. For SMBs, pricing can be as low as $2–$5 per device/month — far cheaper than the $50,000+ cost of recovering from a breach.
By preventing data leaks, these tools help you comply with regional laws like UAE NESA, KSA NCA, POPIA, and NDPR, avoiding fines and legal issues.
We’re a trusted GCC & Africa solutions partner, providing Xcitium’s award-winning EDR, 24/7 MDR SOC teams, and Zero Dwell Containment — all tailored for SMB budgets.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts