
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Securing users, apps, and devices at scale begins with the right policy enforcement strategy. With Cato’s converged platform, firewall rules, threat prevention, and advanced security layers like IPS and anti-malware are all unified within a single policy engine. This eliminates fragmented security stacks and makes real-time policy enforcement intuitive for IT teams.
Cato’s cloud-native architecture allows these policies to be managed centrally via the Cato Management Application (CMA), with enforcement executed at the nearest PoP, ensuring minimum latency and optimal performance. Whether managing hybrid networks or protecting remote workers, Cato’s security policies are flexible, identity-aware, and integrated into the broader SASE framework.
In this blog, we’ll walk through how to configure, test, and monitor security policies using the new CMA UI, along with practical tips for applying Zero Trust principles and responding to real threats faster.
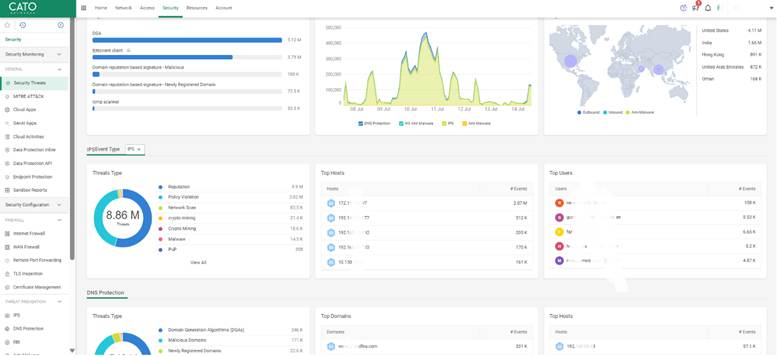
In the updated CMA interface: - Go to Security > Internet Firewall to manage outbound access control rules - Use Security > WAN Firewall for east-west traffic segmentation between sites, users, and VLANs - Configure advanced threat prevention under Security > Threat Protection > Profiles - Track and investigate incidents using Security > Threats and Security > Events - Configure inspection of encrypted traffic under Threat Protection > TLS Inspection
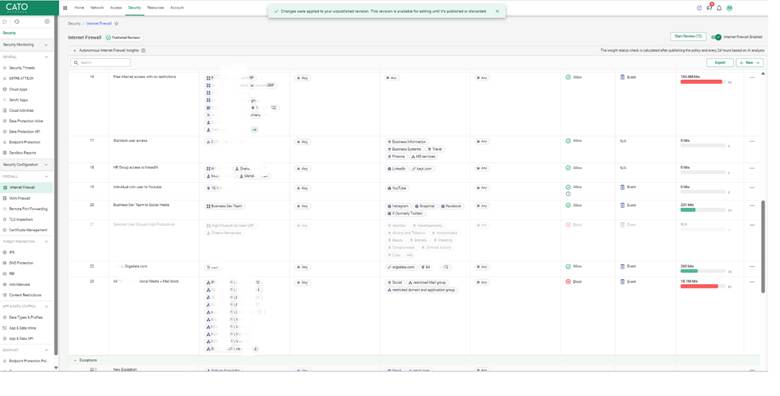
Use identity-based access to tailor policies for different roles: allow DevOps teams full Git access while limiting interns to core documentation sites only.
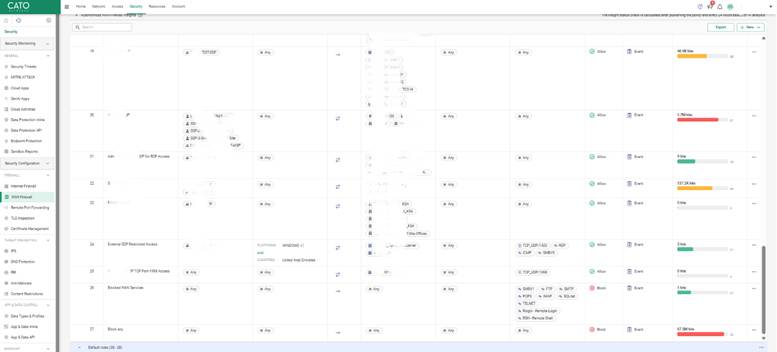
Augment WAN Firewall rules with posture-based ZTNA policies to enforce access only from healthy, compliant devices.
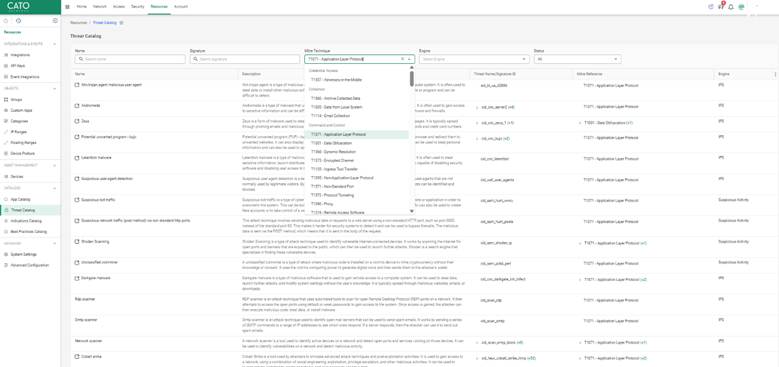
For finance and legal departments, apply Strict protection with full TLS inspection. For R&D and testing environments, use Custom to avoid false positives and performance concerns.
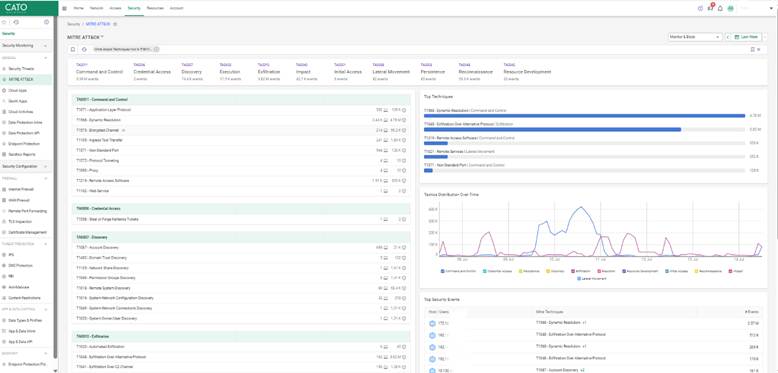
Export logs to external SIEM platforms using Syslog or REST API for extended analytics. Correlate user behavior with threat detection to identify insider threats early.
Contact Our Cato SASE Experts today
Yes. Use identity-based filtering integrated with AD or SAML IdPs.
The incident is logged in the Threats dashboard and the user is immediately disconnected from the malicious domain or flow.
Minimal. Inspection occurs at the nearest PoP using Cato’s optimized DPI engines.
Not directly, but Cato offers templates and migration assistance.
Yes. You can enable inspection selectively and apply exceptions for banking or health services.
Use the Network > Tools > Firewall Tester in CMA to validate rule behavior.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts