
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

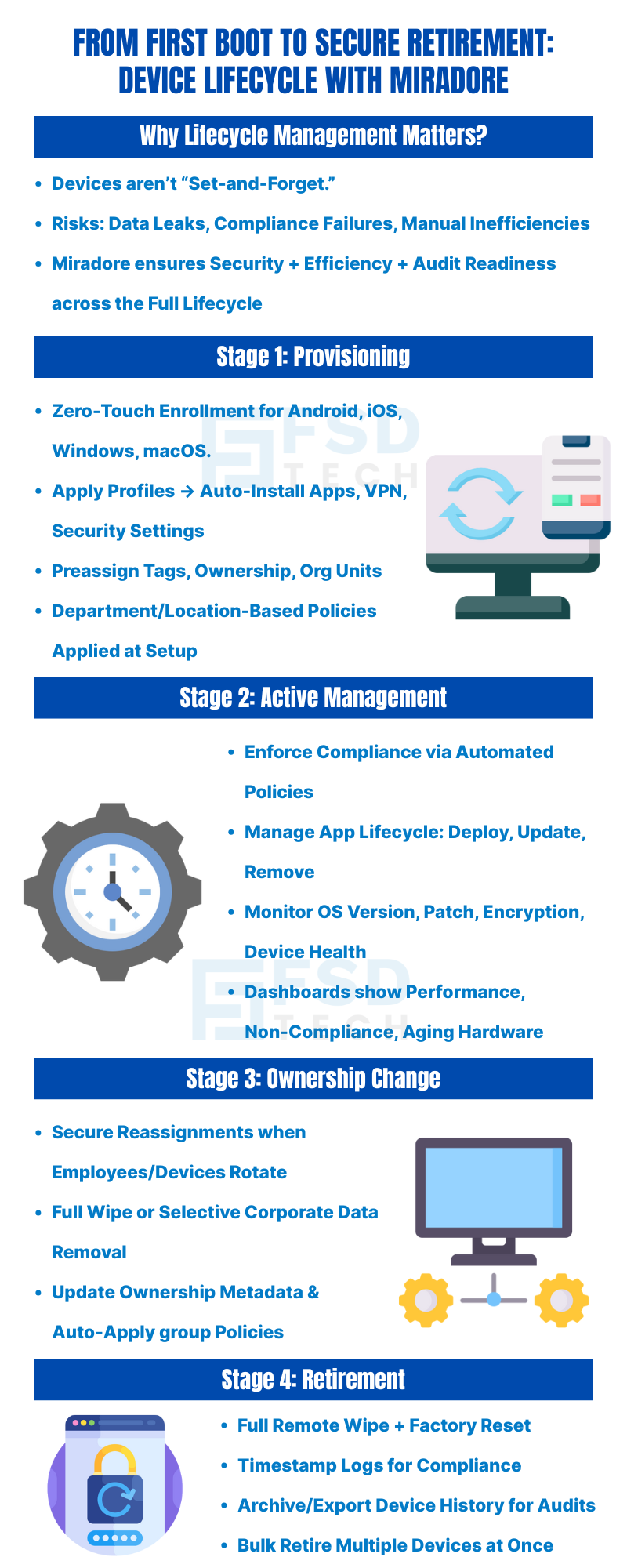
Enterprise mobility doesn't end once a device is enrolled. From provisioning new endpoints to retiring them securely, managing the complete lifecycle of devices is critical for data security, operational efficiency, and regulatory compliance.
Miradore provides a streamlined and policy-driven approach to endpoint lifecycle management (LCM) — covering every stage from onboarding to secure decommissioning. Whether you're managing hundreds of tablets for a retail chain or work-from-home laptops across business units, Miradore ensures visibility and control throughout the device journey.
Provisioning starts with onboarding devices efficiently and securely. Miradore supports zero-touch provisioning methods for Android (ZTE), iOS (DEP), Windows (Autopilot), and manual enrollment options.
You can:
This ensures every device is work-ready from first boot, without requiring hands-on setup by IT staff.
Once provisioned, devices enter the operational phase. Miradore provides centralized visibility and ongoing control through:
Device lifecycle dashboards give you insights into:
Want to see how Miradore can simplify lifecycle management in your environment? Fill out the form and our team will send you tailored recommendations.
Devices often shift hands within organizations. Whether reassigning a laptop to a new employee or rotating tablets between teams, Miradore supports secure, structured transitions:
This eliminates residual data risks while speeding up redeployment.
Eventually, devices must be retired due to hardware failure, end-of-support, or corporate refresh cycles. Miradore ensures decommissioning happens securely:
This helps you meet compliance needs while securely removing devices from active inventory.
A distributed services company managing 400+ mobile and desktop devices across regions needed a way to onboard new employees, reassign laptops securely, and decommission expired devices in a compliant manner.
Using Miradore, they:
Next Steps
Device management doesn’t end at enrollment. With Miradore, you get full lifecycle coverage that minimizes manual effort, increases endpoint security, and keeps your IT environment audit-ready.
Manage devices from start to finish with confidence.
Ready to take control of your device lifecycle? Book a free consultation with our experts today and discover how Miradore can fit your IT strategy.
Yes. Miradore supports zero-touch enrollment for major platforms, and you can automate provisioning using profiles, tags, and group-based policies.
IT admins can remotely wipe corporate data, reset ownership, and reassign profiles to support smooth handovers without re-enrollment.
You can retire it through Miradore by performing a secure wipe, logging the retirement, and archiving its management history.
Yes. Miradore maintains detailed logs of provisioning, policy changes, wipe events, and user assignments, all exportable for audits.
No. Most processes—from provisioning to compliance enforcement—are automated via dynamic rules, schedules, and group-based actions.
All actions (wipes, policy pushes, admin activity) are logged, timestamped, and linked to users/devices for full traceability in audits.
Yes. Devices can be selected by group, tag, or filter and retired in bulk with secure wipe and audit logging.
Yes. Miradore provides consistent lifecycle management capabilities across Android, iOS, Windows, and macOS endpoints.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts