
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025
.jpg&w=3840&q=75)
In 2023, a small healthcare provider in Abu Dhabi became the target of a cyberattack.
Hackers managed to break into the company’s network and steal copies of their backup files from a connected server.
At first, it seemed like the company was facing disaster:
But when the hackers tried to open the files, all they saw was unreadable gibberish.
Why? Because the backups were encrypted.
Without the secret key to decrypt them, the data was useless to the attackers.
This one layer of protection saved the business from financial ruin and public embarrassment.
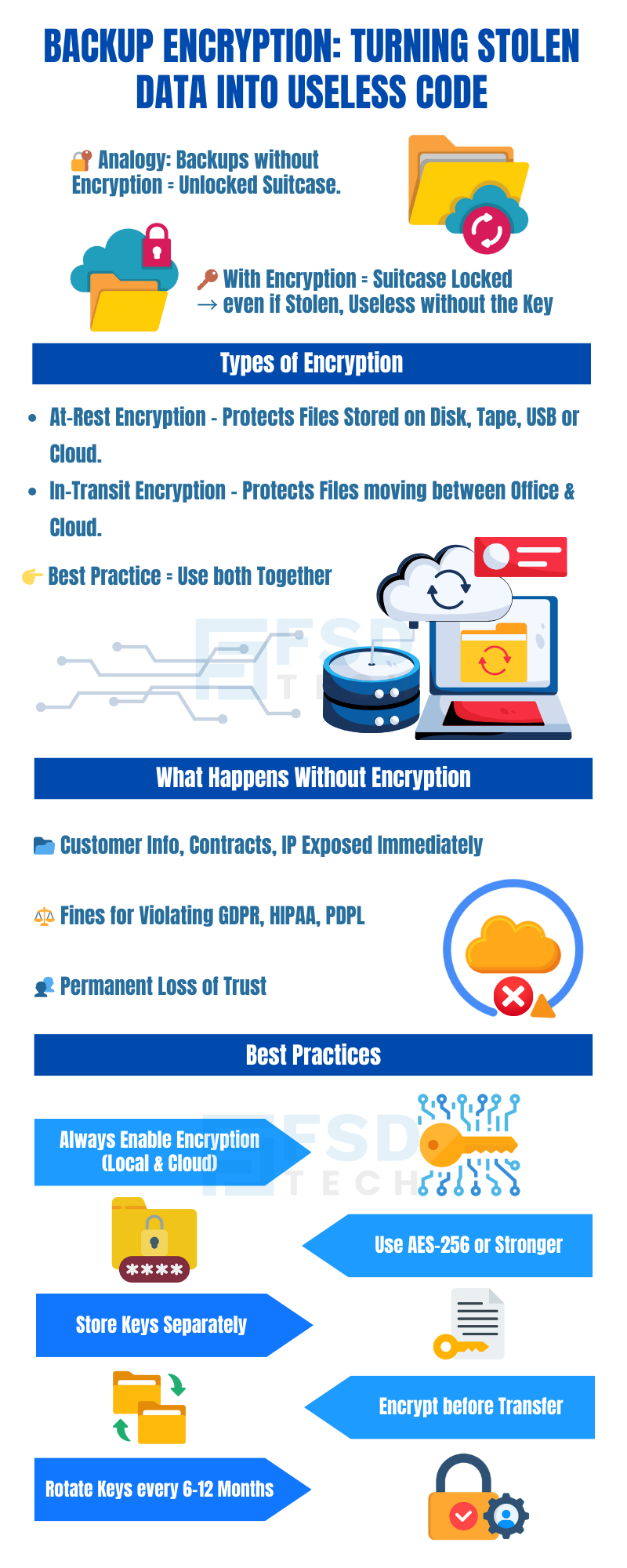
Backup encryption is the process of scrambling your backup data so no one can read it unless they have the correct password or decryption key.
It works much like locking your valuables in a safe:
Not sure if your backups are really secure? Get a free backup security checklist today
The best protection comes from using both types together.
If backups aren’t encrypted, you’re essentially leaving your data in an unlocked box.
If that box is stolen — whether by a cybercriminal or through lost equipment — the thief can immediately read everything.
This can lead to:
A law firm in Doha stored its client case files in cloud backups protected by Vembu’s AES-256 encryption.
When their cloud provider suffered a security breach, hackers managed to copy some backup files — but without the encryption keys, they couldn’t read a single document.
This protection saved the firm from potential lawsuits and kept their clients’ trust intact.
Creating backups is only half the job — securing them is the other half.
Without encryption, your backups are vulnerable.
With encryption, even if someone steals them, they’re just holding a pile of unreadable code.
Is your backup data truly safe from hackers? With Vembu BDR Suite, encryption is built-in from start to finish, giving you peace of mind that your backups can’t be read without your key. Book your free security review today
Backup encryption is a way of locking your backup data so that no one can read it unless they have the special password or “key” to unlock it.
When you encrypt your backup, the files are turned into unreadable code. Even if someone steals them, they won’t be able to see anything useful without the key.
Think of it like storing important documents in a safe — without the combination, it’s just a heavy box full of useless paper to a thief.
Your backups often hold the most important and sensitive information in your business, such as:
If someone got access to your backups without encryption, they could open and read all of this instantly.
With encryption, even if your backup is stolen, it’s just scrambled data without the decryption key.
Encryption uses a mathematical formula to scramble your readable data into unreadable code.
When you need the files back, the encryption key reverses the process, turning the scrambled code into readable information again.
Without that exact key, it’s nearly impossible to make sense of the scrambled data.
For complete safety, you need both: protection during storage and during transfer.
Without encryption, backups are just like files on a regular computer — anyone who gets them can open and read them.
If they’re stolen through hacking or physical theft, the thief could see:
Confidential contracts.
Internal plans and strategies.
This could lead to fines, lawsuits, and permanent damage to your company’s reputation.
AES-256 is one of the strongest encryption methods available today.
It’s used by banks, governments, and the military to protect sensitive information.
The “256” refers to the key length — longer keys are much harder to break.
Only someone with the exact encryption key or password can decrypt the backups.
Without it, even the most advanced hacker would find it nearly impossible to read the files.
Keep them separate from the backups and in a very secure place.
Best options include:
If you lose your encryption key, you won’t be able to restore your data — so store it safely.
Encryption does require some processing power, so it might add a few seconds or minutes to the backup process.
However, with modern systems like Vembu BDR Suite, the slowdown is minimal and the security benefit is huge.
Encryption doesn’t stop ransomware from infecting your live systems, but it protects your backups if attackers try to steal them.
Even if ransomware operators take your backups, they won’t be able to read them without the key.
In many industries — including healthcare, finance, and government contracting — yes.
Regulations like HIPAA, GDPR, and various ISO standards require businesses to encrypt their backups to protect sensitive data.
If you encrypt your backups before sending them to the cloud, your cloud provider cannot read them.
They will only see scrambled data, which is useless without your key.
You should encrypt all backups — both local and cloud.
Physical theft is just as real a threat as hacking.
For example, if someone steals a hard drive or tape from your office, encryption keeps it safe.
Changing your keys periodically (every 6–12 months) adds an extra layer of security.
This is called key rotation and is a good practice for long-term data protection.
Vembu BDR Suite offers:
Backup encryption is the process of securing business data using advanced encryption algorithms (like AES-256). This ensures that even if backups are stolen or accessed without permission, the data remains unreadable to unauthorized users.
SMBs in GCC and Africa face rising cyber threats, ransomware, and strict compliance requirements. Encrypted backups not only safeguard critical data but also help meet regional and global regulations such as GDPR and local data protection laws.
Vembu BDR Suite provides end-to-end protection by encrypting backups both in-transit and at rest with AES-256 encryption. This guarantees secure data across on-premises, cloud, and hybrid environments.
Yes. Encrypted backups play a vital role in ensuring compliance with data security regulations. They help SMBs avoid penalties and protect sensitive customer and business information.
If encrypted backups are stolen, the data is still safe. Without the encryption key, the stolen files remain unreadable, preventing breaches, reputational damage, and financial loss.

Nasmal is a Solution Architect & Business Analyst focused on AI, Data, Automation, BCP, and Process Optimization. He helps businesses evolve from reactive to proactive, data-driven, and resilient operations. With hands-on expertise, he simplifies complex tech into clear, easy-to-understand blogs.
Share it with friends!

🕓 November 24, 2025

🕓 September 16, 2025

🕓 September 5, 2025
share your thoughts