.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

In early 2024, a medium-sized manufacturing company in Riyadh faced a crisis.
On a Monday morning, their computer systems suddenly froze.
A message popped up on every employee’s screen:
“Your files have been encrypted. Pay $150,000 in cryptocurrency within 72 hours, or your data will be deleted forever.”
The hackers had done their homework. Before locking the files, they searched the company’s network and deleted every backup they could find.
But the attackers missed one thing: The company had a set of immutable backups stored in the cloud. These backups were locked in such a way that no one — not even the company’s own IT administrator — could delete or change them until the time period expired.
Within hours, the IT team restored every system from these untouchable backups. No ransom was paid.
Operations were back to normal by the next day.
This wasn’t luck — it was planning. And it’s why immutable backups are now considered one of the most important tools for data protection in 2025.
Don’t wait for ransomware to teach you a costly lesson. Secure your business with immutable backup protection today. Book Your Free Consultation
An immutable backup is a locked copy of your data that cannot be changed, overwritten, or deleted for a certain amount of time — not by hackers, not by employees, and not even by your IT team.
Think of it like keeping your most valuable documents in a vault with a timer. Once you close the vault and set the timer for, say, 30 days, no one can open it until that time is up — no matter how hard they try.
Immutable backups use a technology often called Write Once, Read Many (WORM).
This means:
Once the “lock period” you’ve chosen is over, you can delete or replace the backup if you wish — but until then, it’s completely safe.
Your data deserves a shield hackers can’t break. Get started with Vembu Immutable Backup now. Claim Free Data Protection Health Check
Myth 1: They’re too expensive for small businesses.
Reality: Cloud-based immutable storage is now affordable, with plans designed for SMB budgets.
Myth 2: They’re complicated to set up.
Reality: With solutions like Vembu BDR Suite, immutability can be turned on with just a few clicks.
Myth 3: I already have regular backups, so I don’t need immutability.
Reality: Regular backups can still be changed or deleted by ransomware or human error. Without immutability, your “safe copy” might not be so safe.
Vembu BDR Suite makes immutability simple and practical for all business sizes:
Real-World Example
A medical clinic in Nairobi stored all patient records on a central server.
When ransomware hit, it destroyed all the local backups.
But their immutable backups stored in Vembu’s cloud were untouched.
They restored the entire system in under 3 hours, avoided paying the ransom, and prevented a legal disaster under healthcare privacy laws.
The Key Takeaway
Immutable backups are like an insurance policy that can’t be canceled.
In today’s world of ransomware, human mistakes, and insider risks, they’re no longer a “nice-to-have” — they’re a must-have for business survival.
Tomorrow’s Topic – We’ll explore “The 3-2-1 Backup Strategy: Still Relevant in 2025?” and how to adapt it to modern threats.
If your backups can be deleted or changed, you’re one step away from disaster.
Ready to lock down your backups and stay ransomware-proof? Schedule a Free Strategy Call with Our Experts
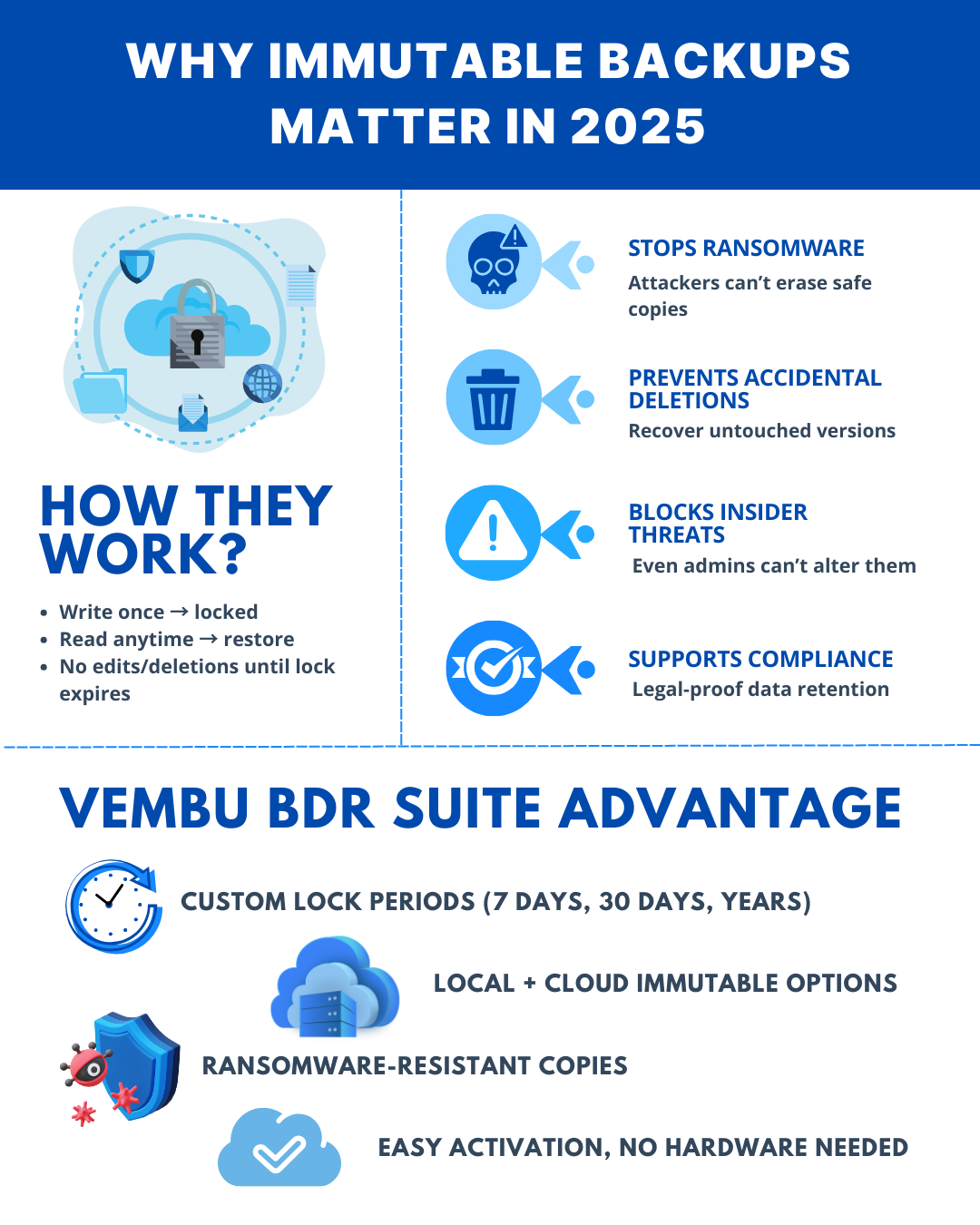
An immutable backup is a special kind of backup that is completely locked for a certain period of time.
Once the backup is created, no one — not even the system administrator or the person who set it up — can delete, edit, or change it until the lock time runs out.
Think of it as putting your most important files in a safe with a timer. You can open the safe to read the files whenever you want, but you can’t remove or change them until the timer finishes.
A regular backup is like a regular filing cabinet — you can open it any time and add, change, or remove files. That means if something goes wrong — like a hacker attack or a mistaken deletion — the backup can also be destroyed or altered.
An immutable backup is like a filing cabinet that locks itself and refuses to open for editing until a set date. It’s much harder (often impossible) for hackers, viruses, or even accidental clicks to damage it.
In the past, backups were enough to recover from most problems. But now, cybercriminals have gotten smarter.
Modern ransomware often attacks backups first so that you can’t restore your data without paying them.
Immutable backups make that impossible — even if hackers get into your systems, they can’t touch these protected copies.
Let’s say ransomware attacks your main computer systems and also tries to delete your backups. If your backups are immutable, the ransomware will fail because the system simply will not allow changes or deletion until the lock period is over.
You can then restore your files from these untouched backups without paying the ransom.
Yes. Sometimes people delete the wrong folder or overwrite an important document by accident. If your backup is immutable, you can go back to the original, unchanged version and recover it easily — even if the mistake was made weeks ago.
Yes. Unfortunately, not all risks come from outsiders. If a disgruntled employee or contractor tries to damage your data, immutable backups will still be safe because they cannot be deleted or changed until the lock period ends.
They use something called Write Once, Read Many (WORM) technology:
The lock period is the time during which your backup is completely unchangeable.
This could be 7 days, 30 days, 6 months, or even years — depending on your needs.
For example:
No. In fact, small businesses benefit a lot from immutable backups because they often have fewer resources to recover from disasters. Cloud-based immutable backup solutions have made this technology affordable for everyone.
Not anymore. Modern solutions, especially cloud-based ones, cost far less than paying a ransom or losing your data forever. For most businesses, the cost is tiny compared to the risk they remove.
Yes. Immutability is not a replacement for a good backup plan — it’s an extra layer of protection. You still need to:
Vembu’s system makes it simple:
In industries like healthcare, finance, and law, you often must keep certain records in their original form for years. Immutable backups guarantee the data hasn’t been altered, which makes audits and legal checks much easier.
Not at all. With solutions like Vembu, immutability can be enabled with just a few clicks — no special equipment, extra staff, or complex training needed.
Start by reviewing your current backup process:
Then, work with a trusted provider like Vembu to:

Nasmal is a Solution Architect & Business Analyst focused on AI, Data, Automation, BCP, and Process Optimization. He helps businesses evolve from reactive to proactive, data-driven, and resilient operations. With hands-on expertise, he simplifies complex tech into clear, easy-to-understand blogs.
Share it with friends!

🕓 November 24, 2025

🕓 September 16, 2025

🕓 September 5, 2025
share your thoughts