
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Transport Layer Security (TLS) inspection has long been a cornerstone of enterprise security. It enables organizations to decrypt and inspect encrypted traffic, ensuring that threats concealed within HTTPS sessions are detected and mitigated before they can compromise the network. However, traditional TLS inspection deployments have often been complex, time-intensive, and prone to operational issues when improperly configured.
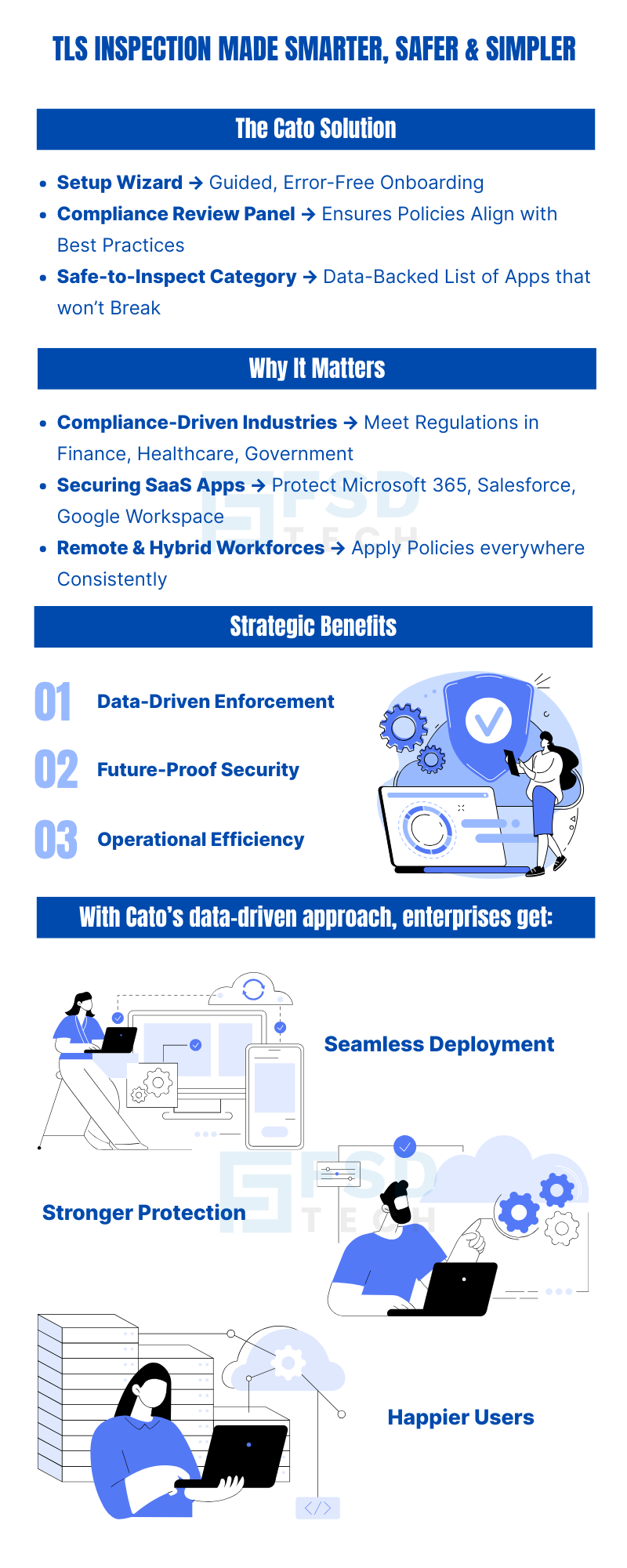
Cato Networks has addressed these challenges with the introduction of Data-Driven Safe TLS Inspection. This new capability streamlines the setup process, enforces industry best practices, and leverages advanced research to reduce user experience issues—all while maintaining strong network security.
The feature is designed to remove barriers to adopting TLS inspection by simplifying deployment and minimizing disruptions. It introduces three key enhancements:
The Setup Wizard provides guided rule creation, ensuring that administrators follow established best practices. Instead of trial-and-error configuration, the wizard offers:
A new compliance review section on the TLS Inspection page allows administrators to evaluate how their rules align with recommended best practices. This visibility makes it easier to identify policy gaps, overly broad rules, or exceptions that may expose the organization to risk.
Cato’s research team analyzed global network data to determine which applications and domains can safely undergo TLS inspection without causing breakage or performance issues. These findings have been consolidated into a dedicated Safe-to-Inspect category, which can be easily applied to inspection rules.
This reduces the uncertainty surrounding TLS inspection, minimizes disruptions, and accelerates the rollout of inspection policies across the organization.
Faster Deployment
TLS inspection can now be implemented in a fraction of the time. Guided configuration reduces manual effort and eliminates many of the complexities associated with traditional deployments.
Stronger Security Coverage
With the majority of modern web traffic encrypted, TLS inspection ensures that threats cannot exploit encryption to bypass defenses. Cato’s best-practice guidance and Safe-to-Inspect categories enable
enterprises to maintain visibility while minimizing false positives.
Consistency Across Sites and Users
Centralized guidance and compliance review features make it easier for organizations to enforce inspection policies consistently across all users and sites, reducing the risk of policy drift.
Improved End-User Experience
By excluding applications that are known to conflict with TLS inspection, user productivity is preserved. Employees remain protected without encountering unnecessary service disruptions.
Want to know how TLS inspection applies to your business? Fill out the form and get a free compliance and security readiness check.
TLS inspection is no longer optional in today’s threat landscape, where encrypted traffic has become the default and adversaries increasingly exploit it to mask their activities. However, traditional TLS inspection has often been difficult to implement effectively.
With Data-Driven Safe TLS Inspection, Cato Networks removes these barriers. By combining a guided setup wizard, compliance reviews, and research-backed application categories, enterprises can now deploy TLS inspection that is both effective and seamless.
The result is a more secure organization with fewer disruptions and a significantly improved user experience.
Ready to see Cato’s Data-Driven TLS Inspection in action? Book a free consultation with our experts.
Over 95% of web traffic today is encrypted. Without TLS inspection, threats embedded within encrypted streams can bypass security tools, leaving organizations vulnerable. TLS inspection ensures visibility into this traffic.
Cato simplifies implementation through a guided wizard, provides real-time compliance checks, and offers a Safe-to-Inspect category of applications based on global data analysis. This reduces complexity and operational risks.
No. By using the Safe-to-Inspect category and bypassing traffic known to cause conflicts, Cato minimizes disruptions and ensures user productivity is not compromised.
Yes. Many industries require TLS inspection for regulatory compliance. The simplified setup and compliance review make it easier for organizations to demonstrate adherence to these standards.
Yes. Cato continuously updates the Safe-to-Inspect category based on ongoing research and data analysis across its global network, ensuring it remains accurate and relevant.
Yes. TLS inspection is enforced consistently across all users and locations, whether they are in the office, working remotely, or in hybrid environments.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts