
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Enterprise networking has undergone a seismic shift over the past decade. The rise of cloud computing, SaaS adoption, and a distributed workforce have fundamentally changed how organizations connect users to applications and data. Traditional WAN architectures, once optimized for branch-to-data center traffic, now struggle to deliver the agility, security, and performance required in a cloud-first world.
For CISOs, Security Architects, Network Architects, and IT leaders, the stakes have never been higher. The network is no longer just a transport layer—it is the foundation of digital business, security, and user experience. As organizations grapple with escalating cyber threats, regulatory demands, and the need to support users everywhere, the limitations of legacy SD-WAN are becoming impossible to ignore. The question is no longer “if” but “when” to move beyond SD-WAN—and “how” to do it right.
SD-WAN was born out of necessity. As enterprises grew weary of the high costs and rigidity of MPLS, SD-WAN offered a compelling alternative:
SD-WAN delivered on its promise for organizations with distributed sites and predictable, data center-centric traffic patterns.
However, the emergence of cloud and hybrid work has exposed critical SD-WAN limitations:
In short, SD-WAN’s original design—optimized for branch-to-data center connectivity—no longer aligns with the realities of cloud-first, hybrid enterprises.
The modern enterprise is defined by its cloud-first strategy and decentralized workforce :
These trends demand a new approach to connectivity and security—one that is agile, scalable, and built for the cloud.
With the perimeter gone, security must evolve:
SD-WAN, even when augmented with security appliances, cannot natively deliver these capabilities at the scale and agility required by modern enterprises.
Secure Access Service Edge (SASE) represents a fundamental rethinking of enterprise networking and security. Rather than treating connectivity and security as separate silos, SASE converges them into a unified, cloud-native platform.
Core SASE Components:
SASE is not just SD-WAN with security bolted on. It is a fundamentally different architecture:
SASE architecture benefits include agility, scalability, and the ability to support digital transformation initiatives without compromising security or user experience.
Many vendors claim to offer SASE by integrating SD-WAN with security appliances—often from multiple vendors. This approach introduces complexity, policy fragmentation, and operational risk.
Cato SASE is different. Cato delivers a unified SASE platform as a single, cloud-native service:
A key differentiator for Cato is its global private backbone :
This approach delivers a secure SD-WAN alternative that is purpose-built for the demands of modern enterprises.
Cato’s security stack is fully integrated and cloud-delivered:
Security updates and threat intelligence are applied globally, ensuring all users benefit from the latest protections—without manual intervention.
| Feature/Capability | SD-WAN (Standalone) | Cato SASE (Converged) |
|---|---|---|
| Architecture | Appliance-based overlay | Cloud-native, single-vendor |
| Deployment Model | On-premises appliances | Cloud-delivered, lightweight edge devices or clientless for remote users |
| Cloud Integration | Limited, often backhauled | Native, direct-to-cloud via global PoPs |
| Scalability | Hardware-dependent | Instantly scalable, elastic |
SD-WAN requires deploying and managing physical or virtual appliances at every site. Scaling to support new locations or remote users often means more hardware, more configuration, and more complexity. In contrast, Cato SASE uses lightweight edge devices (or clientless access for remote users) and cloud-based orchestration, enabling rapid, elastic scaling with minimal operational overhead.
| Security Aspect | SD-WAN (Standalone) | Cato SASE (Converged) |
|---|---|---|
| Integrated Security | No (requires add-ons) | Yes (NGFW, SWG, CASB, ZTNA, DLP) |
| Zero Trust | Not native | Built-in |
| Policy Consistency | Fragmented, device-based | Unified, cloud-delivered |
| Threat Prevention | Variable, appliance-based | Inline, always-on |
Standalone SD-WAN encrypts traffic but relies on external appliances for advanced security. This creates policy gaps and increases the risk of misconfiguration. Cato SASE delivers a unified SASE platform with security built-in, ensuring consistent policy enforcement and comprehensive threat protection everywhere.
| Operational Factor | SD-WAN (Standalone) | Cato SASE (Converged) |
|---|---|---|
| Management | Multiple consoles, vendors | Single pane of glass |
| Troubleshooting | Siloed, complex | End-to-end visibility |
| Total Cost of Ownership | Higher (multiple tools, vendors, support contracts) | Lower (converged platform, reduced hardware, unified support) |
Cato SASE simplifies operations by consolidating networking and security into a single platform. IT teams gain deep visibility, unified policy management, and streamlined troubleshooting—reducing both operational overhead and risk. The result is a lower total cost of ownership compared to piecemeal SD-WAN plus security stacks.
A regional retail and distribution giant with more than 50 sites struggled with ongoing challenges in its SD-WAN deployment.
After migrating to Cato SASE, the manufacturer achieved:
Simplified operations: One platform, one support team, and no more hardware sprawl.
The enterprise perimeter is gone. Applications and users are everywhere. SD-WAN, while transformative in its day, cannot meet the demands of the modern, cloud-first enterprise.
Cato SASE is the next logical step—a converged, cloud-native platform that delivers secure, optimized access for every user, everywhere. The benefits are clear:
For CISOs, Security Architects, Network Architects, and IT Infrastructure Leads, the path forward is clear:
Transitioning from SD-WAN to SASE is a strategic journey. Here’s a step-by-step checklist to guide your migration:
1. Inventory your network: Map all sites, users, applications, and security controls.
2. Define success metrics: Identify key performance indicators (KPIs) for performance, security, and user experience.
3. Select pilot sites/users: Start with a subset of locations or remote users to validate the SASE approach.
4. Deploy Cato SASE edge devices or clientless access: Connect pilot sites/users to the nearest Cato PoP.
5. Migrate security policies: Translate existing firewall, VPN, and access policies into Cato’s unified policy engine.
6. Monitor and optimize: Use Cato’s analytics and visibility tools to fine-tune performance and security.
7. Expand adoption: Gradually onboard additional sites, users, and applications as legacy contracts expire.
8. Decommission legacy infrastructure: Retire SD-WAN appliances, VPN concentrators, and standalone security devices.
9. Review and refine: Continuously assess and optimize your SASE deployment to align with evolving business needs.
At the heart of Cato’s platform is its single-pass architecture . Unlike traditional solutions that process traffic multiple times—once for networking, again for security—Cato inspects and routes each packet only once. This delivers:
How it works:
1. Traffic enters the nearest Cato PoP —from a branch, remote user, or cloud connector.
2. Single-pass engine inspects traffic: Applies NGFW, SWG, CASB, ZTNA, and DLP policies in one streamlined process.
3. Traffic is routed over Cato’s private backbone to its destination—another site, a cloud service, or the internet.
4. End-to-end visibility and analytics are captured for every flow, enabling real-time monitoring and rapid troubleshooting.
This architecture is a cornerstone of Cato’s ability to deliver cloud-first network security at scale.
An India- and GCC-based IT/ITES company with thousands of remote and hybrid employees was struggling with growing challenges in its SD-WAN approach.
By adopting Cato SASE, the enterprise achieved:
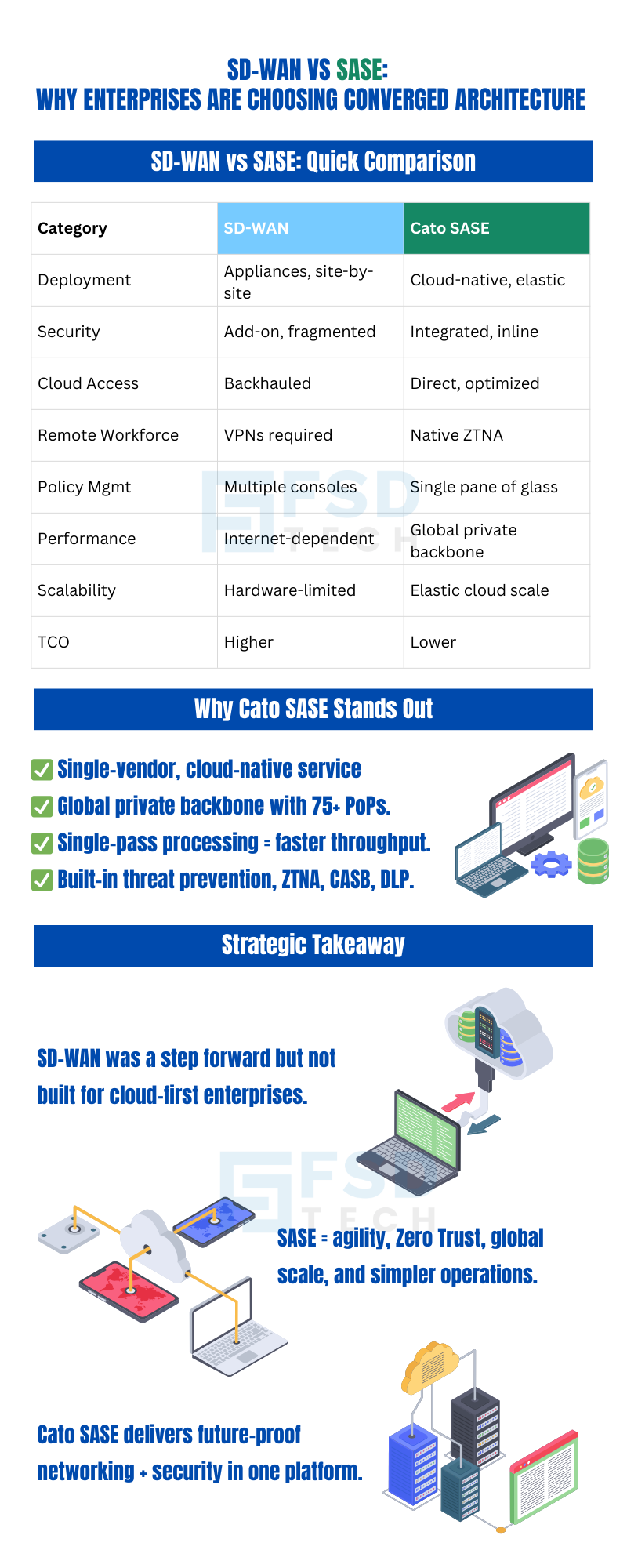
Key Differences:
| Category | SD-WAN (Standalone) | Cato SASE (Unified SASE Platform) |
|---|---|---|
| Deployment | Appliance-based, site-by-site | Cloud-native, global PoPs |
| Security | Add-on, fragmented | Integrated, inline |
| Cloud Access | Often indirect/backhauled | Direct, optimized |
| Remote Workforce | VPN required, complex | ZTNA, seamless |
| Policy Management | Multiple consoles | Single pane of glass |
| Performance | Public internet dependent | Global private backbone |
| Scalability | Hardware-limited | Elastic, cloud-scale |
| Total Cost of Ownership | High (multiple vendors) | Lower (converged, single vendor) |
The debate of SD-WAN vs SASE is not just about technology—it’s about enabling the business to move faster, stay secure, and deliver a superior user experience in a cloud-first world. SD-WAN was a critical step forward, but its limitations are now clear. The future belongs to platforms that converge networking and security, eliminate complexity, and scale with the needs of the modern enterprise.
Cato SASE explained: Cato’s single-vendor, cloud-native SASE platform delivers on this vision—providing a secure SD-WAN alternative that is built for agility, security, and simplicity. With a global private backbone, integrated security stack, and unified management, Cato empowers IT leaders to replace SD-WAN with SASE and future-proof their networks.
Strategic Takeaway: SD-WAN is no longer enough. The next logical step is a unified SASE platform that delivers cloud-first network security, Zero Trust Network Access, and operational excellence—everywhere your business operates.
Ready to move beyond SD-WAN? Contact FSD-Tech for a personalized assessment and see how converged SASE can transform your enterprise network. Contact Now
No. While SASE incorporates SD-WAN’s connectivity, it natively integrates a full security stack—firewall, ZTNA, CASB, SWG, DLP—and delivers both networking and security as a unified, cloud-native service. This convergence enables consistent policy enforcement, deep visibility, and operational simplicity that cannot be achieved by simply bolting security onto SD-WAN.
Yes. Many organizations choose to replace SD-WAN with SASE in phases. You can start by onboarding select sites or remote users to Cato SASE, validate the architecture, and then expand adoption as legacy contracts expire or as business needs evolve. This incremental approach reduces risk and disruption.
Cato’s global private backbone provides predictable latency, high availability, and optimized routing between all connected sites and users. Unlike SD-WAN solutions that rely on the variable public internet, Cato’s backbone is SLA-backed and connects directly to major cloud providers, ensuring consistent performance for critical applications.
Cato SASE enables secure, optimized access for users everywhere—branch, home, or on the go. By replacing legacy VPNs with Zero Trust Network Access (ZTNA), users benefit from seamless, direct-to-cloud connectivity with integrated security. This improves user experience, reduces IT support tickets, and strengthens the overall security posture.
Yes. SASE is purpose-built for cloud-first organizations, delivering direct, secure access to SaaS and IaaS applications without backhauling or performance bottlenecks. Integrated security and unified management further reduce risk and operational overhead compared to traditional SD-WAN solutions.
SASE simplifies compliance by enforcing consistent security policies, access controls, and data protection measures across all users and locations. Centralized visibility and reporting make it easier to demonstrate compliance with regulations such as GDPR, HIPAA, and PCI DSS.
Cato SASE delivers ZTNA as a core component of its platform. Access is granted based on user identity, device posture, and context, with continuous verification for every session. This ensures that only authorized users and devices can access sensitive resources, regardless of location.
Yes. Cato SASE provides a fully integrated security stack—including NGFW, SWG, CASB, ZTNA, and DLP—delivered as a cloud service. This allows organizations to retire legacy firewalls, VPN concentrators, and web gateways, consolidating security into a single, unified platform.
Moving to a unified SASE platform like Cato dramatically simplifies operations. IT teams manage networking and security from a single console, with end-to-end visibility and analytics. Automated updates, global policy enforcement, and integrated threat intelligence reduce manual effort and operational risk.
Cato’s global private backbone and distributed PoPs enable organizations to connect new sites and users anywhere in the world with minimal effort. The platform scales elastically, ensuring consistent performance and security regardless of geographic location. This makes it ideal for supporting mergers, acquisitions, and rapid business growth.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts