.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

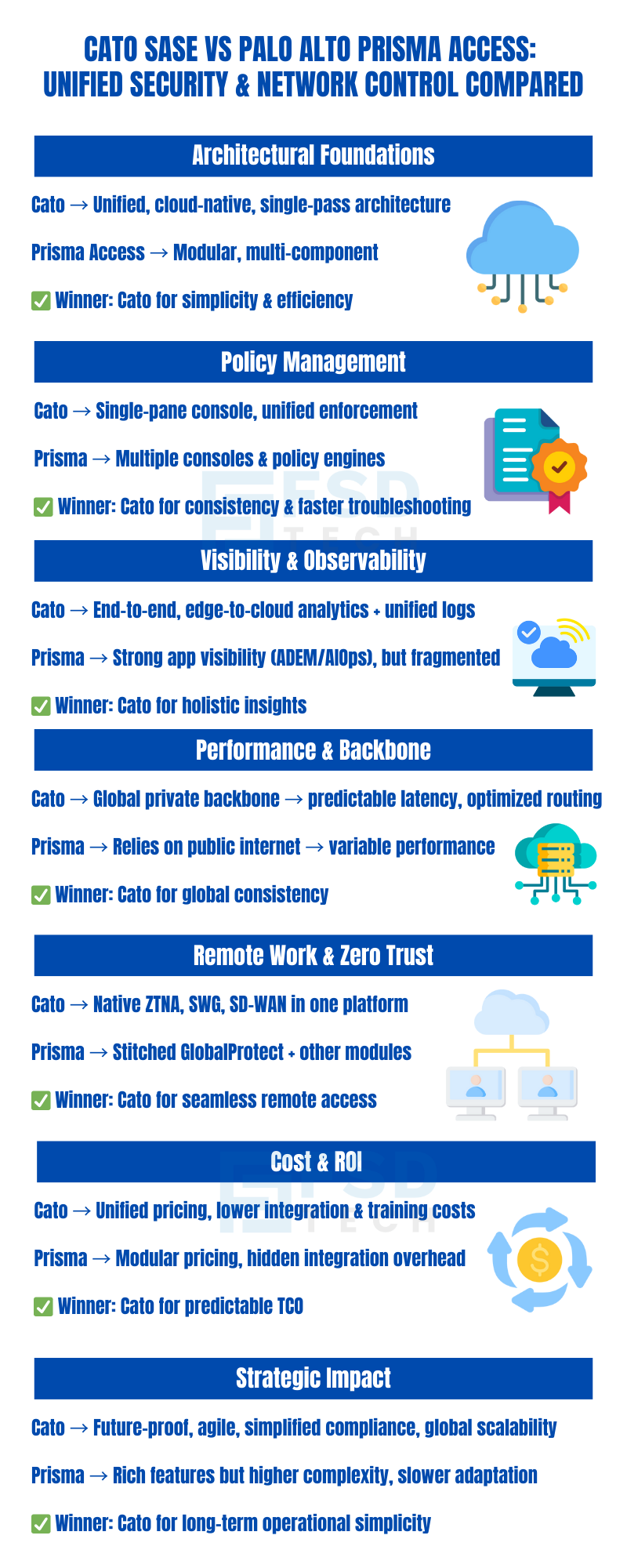
The rapid evolution of cloud, mobility, and remote work has made Secure Access Service Edge (SASE) a strategic imperative for organizations seeking unified security and network control. As enterprises rearchitect their infrastructure for agility and resilience, the choice of SASE platform can determine not only security posture but also operational efficiency, user experience, and long-term scalability.
Two of the most prominent SASE contenders— Cato Networks SASE Cloud Platform and Palo Alto Networks Prisma Access —offer distinct architectural philosophies and operational models. For security architects, CISOs, and infrastructure leaders, understanding these differences is critical to making an informed, future-proof investment.
This in-depth comparison examines how Cato’s fully integrated, cloud-native single-pass architecture delivers superior simplicity, operational efficiency, and visibility compared to Palo Alto’s Prisma Access, which leverages a more fragmented product ecosystem. We’ll explore architecture, policy management, visibility, performance, and remote work enablement, providing actionable insights and real-world scenarios to guide your SASE strategy.
SASE is a cloud-delivered framework that converges network and security functions—including SD-WAN, secure web gateway (SWG), cloud access security broker (CASB), firewall-as-a-service (FWaaS), and zero trust network access (ZTNA)—into a single service. This convergence enables organizations to secure users, devices, and applications everywhere, with consistent policy enforcement and visibility.
Traditional network and security architectures struggle to keep pace with distributed workforces, cloud adoption, and evolving threats. SASE’s promise lies in its ability to unify disparate technologies, reduce complexity, and deliver security and performance at scale. However, not all SASE solutions are created equal—architectural choices can have profound impacts on manageability, scalability, and user experience.
Cato Networks was founded with a singular vision: to converge networking and security into a single, global, cloud-native platform. Cato’s architecture is built from the ground up as a unified fabric, integrating SD-WAN, SWG, CASB, ZTNA, and threat prevention in a single-pass engine. All traffic—regardless of source, destination, or protocol—is inspected and processed once, minimizing latency and avoiding the inefficiencies of chaining multiple appliances or services.
This single-pass architecture means that policies are enforced consistently, analytics are comprehensive, and troubleshooting is streamlined. The entire platform is managed through a single interface, providing end-to-end visibility and control from edge to cloud.
Palo Alto Networks’ Prisma Access brings together a suite of security and networking services, leveraging the company’s established PAN-OS firewall technology, GlobalProtect for remote access, and CloudGenix for SD-WAN (acquired in 2020). While Prisma Access is cloud-delivered and offers robust security features, its architecture is inherently modular—different components are stitched together to deliver the full SASE experience.
This modularity can introduce integration challenges, especially when deploying across diverse environments or scaling globally. Policy enforcement may occur in different engines, and administrators often need to navigate multiple consoles for configuration, monitoring, and troubleshooting.
| Feature | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Core Architecture | Unified, cloud-native, single-pass | Modular, multi-component |
| SD-WAN Integration | Native | Acquired (CloudGenix) |
| Policy Enforcement | Single engine, single console | Multiple engines, multiple consoles |
| Backbone | Global private backbone | Public internet |
| Deployment Complexity | Low | Moderate to high |
Cato’s platform is designed for operational simplicity. All security and networking policies are managed from a single, unified console. This single-pane-of-glass approach eliminates the need to synchronize configurations across disparate systems, reducing the risk of policy drift and misconfiguration. Administrators can define, enforce, and monitor policies consistently across all users, locations, and applications.
Key benefits include:
Prisma Access, while feature-rich, often requires administrators to interact with multiple consoles and policy engines. For example, SD-WAN configuration may be managed through the CloudGenix interface, while security policies are handled in PAN-OS, and remote access is configured in GlobalProtect. This fragmentation increases administrative overhead, complicates change management, and can slow down incident response.
Operational challenges include:
| Policy Management Area | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Policy Creation | Single unified console | Multiple consoles/modules |
| Enforcement Consistency | High | Variable |
| Change Management | Streamlined | Complex |
| Troubleshooting | Centralized | Fragmented |
Cato delivers comprehensive, edge-to-cloud visibility through its unified platform. Administrators can monitor user experience, application performance, and security events from a single interface. This holistic view enables rapid identification of issues, root cause analysis, and proactive optimization.
Key capabilities:
Prisma Access provides strong observability features, particularly with Autonomous Digital Experience Management (ADEM) and AIOps. These tools offer deep insights into application performance and user experience. However, due to the modular nature of the platform, visibility is often app-centric and may not extend seamlessly across the entire network and security fabric. Administrators may need to correlate data from multiple sources to gain a complete picture.
Observability considerations:
| Visibility Feature | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Edge-to-Cloud Visibility | Comprehensive, unified | App-centric, fragmented |
| Analytics | Real-time, historical | Advanced, module-specific |
| Event Correlation | Automatic, holistic | Manual, multi-source |
| Compliance Reporting | Simplified | Requires data aggregation |
Cato operates a global private backbone, purpose-built to deliver predictable latency, optimized routing, and consistent performance for all users and locations. This backbone interconnects Cato PoPs (Points of Presence) worldwide, ensuring that traffic is always routed over the most efficient path, regardless of user location or application destination.
Performance benefits:
Prisma Access relies on the public internet for site-to-site and remote connectivity. While Palo Alto has invested in optimizing its cloud infrastructure, the inherent variability of the public internet can impact performance, particularly for global organizations or those with latency-sensitive applications. Performance may fluctuate based on ISP routing, congestion, and regional internet conditions.
Performance considerations:
| Backbone/Connectivity | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Backbone Type | Global private backbone | Public internet |
| Latency | Predictable, low | Variable, higher risk |
| Application Performance | Optimized | Dependent on internet |
| Global Consistency | High | Variable |
Cato natively integrates Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and SD-WAN within a single platform. This enables organizations to deliver secure, optimized remote access to users anywhere, without the need to stitch together multiple products or manage complex integrations. Policy enforcement, visibility, and user experience are consistent, regardless of location or device.
Integrated remote work capabilities:
Prisma Access provides comprehensive security for remote users, leveraging GlobalProtect for VPN and ZTNA, and integrating SWG and SD-WAN through additional modules. However, these capabilities are delivered via a combination of native and acquired technologies, requiring careful integration and ongoing management. Organizations may need to deploy multiple agents, configure separate policies, and ensure interoperability between modules.
Remote work challenges:
| Remote Work/Zero Trust | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| ZTNA Integration | Native, unified | Via GlobalProtect, modular |
| SWG/SD-WAN Integration | Native, unified | Acquired, modular |
| Remote Access Client | Single | Multiple possible |
| Policy Consistency | High | Variable |
Consider a multinational enterprise with offices in 30 countries. Deploying Cato SASE, the organization achieves:
In contrast, a similar rollout with Prisma Access requires:
The result: Cato delivers faster time-to-value, reduced operational overhead, and a more predictable user experience.
For a manufacturing firm with thousands of IoT devices, Prisma Access’s advanced IoT security features offer granular control. However, integrating these features with legacy network segments can be challenging due to the modular architecture. Cato’s unified platform simplifies policy enforcement across all device types, reducing operational risk and complexity.
Other industry scenarios:
Cato is recognized for competitive pricing and clear ROI, particularly for organizations prioritizing simplicity and operational efficiency. The unified platform reduces the need for multiple vendors, appliances, and integration projects, resulting in lower capital and operational expenditures.
Prisma Access is typically more expensive, reflecting its advanced security features and enterprise-grade capabilities. However, the modular approach can introduce hidden costs related to integration, training, and ongoing management.
| Cost/ROI Factor | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Licensing Model | Unified, predictable | Modular, variable |
| Hardware/Appliance Needs | Minimal | May require additional devices |
| Integration Costs | Low | Higher |
| Operational Overhead | Low | Moderate to high |
| Time-to-Value | Fast | Moderate to slow |
Selecting a SASE platform is a long-term strategic decision. Cato’s unified, cloud-native architecture positions organizations to adapt quickly to new requirements, scale globally, and integrate emerging technologies without major re-architecture. The single-pass engine and global backbone ensure that security and performance keep pace with business growth.
Prisma Access, while robust and feature-rich, may require ongoing integration efforts as new modules are added or existing ones evolve. Organizations should weigh the benefits of advanced features against the potential for increased complexity and slower adaptation to changing needs.
| Comparison Area | Cato SASE Cloud Platform | Palo Alto Prisma Access |
|---|---|---|
| Unified SASE Architecture | Yes | No (modular) |
| Single-Pass Inspection SASE | Yes | Partial |
| Global Private Backbone vs Public Internet | Private backbone | Public internet |
| Integrated Cloud-Native Security | Yes | Modular, some acquired |
| Network Visibility in SASE Platforms | End-to-end, unified | App-centric, fragmented |
| Policy Management | Single-pane, unified | Multi-console, complex |
| Remote Work SASE Platform | Native ZTNA, SWG, SD-WAN | Stitched modules, integration |
| Deployment Complexity | Low | Moderate to high |
| Cost Predictability | High | Variable |
| Scalability | Seamless, global | Requires integration |
| Zero Trust with Cato vs Palo Alto | Native, unified | Modular, via GlobalProtect |
Selecting the best SASE solution for 2025 and beyond requires a deep understanding of architectural differences, operational models, and long-term strategic implications. Cato SASE stands out with its unified, cloud-native, single-pass architecture, delivering superior simplicity, operational efficiency, and end-to-end visibility. Its global private backbone ensures predictable performance, while native integration of ZTNA, SWG, and SD-WAN streamlines remote work and Zero Trust initiatives.
Palo Alto Prisma Access offers robust security features and advanced observability, but its modular, multi-component approach can introduce complexity in deployment, policy management, and ongoing operations. Organizations must weigh the benefits of advanced features against the potential for increased administrative overhead and integration challenges.
For security architects, CISOs, and network engineers evaluating SASE vendor options, the choice between Cato Networks vs Palo Alto Networks hinges on priorities: operational simplicity, unified architecture, and predictable performance versus modular flexibility and advanced, but potentially fragmented, security capabilities.
In a landscape where agility, visibility, and unified control are paramount, Cato SASE delivers a compelling value proposition for enterprises seeking to future-proof their security and network infrastructure. As you evaluate your SASE strategy, consider not only feature checklists but also the long-term impact of architectural decisions on your organization’s ability to adapt, scale, and thrive in a cloud-first world.
Ready to see which SASE model fits your enterprise best? Talk with our experts for tailored insights. Book a Free Consultation →
Cato offers a fully converged, cloud-native platform with a single-pass engine, integrating all security and networking functions into one fabric. This design eliminates the need for multiple appliances or stitched-together modules, simplifying deployment, management, and scaling. In contrast, Prisma Access relies on a modular approach, combining components like PAN-OS, GlobalProtect, and acquired technologies, which can increase complexity and integration overhead.
Cato’s global private backbone ensures predictable latency and optimized routing for all users and locations, delivering consistent application performance even for latency-sensitive workloads. Prisma Access, by contrast, relies on the public internet for site-to-site and remote connectivity, which can introduce variability in performance due to ISP routing, congestion, and regional differences.
Cato provides a single-pane-of-glass for unified policy enforcement, allowing administrators to define and monitor policies across all users, locations, and applications from one console. Prisma Access often requires managing policies across multiple consoles and modules, increasing administrative overhead and the risk of configuration drift.
Cato is recognized for its straightforward deployment and operational simplicity, enabling organizations to quickly onboard new sites and users with minimal configuration. Prisma Access, while offering advanced features, may require more time and expertise to deploy and scale due to its modular architecture and the need to integrate multiple components.
Yes, both Cato and Prisma Access support Zero Trust Network Access (ZTNA) and secure remote access. However, Cato delivers these capabilities natively within a single platform, ensuring consistent policy enforcement and user experience. Prisma Access may require integrating additional modules or third-party solutions to achieve full Zero Trust and remote work capabilities.
Prisma Access’s modular architecture can introduce complexity in deployment, policy management, and ongoing operations. The reliance on the public internet for connectivity can result in variable performance, and managing multiple consoles increases the risk of configuration drift. Organizations may also face higher integration and operational costs compared to Cato’s unified platform.
Cato provides end-to-end, unified visibility across all users, devices, and applications through a single interface. This enables rapid troubleshooting and comprehensive analytics. Prisma Access offers strong observability, particularly for specific applications, but visibility can be fragmented due to the modular architecture, requiring administrators to correlate data from multiple sources.
Cato’s global private backbone and unified management make it well-suited for multinational organizations seeking consistent security and performance across all regions. Rapid onboarding, centralized policy enforcement, and predictable latency are key advantages. Prisma Access can support global deployments but may require more effort to optimize performance and manage policies across diverse environments.
Cato is recognized for competitive, predictable pricing and clear ROI, especially for organizations prioritizing simplicity and operational efficiency. The unified platform reduces the need for multiple vendors and integration projects. Prisma Access is typically more expensive, with costs reflecting its advanced security features and modular approach. Hidden costs may arise from integration, training, and ongoing management.
Cato’s unified platform simplifies compliance reporting by providing centralized visibility, logging, and policy enforcement. This makes it easier to demonstrate adherence to regulatory frameworks such as PCI DSS, HIPAA, and GDPR. Prisma Access also offers robust compliance features, but administrators may need to aggregate data from multiple modules and consoles to generate comprehensive reports.
Both platforms are designed to support phased migrations from legacy architectures. Cato’s unified, cloud-native approach can simplify migration by consolidating multiple functions into a single platform, reducing the number of moving parts. Prisma Access supports migration as well, but the modular nature may require more careful planning and integration to avoid disruption.
Cato’s SD-WAN is natively integrated into its unified platform, allowing seamless management and policy enforcement alongside security functions. Prisma Access delivers SD-WAN capabilities through CloudGenix, an acquired technology, which may require separate configuration and management, increasing complexity for administrators.
A unified SASE architecture, such as Cato’s, positions organizations to adapt quickly to new requirements, scale globally, and integrate emerging technologies without major re-architecture. It reduces operational risk, accelerates time-to-value, and ensures consistent security and performance as the business evolves. Modular solutions may require ongoing integration and adaptation as new needs arise.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts