.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

It’s 1:48 AM in Riyadh.
You’re the CEO of a growing retail chain in the GCC. Sales are up, you’ve just opened a new branch in Jeddah, and your online orders are booming. Life is good.
Then your phone rings.
On the other end, your IT manager is panicked:
“Sir… we think we’ve been hit by ransomware. One of our systems is locked. Files are encrypted. We can’t process sales.”
You’re groggy, but your mind races:
Didn’t we already buy antivirus software? Isn’t that supposed to protect us?
The IT manager continues:
“Yes, we have antivirus. But this wasn’t caught. The malware slipped through. It’s spreading.”
By sunrise, your sales system is frozen. Deliveries are delayed. Customers are complaining. Staff can’t log in. The attackers are demanding $50,000 in Bitcoin.
Now imagine the same story — but with one difference.
Instead of waking up to disaster, you wake up to a simple message from your IT provider:
“A suspicious file was detected at 2:03 AM. EDR contained it instantly. The infected laptop was isolated. No data loss. No downtime. Your systems are safe.”
That’s the power of EDR (Endpoint Detection & Response).
Let’s strip away the jargon.
Think of every computer, laptop, tablet, and phone in your company as a door into your business. Each employee is holding a set of keys.
Antivirus is like a security guard at the front door. He checks IDs — but only for criminals he’s seen before. If a new intruder shows up in disguise, he walks right past.
EDR, on the other hand, is like having:
In plain words:
Unlike antivirus, which just blocks known viruses, EDR deals with the unknowns — the brand-new threats designed to bypass traditional defenses.
You might think: “But I’m not a bank or a government agency. Why would hackers care about my small or mid-sized business?”
Here’s the uncomfortable truth: they care a lot.
Hackers know that SMBs often:
To hackers, this means: low effort, high reward.
In Dubai, Nairobi, Lagos, or Cairo — employees work from home, coffee shops, airports, or even on mobile phones. Every one of those devices is a potential doorway for cybercriminals.
A single compromised laptop on a home Wi-Fi network could open the gates to your entire business network.
Governments across the GCC & Africa have introduced tough data protection laws:
If your customer data is leaked, the fines can be crushing — not to mention the loss of trust.
Fact: Studies show that 60% of SMBs close within 6 months of a major cyberattack. Not because they want to — but because the financial and reputational damage is too great.
Protect your business before it’s too late — discover how EDR shields SMBs from today’s cyber threats. Click Here
Let’s imagine how EDR works inside your business.
Every device is under watch — like having CCTV cameras inside every office and store. If an employee plugs in a suspicious USB stick or downloads an unknown file, the system notices immediately.
EDR uses AI and machine learning to spot unusual behavior. For example:
These are red flags.
The moment a threat is confirmed, the infected device is isolated from the rest of the network. Like locking a fire door during a blaze — the fire is contained to one room, not the whole building.
The system creates a full timeline of what happened:
Finally, EDR rolls back changes, cleans the system, and restores it to a safe state. Business continues with minimal disruption.
Imagine you’re driving in Nairobi traffic.
One prevents basic harm. The other saves your life when the unexpected happens.
Here’s the difference in a table (business-friendly):
Feature | Antivirus | EDR |
|---|---|---|
| Detects Known Threats | ✅ | ✅ |
| Detects New Threats | ❌ | ✅ |
| Real-Time Monitoring | ❌ | ✅ |
| Incident Response | ❌ | ✅ |
| Detailed Attack Analysis | ❌ | ✅ |
An employee opened a fake invoice attachment.
A receptionist clicked a phishing email that looked like it came from the insurance provider.
Hackers attempted to steal login credentials using keylogger malware.
Don’t wait for a cyberattack to strike — see how EDR can safeguard your business now.
At FSD-Tech, we deliver Managed EDR powered by Xcitium — specifically designed for SMBs and mid-market firms in GCC & Africa.
Here’s why it’s different:
It’s like having a cybersecurity command center without hiring 10 full-time staff.
Data protection isn’t just a technical issue. It’s a legal and reputational issue.
With EDR, you can:
Whether you’re under UAE PDPL, Saudi PDPL, Nigeria NDPR, or South Africa POPIA, EDR helps keep you on the right side of the law.
Let’s compare:
Scenario | Without EDR | With EDR |
|---|---|---|
| Ransomware | Pay ransom + days of downtime | Attack blocked instantly |
| Data Breach | Loss of trust + regulatory fines | Contained before spreading |
| Unknown Malware | Weeks to detect & respond | Detected & neutralized in seconds |
Takeaway: Prevention is always cheaper than recovery.
Would you drive on Sheikh Zayed Road without a seatbelt?
Would you fly without a safety check?
Then why would you run your business without EDR protection?
Cybercriminals don’t care whether you’re big or small. They care if you’re protected or not.
With FSD-Tech Managed EDR powered by Xcitium, you get:
EDR isn’t optional anymore. It’s survival.
Book a free consultation with our experts to design your EDR strategy today. Schedule now
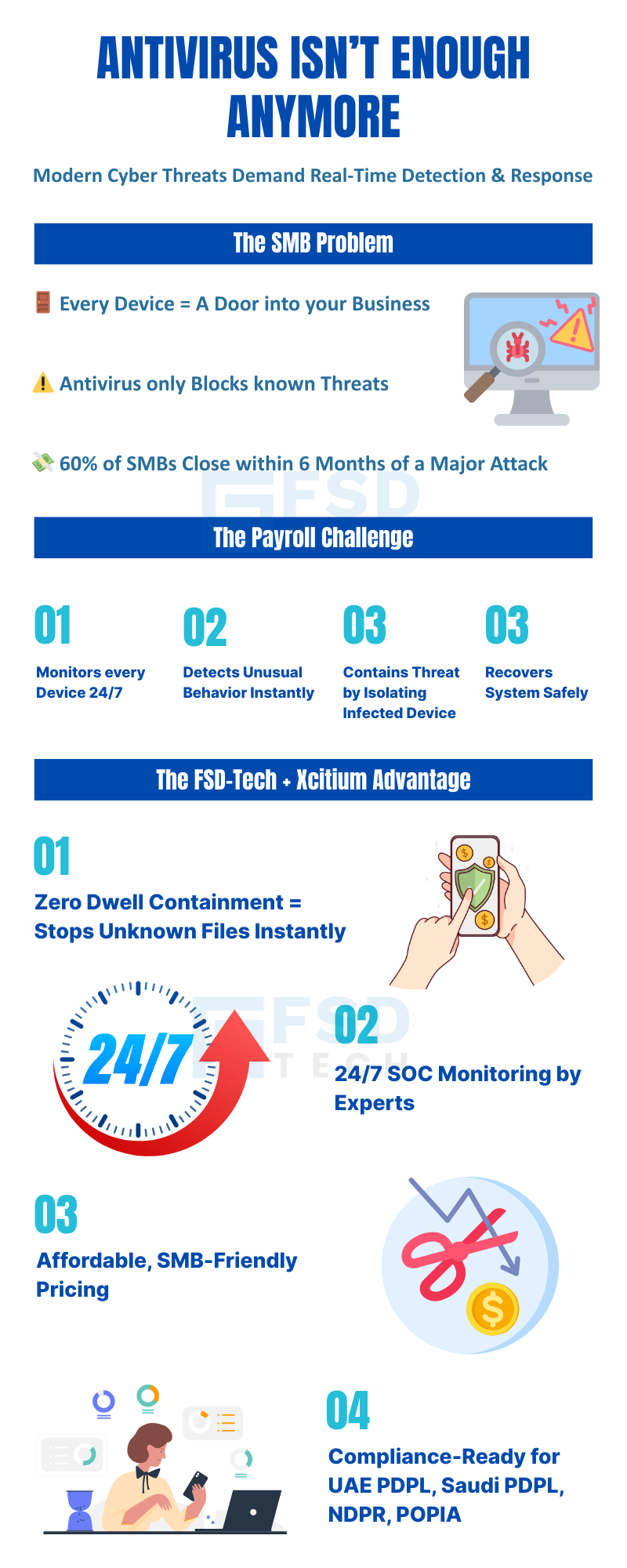
EDR (Endpoint Detection and Response) is advanced security software that watches over every device in your business — laptops, desktops, tablets, and smartphones. It detects suspicious activity, blocks dangerous files, and isolates threats before they can spread. Unlike traditional antivirus, it works in real time and stops new, unknown threats too.
If you’re an SMB in GCC or Africa, EDR is essential because cybercriminals increasingly target smaller companies with weaker defenses.
EDR works by:
1️⃣ Monitoring every endpoint 24/7.
2️⃣ Detecting unusual or risky activity instantly.
3️⃣ Isolating the affected device before the threat spreads.
4️⃣ Investigating the cause and impact.
5️⃣ Restoring the device to a safe state.
It’s like having a security guard for every device that never takes a break.
SEO Keywords: endpoint security monitoring GCC, SMB cyber protection Africa, EDR monitoring service GCC.
Antivirus mostly detects known threats and can miss new or complex attacks. EDR goes further by:
This means EDR is far better at protecting SMBs in GCC & Africa from modern cyberattacks like ransomware and phishing.
SEO Keywords: difference between EDR and antivirus, advanced endpoint security GCC, SMB cybersecurity Africa.
SMBs here face rising cyber threats due to:
EDR is cost-effective and scalable, giving SMBs enterprise-level protection without the expense of hiring a large IT security team.
SEO Keywords: SMB cybersecurity GCC, cost-effective EDR GCC, endpoint security Africa SMB.
Yes. With solutions like Xcitium EDR + Zero Dwell Containment, ransomware is detected and isolated before it can encrypt files. This means even if a malicious file is opened, it’s contained immediately, preventing damage.
SEO Keywords: ransomware protection GCC, Zero Dwell EDR Africa, SMB ransomware prevention GCC.
Absolutely. EDR protects devices no matter where they are — in the office, at home, or on the road. This makes it perfect for SMBs in GCC & Africa with hybrid or fully remote teams.
SEO Keywords: remote workforce endpoint security GCC, EDR for hybrid teams Africa, managed endpoint protection GCC.
Most modern EDR solutions, like those used by FSD-Tech, can detect and respond to threats in seconds. This instant reaction is critical for avoiding costly downtime and data loss.
SEO Keywords: real-time EDR detection GCC, fast threat response Africa, instant endpoint protection GCC.
No. EDR runs quietly in the background without affecting normal work. It only acts when it detects something suspicious, so your employees can work without interruptions.
SEO Keywords: lightweight EDR GCC, seamless endpoint protection Africa, SMB-friendly EDR GCC.
Not at all. With managed EDR services from FSD-Tech, you pay a predictable monthly fee that’s far less than the cost of recovering from a breach. In fact, most SMBs find EDR more affordable than hiring even one full-time security staff member.
SEO Keywords: affordable EDR GCC, cost-effective endpoint security Africa, managed EDR pricing GCC.
Yes. EDR provides detailed logs and reports of security events, which can be used to show compliance with laws like UAE’s Dubai Data Law, KSA’s NCA guidelines, and Africa’s POPIA or NDPR.
SEO Keywords: EDR compliance GCC, endpoint compliance Africa SMB, SOC-ready EDR GCC.
In an MSSP setup, your EDR is monitored by a 24/7 SOC team. This means real people respond to alerts in real time, not just automated systems. This combination is powerful for SMB cybersecurity.
SEO Keywords: managed EDR MSSP GCC, SOC monitored endpoint security Africa, SMB MSSP GCC.
EDR can detect:
It’s designed to defend against both common and advanced cyber threats.
SEO Keywords: advanced threat detection GCC, SMB cyberattack prevention Africa, EDR zero-day protection GCC.
It’s simple:
1️⃣ Contact FSD-Tech for a risk assessment.
2️⃣ We deploy EDR on your devices remotely.
3️⃣ You get instant protection and monitoring from day one.
SEO Keywords: EDR deployment GCC SMB, start EDR service Africa SMB, managed endpoint onboarding GCC.
Zero Dwell Containment is a unique technology from Xcitium that isolates any unknown file instantly before it can run. Combined with EDR, it ensures even brand-new threats are stopped without waiting for updates or patches.
SEO Keywords: Zero Dwell Containment GCC, Xcitium EDR Africa SMB, instant threat isolation GCC.
FSD-Tech specializes in SMB cybersecurity in GCC & Africa, offering:

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts