
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

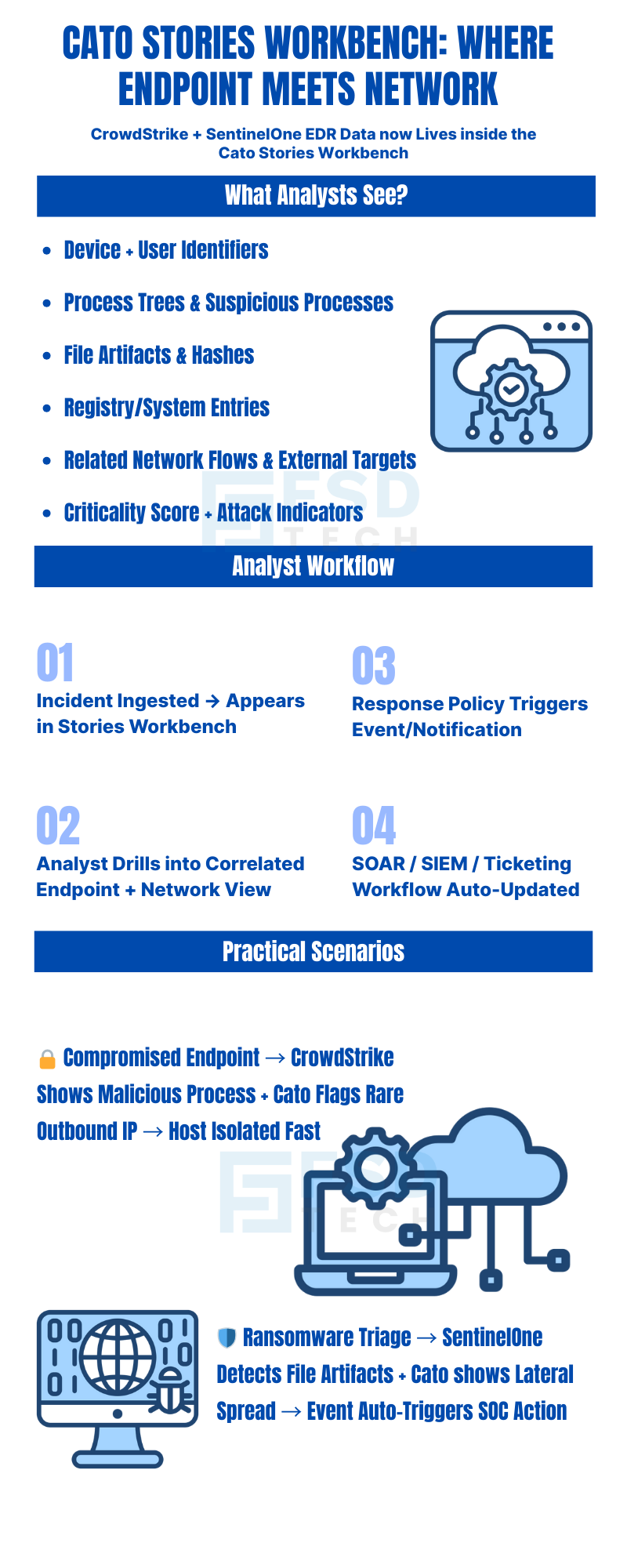
Security operations teams need speed, context, and confidence when investigating incidents. To accelerate triage and reduce mean time to resolution, Cato has extended its XOps analytics platform so that incident and endpoint story data from CrowdStrike and SentinelOne EDR can be ingested and investigated directly in the Stories Workbench. This update centralizes EDR and network signals in a single investigation workflow, enabling security teams to pivot faster between endpoint and network evidence and take guided remediation actions from one console.
Cato XOps now receives and displays endpoint incident stories from CrowdStrike and SentinelOne inside the Stories Workbench. Customers with XDR Pro, XOps, or MDR licenses can access and investigate those endpoint stories.
When the EDR integration is configured, Stories Workbench surfaces combined views of Cato native network signals and EDR incident data so analysts see correlated context (network + endpoint) for the same incident in one place.
The stories include rich endpoint telemetry such as device and user details, processes, files, registry values and additional artifacts relevant to the incident — giving investigators the file- and process-level detail they need to validate or refute an alert.
Single pane of glass for investigation. By bringing CrowdStrike and SentinelOne story data into the Stories Workbench, security teams avoid tool-switching between separate consoles to stitch endpoint and network evidence together. The Stories Workbench was designed to present correlated “stories” (groups of related signals) so analysts can view the complete picture in one place.
Faster, more accurate triage. Endpoint artifacts (processes, files, registry entries) paired with Cato’s network traffic context helps security teams quickly determine whether suspicious endpoint activity is isolated, part of lateral movement, or related to external command-and-control. The consolidated view reduces false positives and shortens investigation loops.
Actionable automation and notifications. XOps’ Response Policy can be configured to generate events, send notifications, or push story events to third-party systems when defined criteria are met. This means teams can automate alerting, ticket creation, or SOAR playbooks based on combined network+endpoint story criteria. (By default events are not generated until Response Policy rules are created.)
Flexible licensing and access model. Stories can be generated even without a paid XOps license, while full access to view and investigate stories in the Stories Workbench is provided to customers with XOps, XDR Pro, or MDR licenses—ensuring organizations with the appropriate service level can benefit from the integrated investigation experience.
When CrowdStrike or SentinelOne incidents are surfaced as stories in the Stories Workbench, the available data typically includes:
Device identifiers and mapped user identity
Process trees and suspicious process details
File artifacts and hashes observed on the host
Registry keys or system artifacts relevant to the incident
Related network flows and external targets discovered by Cato’s telemetry
Timestamps, criticality score and indication of attack (to help prioritize)
This combined dataset allows an analyst to move from high-level alert to detailed root-cause evidence without leaving the Stories Workbench.
Verify license and prerequisites. Confirm your organization’s entitlement (XOps, XDR Pro, or MDR where applicable) and ensure you have administrative access to the Cato Management Application.
Configure the EDR connector. In the Cato console’s detection & response integrations area, create and configure the connector for CrowdStrike and/or SentinelOne using the vendor integration settings and credentials. Once the connector is created, the EDR incidents will begin populating as stories in the Stories Workbench.
Review stories in the Stories Workbench. Use filters, grouping and the criticality ranking to surface high-priority incidents. Drill down into each story for device, user, process and file details, and review the related network traffic that Cato captured.
Configure Response Policy rules. Define Response Policy rules to send notifications or generate events for selected story criteria (for example: high-criticality incidents, specific sources, or particular indications). Events can be exported to the Events page and integrated with downstream SOAR, SIEM, or ticketing systems.
Automate and iterate. Use subscription groups, webhooks or mail lists to automate incident notifications. Tune Response Policy rules to reduce noisy alerts and ensure high-confidence stories generate the right operational workflows.
Want to see how unified endpoint + network investigations could transform your SOC? Fill out the form and our team will contact you with tailored recommendations.
Lower MTTR (mean time to respond). Correlated endpoint + network evidence shortens the time to validate incidents and to escalate or remediate.
Improved investigator efficiency. Analysts spend less time pivoting between consoles; contextual links and story grouping in the Workbench streamline triage.
Stronger hunting and post-incident analysis. Consolidated stories make it easier to hunt for related activity across hosts and sites and to export full story data for deeper forensic analysis (the Events export includes the additional_data JSON for full story context).
Easier SOC orchestration. Response Policy-driven events and integrations enable SOCs to feed stories into existing playbooks and ticketing flows, enabling consistent operational response.
Compromised endpoint with suspicious egress. An analyst sees a CrowdStrike story that reports a malicious process and, in the same story, Cato shows suspicious outbound connections to a rare external IP. The combined view supports a fast containment decision (isolate host, block IP).
Ransomware triage. A SentinelOne incident includes ransomware file artifacts and a process trace; Stories Workbench shows contemporaneous lateral attempts on internal hosts. Response Policy can auto-generate an event for immediate SOC action.
Threat hunting across indicators. Hunt queries use story grouping, filters and criticality scoring to find other devices exhibiting similar process or network patterns, enabling faster containment of an emerging campaign.
The capability requires EDR integration setup in the Cato Management Application and is available for Socket, vSocket and supported agent deployments where XOps ingestion is possible. Verify entitlement (XOps, XDR Pro or MDR) for full Stories Workbench access. Stories may be generated without a paid XOps license, but viewing and investigating stories in the Workbench requires the listed license tiers.
Events are generated only when Response Policy rules specify them; by default story events are not generated. Use Response Policy rules to export events, notify teams, or integrate with third-party workflows. The Events page supports exporting the full story JSON for deep analysis.
Integrating CrowdStrike and SentinelOne EDR stories into the Stories Workbench is an important step in unifying endpoint and network operations. The extension delivers consolidated telemetry, reduces investigative friction, and enables automated SOC workflows via Response Policy rules. For security teams, the result is faster, more accurate incident response and better operational alignment between endpoint detection and network detection capabilities.
Ready to unify your endpoint and network investigations? Book your free XOps Consultation with Cato experts today and accelerate your SOC workflows.
Full Stories Workbench access for CrowdStrike and SentinelOne stories is provided to customers with XOps, XDR Pro, or MDR licensing. Stories can be generated without a license, but viewing/investigating in the Workbench requires the listed entitlements.
After the EDR connector is created and validated in the Cato console, endpoint incidents begin to appear as stories in the Stories Workbench. Use the Workbench filters and grouping to focus on high-priority incidents.
Yes. Configure the XOps Response Policy to generate events and notifications for story criteria. Events can be exported to the Events page and integrated with external systems via webhooks or third-party connectors.
Stories incorporate device and user identifiers, relevant processes, file artifacts, registry values, and other contextual data from the EDR incident—alongside Cato’s network telemetry for the same incident.
Stories can be grouped and filtered by source, indication, criticality and other criteria in the Workbench—enabling efficient hunting for related activity and reducing time spent correlating events across separate tools.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts