
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Threats to your network are no longer limited to known malware or signature-based exploits. To be honest, relying on old-school firewalls today is like using a screen door to stop a flood. Modern enterprises need dynamic protection that works in real time, at cloud scale.
Cato Networks delivers advanced threat prevention capabilities—including IPS, Anti-Malware, and TLS Inspection—all managed through a unified cloud-native architecture.
This guide shows you how to enable and configure these security services in the latest Cato Management Application (CMA). We will also look at what to expect regarding operational behavior so you aren't caught off guard.
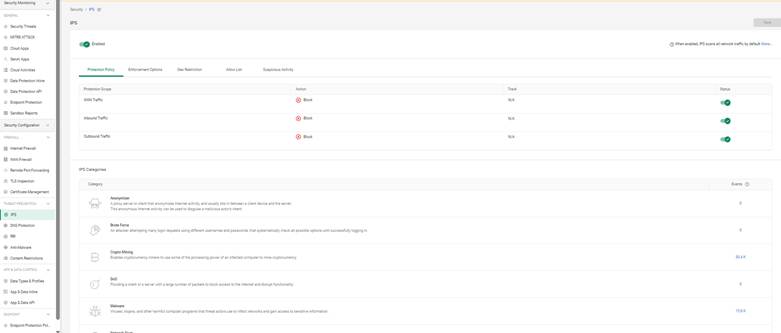
Cato’s IPS engine runs at the network layer and is powered by both signature-based and behavioral detection.
To enable IPS:
You can also review threat severity and categories detected historically.
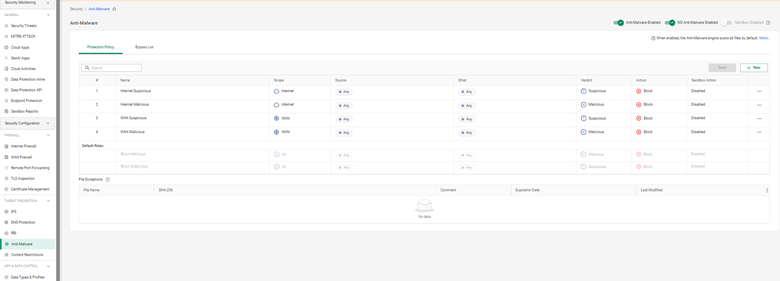
Cato’s Anti-Malware engine inspects downloaded files and executables in real time. It uses both known threat signatures and zero-day detection via machine learning models.
Steps to enable:
Anti-Malware logs are viewable under Monitoring > Security Events.
Also Read: Strategies to Eliminate Network Downtime with Cato SASE’s Reliable Global Backbone
TLS (SSL) Inspection allows Cato to decrypt and inspect HTTPS traffic to detect threats hidden inside encrypted sessions.
To enable TLS Inspection:
⚠️ TLS inspection introduces overhead and may impact latency. It’s recommended to roll out in stages.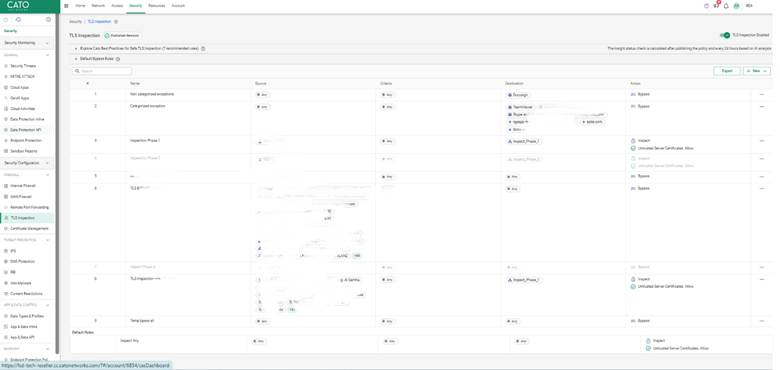
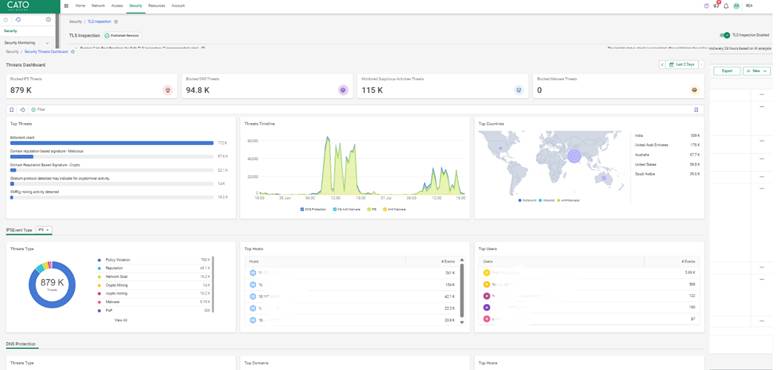
After enabling threat prevention, you can monitor detections under:
Use filters to sort events by source IP, severity, or blocked signature.
An enterprise with distributed branch offices started seeing spikes in CPU usage at multiple endpoints. After enabling TLS inspection and Anti-Malware selectively on file-sharing categories, they discovered embedded ransomware downloads in seemingly harmless zip files.
Using Cato’s logs, the IT team quickly isolated affected endpoints and blocked the application category globally.
Also Read: Beyond VPN Limitations: Why Cato SASE Is the Better Choice for Remote Workforces
Threat prevention in Cato Networks is about more than just checking a box; it’s about creating a proactive defense that evolves with the threat. By leveraging the CMA, you can secure your global workforce without the complexity of managing multiple point products. We are dedicated to providing a security platform that is as agile as your business.
Book a call to reach our Cato SASE experts
No. You can scope TLS policies per site or category.
Only if you exclude their subnet or device identity from policies.
They’ll receive HTTPS warnings. Ensure your root cert is deployed via GPO or MDM.
They’re included in most standard Cato SASE subscriptions, but confirm with your sales rep.
Yes. Cato supports log forwarding via Syslog and REST API.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts